Categories
Tags
2025 Active-Directory Adobe ColdFusion Apache ASP DotNet Aug 2024 AWS B2R Binary Binary Hijacking Broken Access Control Burpsuite Caido Clickjacking Cloud Crackmes Cryptography CVE-2009-3548 CVE-2014-1812 CVE-2024-28397 CVE-2024-32019 CVE-2025-24893 Debugging Easy Email-Forensics Engineering Eternal Blue Exploitation Feb File-upload-vulnerabilities Flare-On Forensics Free FTP HACK HAVOC HTB HttpFileServer IDA IIS impacket Industrial-Control-System Information Disclosure js2py KPMG Linux Malware-Analysis Metasploit Microsoft-Access-database Misc Mobile MS10-092 MS14-025 MS16-032 MS17-010 npbackup nsudo Oct 2024 Operational-Technology OSINT Path-Injection Path-Traversal-To-RCE PMA_Labs Programming PwnedLabs RCE Retired Reverse Reverse Engineering Reversing Runas-Abuse S3 S3-to-AccountID Scripting Sherlock SMB Snyk SSRF Steg Telnet Tomcat VIP Web Windows x64dbg xwiki
244 words
1 minutes
Crackme - TeRrArIsT's Easy, but interesting for novice August 2025
Challenge Info
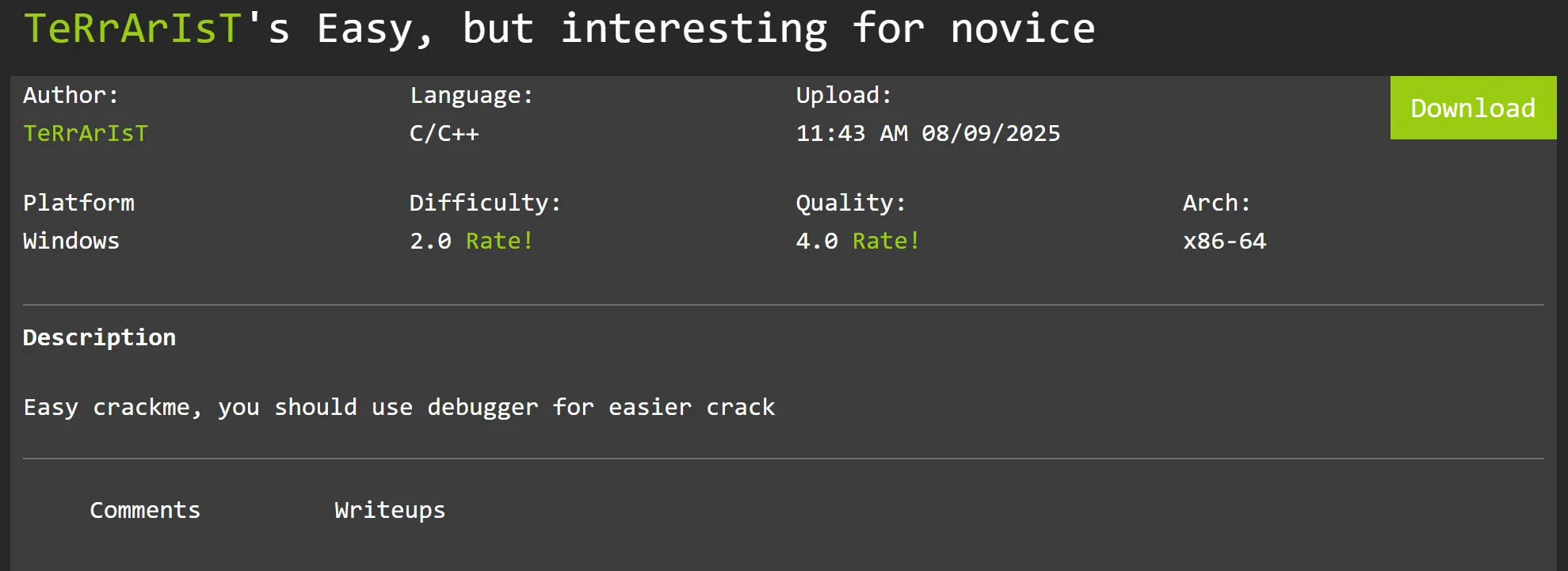
File Info
- This is a 64-bit executable file.
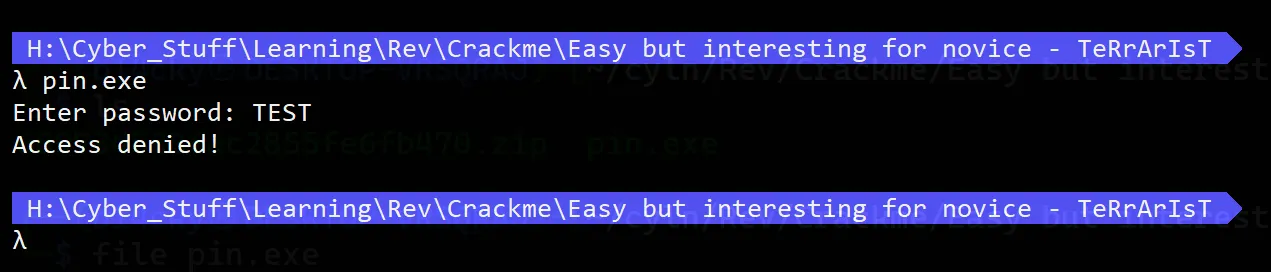
Testing Inputs
- I started by testing with the string
"TEST"as input. - The program responded with Access Denied, which suggests it’s validating the input against a different, predefined string. We can clearly observe this in IDA.
- IDA View:
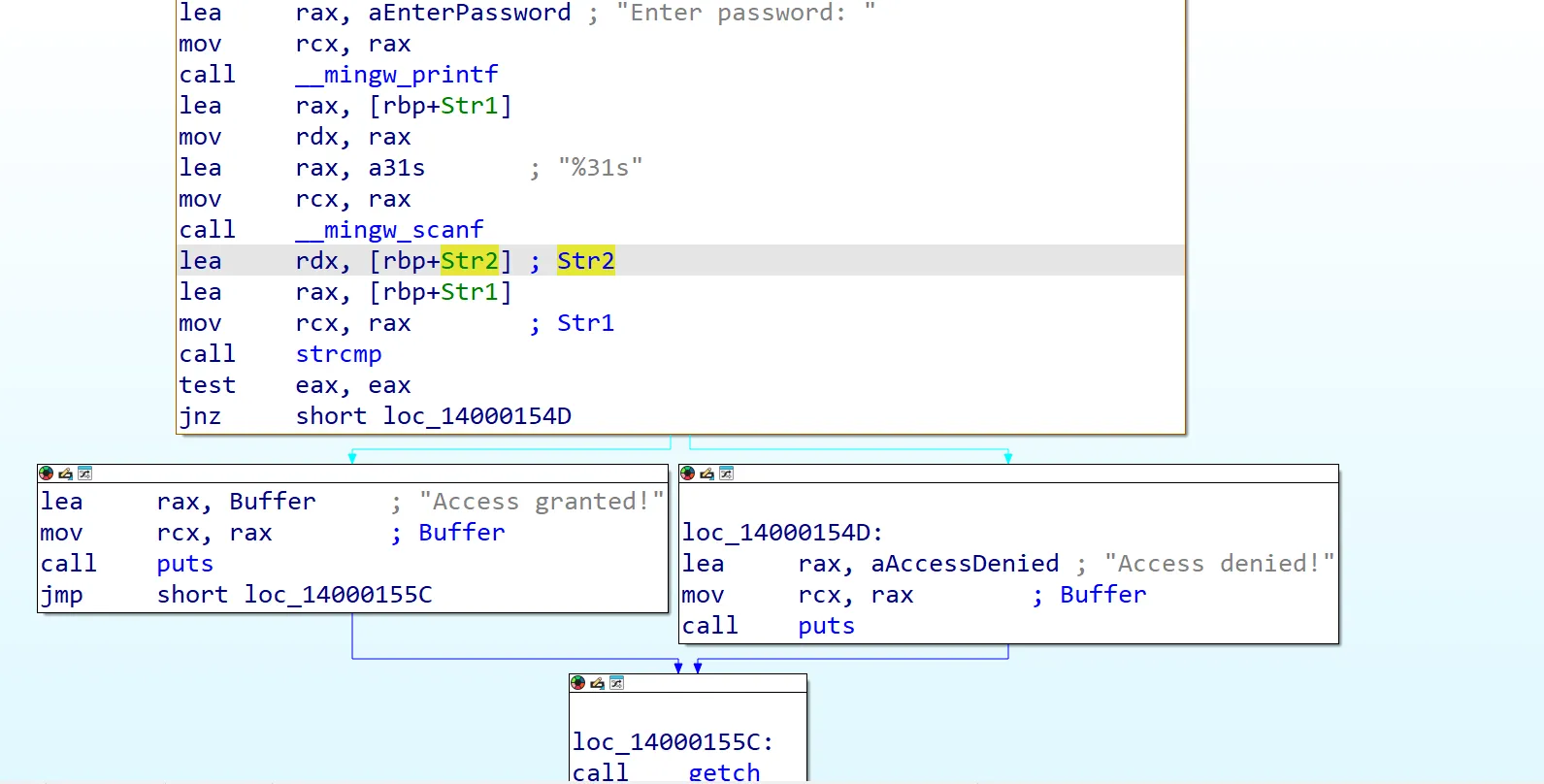
- Pseudocode (IDA-generated):
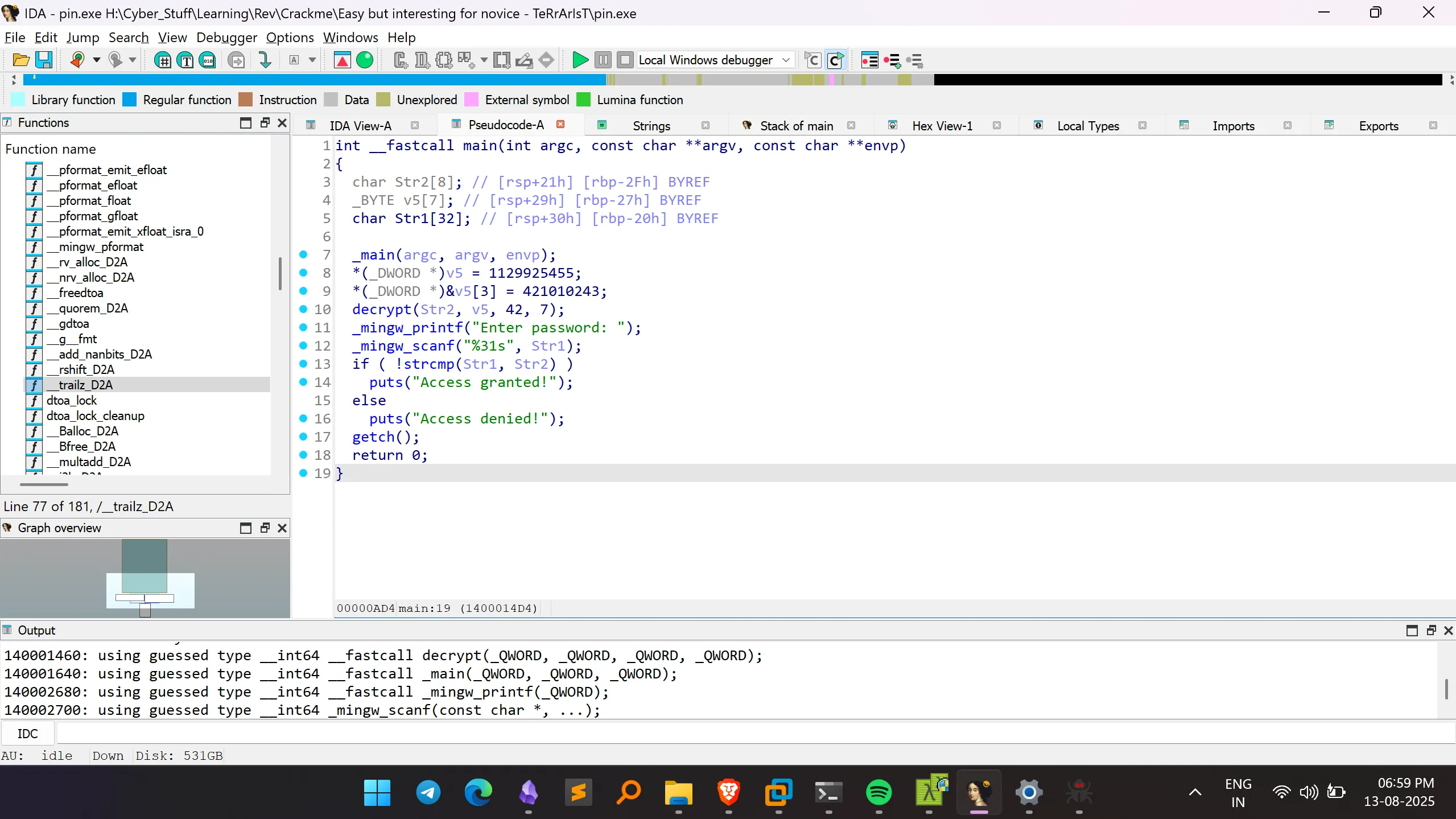
int __fastcall main(int argc, const char **argv, const char **envp)
{
char Str2[8]; // [rsp+21h] [rbp-2Fh] BYREF
_BYTE v5[7]; // [rsp+29h] [rbp-27h] BYREF
char Str1[32]; // [rsp+30h] [rbp-20h] BYREF
_main(argc, argv, envp);
*(_DWORD *)v5 = 1129925455;
*(_DWORD *)&v5[3] = 421010243;
decrypt(Str2, v5, 42, 7);
_mingw_printf("Enter password: ");
_mingw_scanf("%31s", Str1);
if ( !strcmp(Str1, Str2) )
puts("Access granted!");
else
puts("Access denied!");
getch();
return 0;
}
- To investigate further, I used x64dbg and began searching for static strings that could help in pinpointing the password verification logic.
Examples include:"Access granted!""Access denied!"- References to
strcmp - Other suspicious instructions that might hint at password handling.
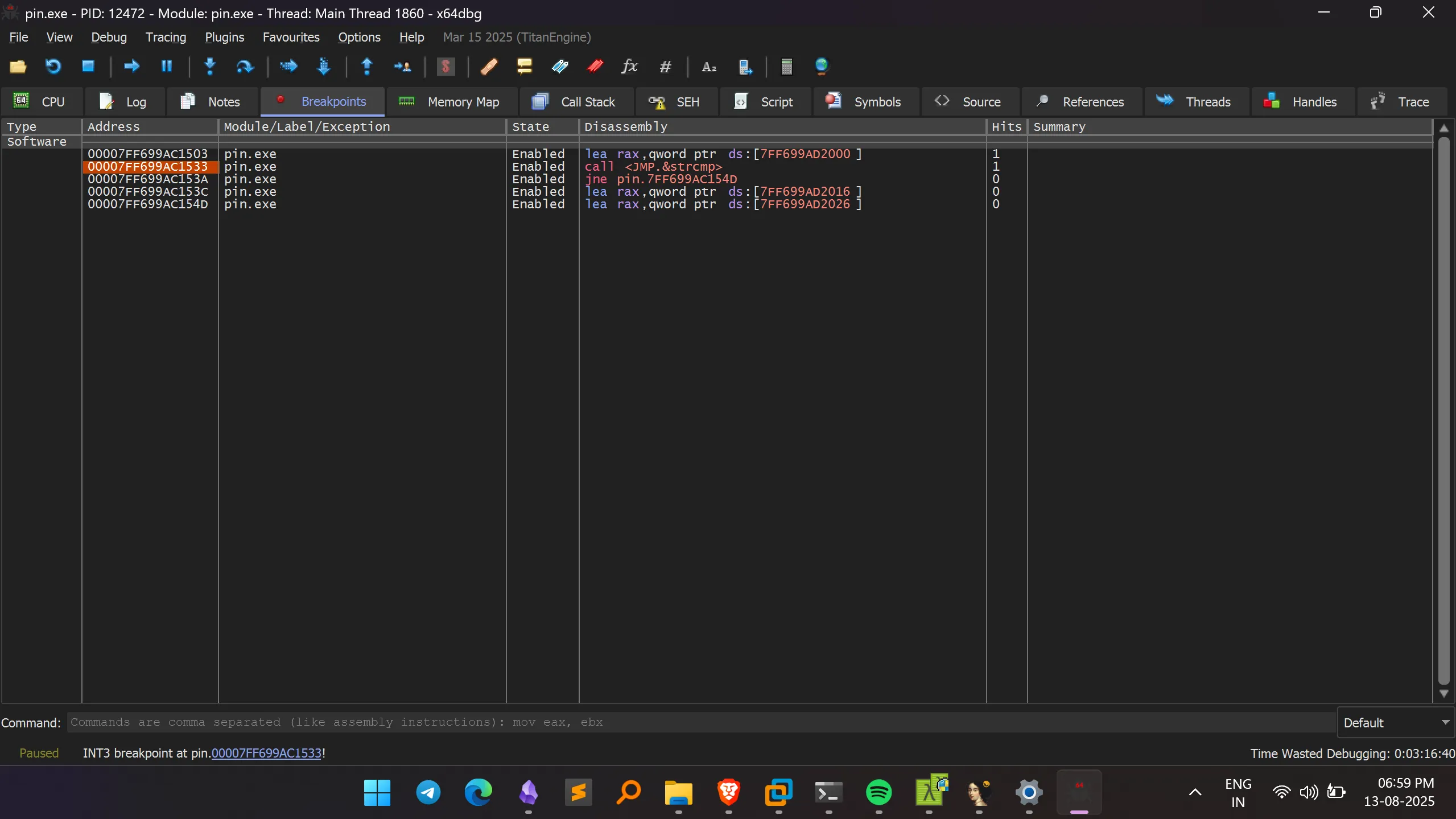
- After setting breakpoints, I ran the program until it hit the relevant instruction.
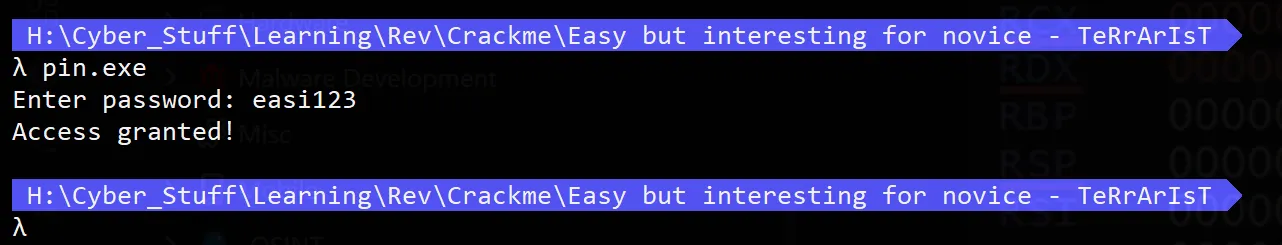
- At this point, I entered the test input string:
JEEL.
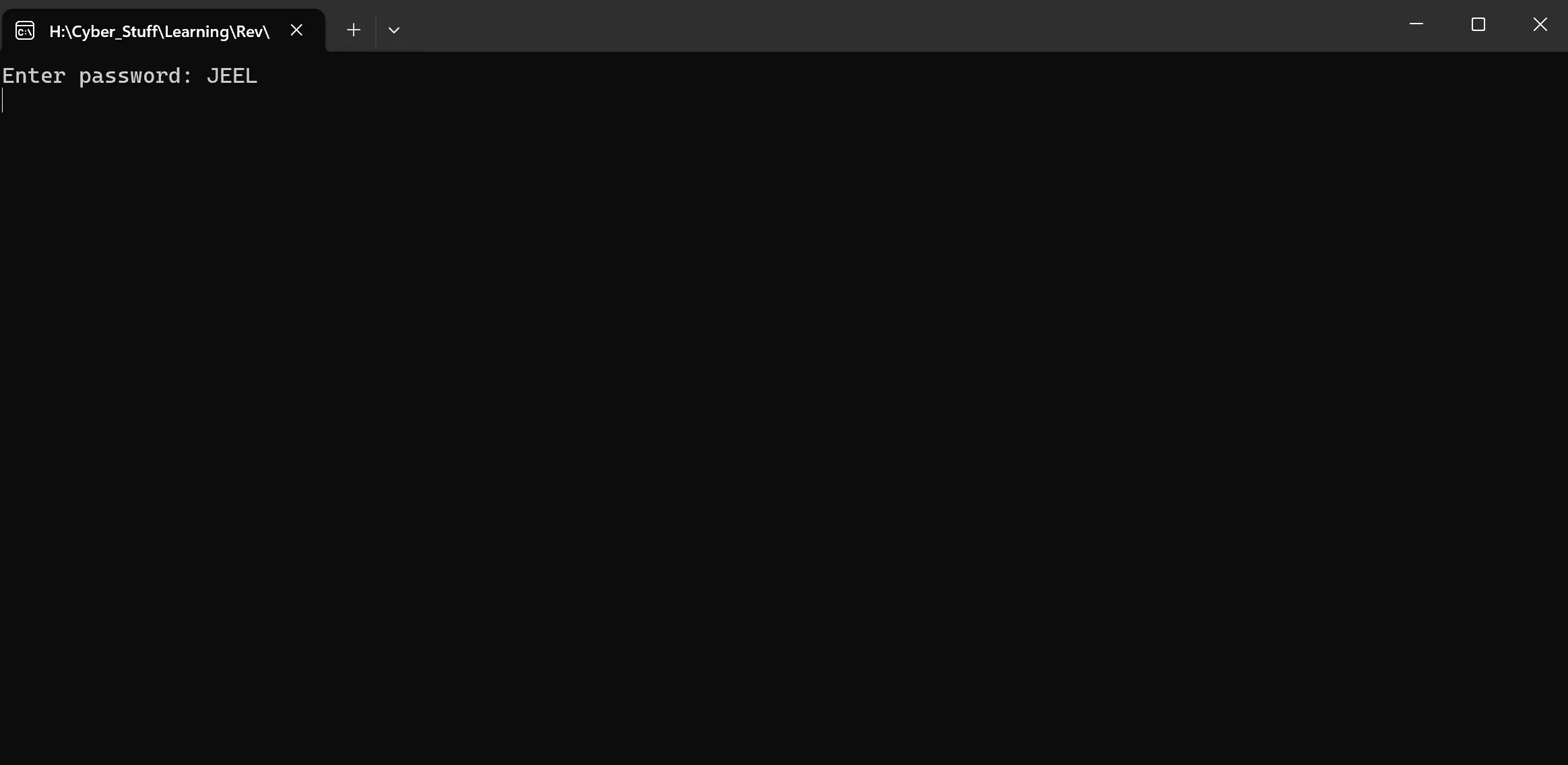
- I then continued execution to the section where the string comparison occurs.
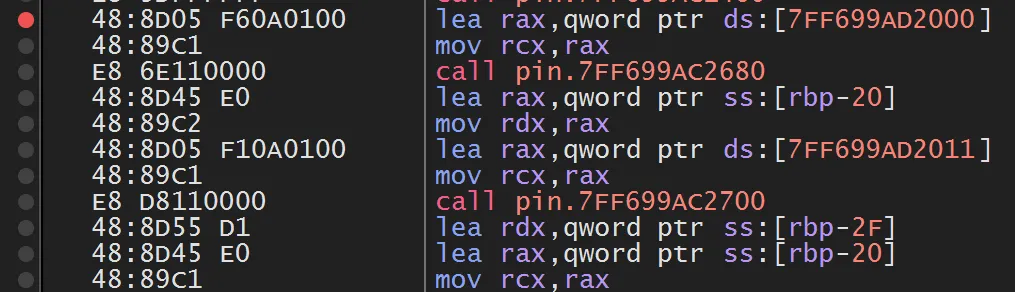
These instructions are particularly interesting because they load the two strings into registers before thestrcmpcall:- First string →
RDX(the user’s input) - Second string →
RAX(the stored, correct password)
- First string →
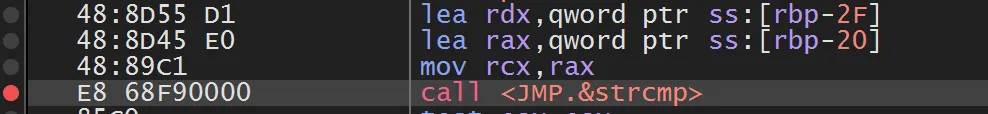
strcmpCall Instruction:
![]()
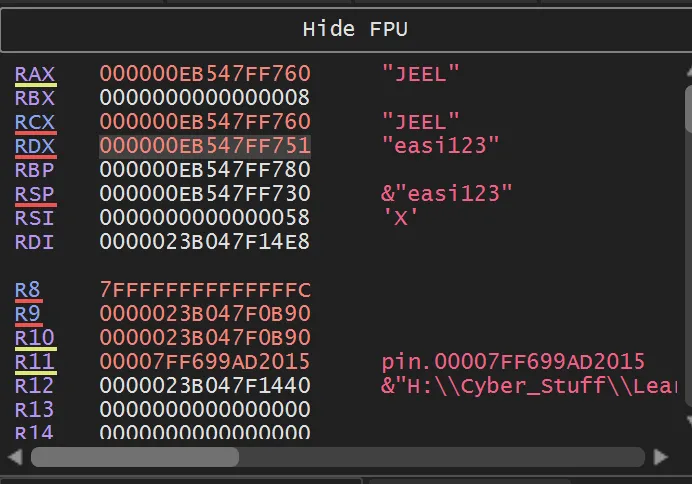
- Register values at the moment of comparison:
- User’s input:
"JEEL" - Stored password:
"easi123"— which is the correct key/flag for the program.
- User’s input:
Crackme - TeRrArIsT's Easy, but interesting for novice August 2025
https://b14cky.github.io/posts/crackme---terrarists-easy-but-interesting-for-novice/writeup/
