KPMG CTF
Welcome
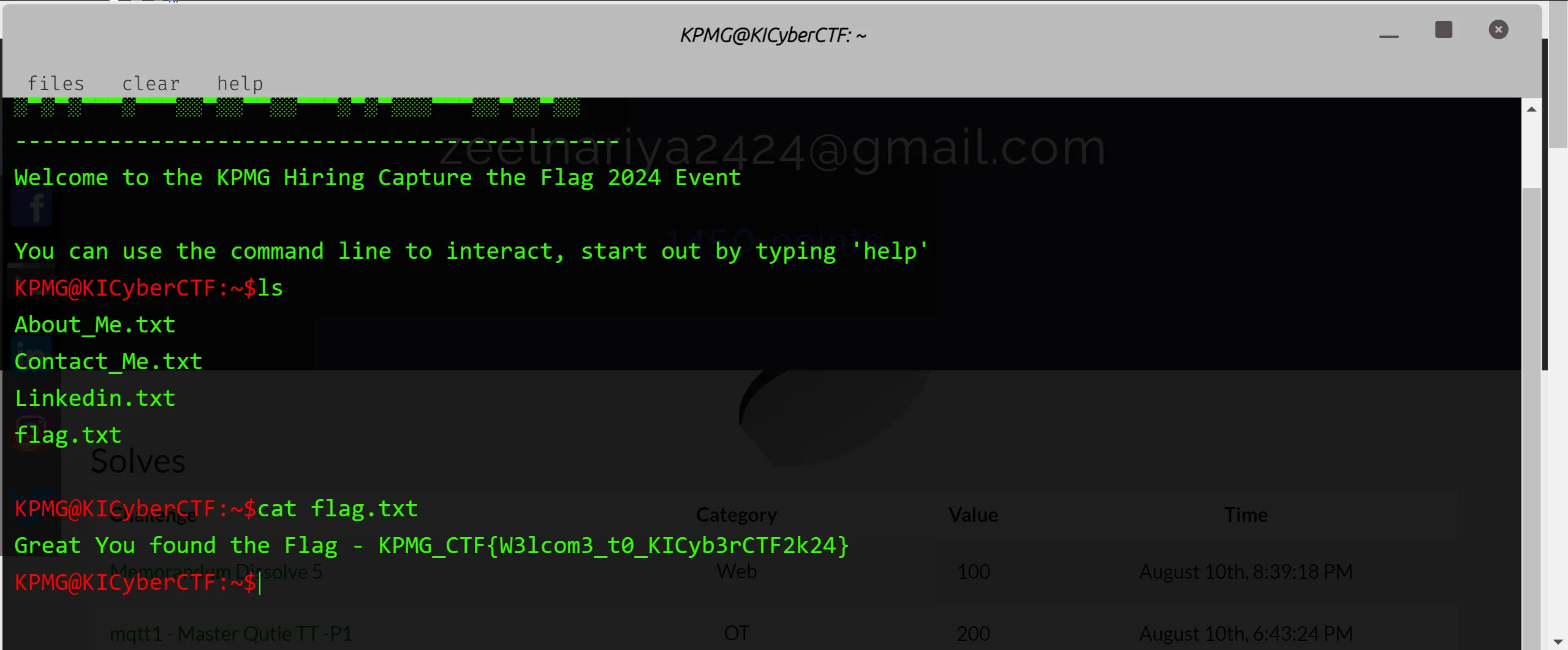
- We can directly cat the flag file from the website terminal,
Cloud
Presign Rains
- Here, after completing the cloud challenge, I was excited to solve this challenge, but here we got a website link.

- From the website, there is no hint related to flag, so I looked at the source code:
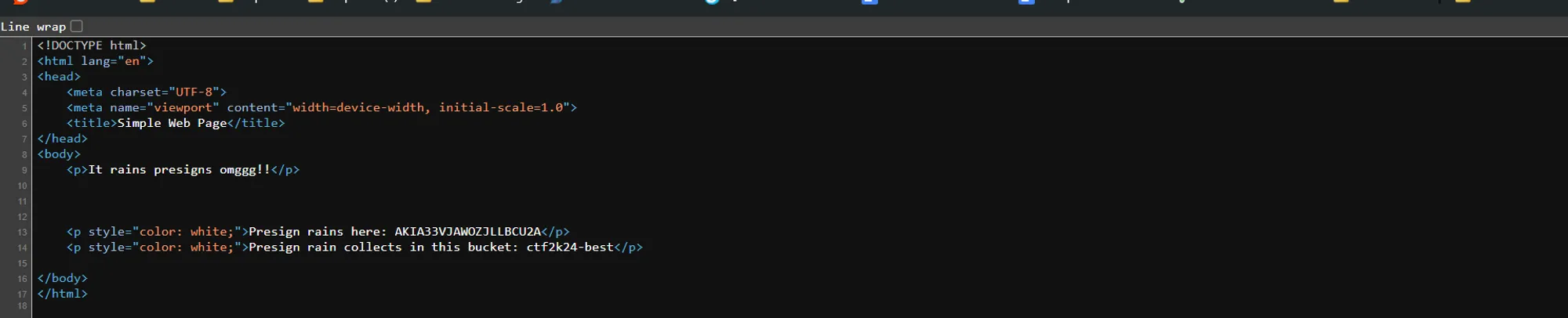
- Here we got the access key and bucket:
access key → AKIA33VJAWOZJLLBCU2A bucket: ctf2k24-best
- First, I thought of using AWS cli, but it also needs a secret key and region. So I tried reconnaissance further, and it led to robots.
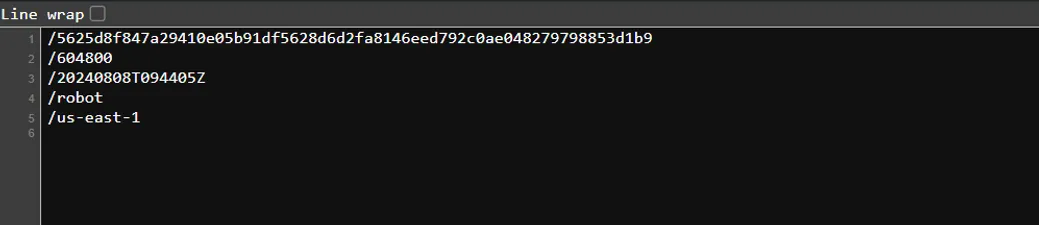
- Here we got many things. I thought there would be credentials in this directory, but these were the credentials. the robot directory:
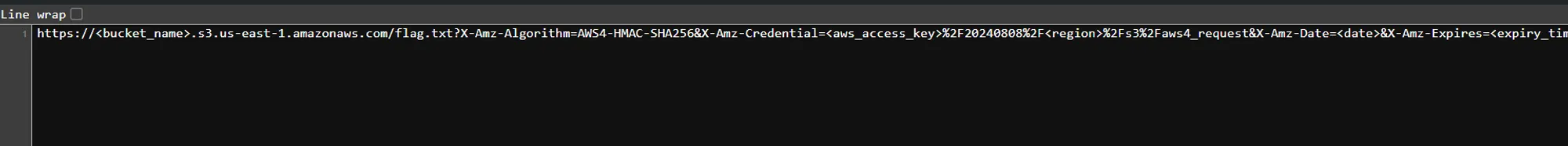
- Link :- [
https://<bucket-name>.s3.us-east-1.amazonaws.com/flag.txt?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=<aws access key>%2F20240808%2F<region>%2Fs3%2Faws4_request&X-Amz-Date=<Date>&X-Amz-Expires=<expire-time>&X-Amz-SignedHeaders=host&X-Amz-Signature=](https://ctf2k24-best.s3.us-east-1.amazonaws.com/flag.txt?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIA33VJAWOZJLLBCU2A%2F20240808%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240808T094405Z&X-Amz-Expires=604800&X-Amz-SignedHeaders=host&X-Amz-Signature=5625d8f847a29410e05b91df5628d6d2fa8146eed792c0ae048279798853d1b9)<singature> - From this link, it was clear that the credential can be used here, and we will get the flag.
- Credential used here:
bucket -> ctf2k24-best
access key → AKIA33VJAWOZJLLBCU2A
Expires → 604800
date → 20240808T094405Z
region → us-east-1
signature → 5625d8f847a29410e05b91df5628d6d2fa8146eed792c0ae048279798853d1b9
- Update Link :-
https://ctf2k24-best.s3.us-east-1.amazonaws.com/flag.txt?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIA33VJAWOZJLLBCU2A%2F20240808%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20240808T094405Z&X-Amz-Expires=604800&X-Amz-SignedHeaders=host&X-Amz-Signature=5625d8f847a29410e05b91df5628d6d2fa8146eed792c0ae048279798853d1b9 - After visiting the link,
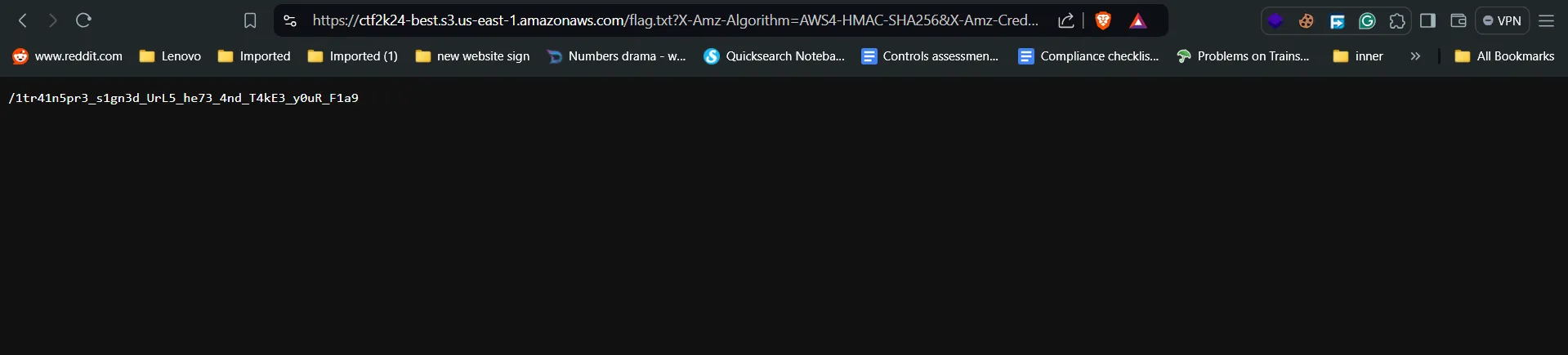
- Here, I thought that I had to use this directory in the link:
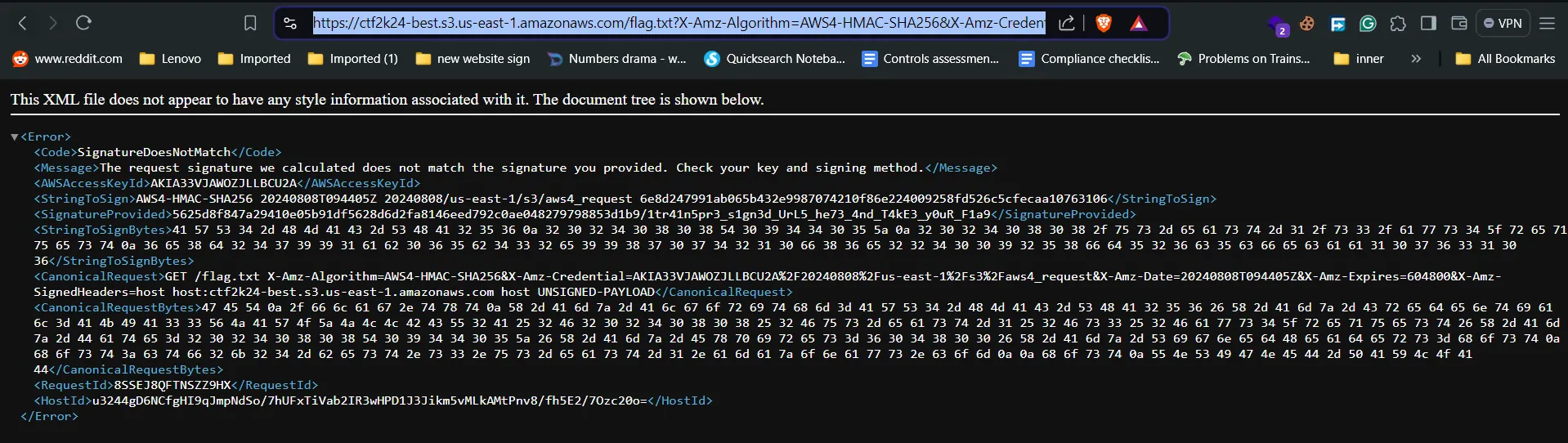
- I got an error, then I tried using this directory path on the link they have provided and i got the flag, 🫡
Data Valut Duel
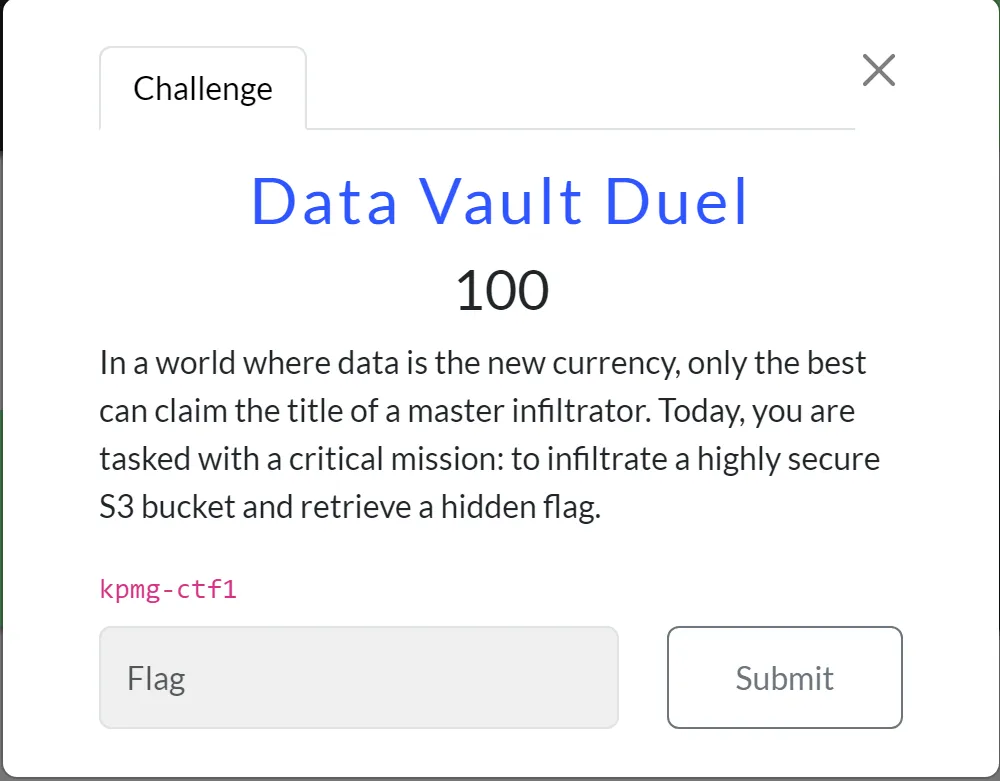
- From the description, I can see that the bucket name is given, which is publicly accessible, but I don’t have the AWS account, so I am not able to use AWS-cli directly, so I searched for this and got this AWS flag from searching.
aws s3 ls s3://kpmg-ctf1 --no-sign-reques
- From this command, I got some info about the bucket, like the available files in it, and one of the files is
rituognriteuonhbiorentgbvhuitrhoirtsnbiuort.txt.
- but without credentials, I can’t access this, so again, I tried to google how I could access it, and I found that using
wgetorcurl, we can directly access that S3 bucket.
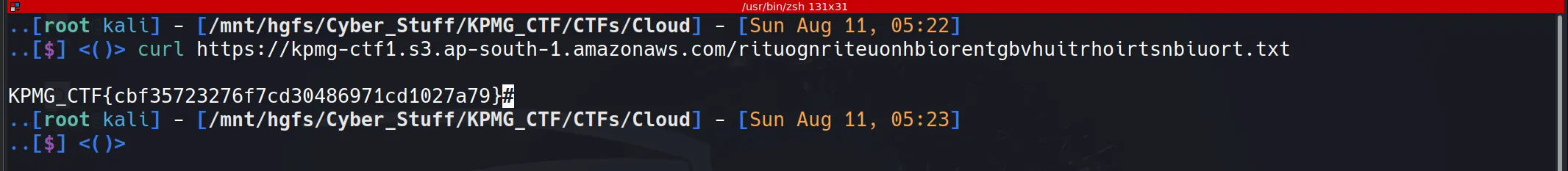
curl -O https://kpmg-ctf1.s3.ap-south-1.amazonaws.com/rituognriteuonhbiorentgbvhuitrhoirtsnbiuort.txt
- Using this command, I can curl the flag directly. hehe Piece of Cake 🫠
OSINT
Hacking The Admins
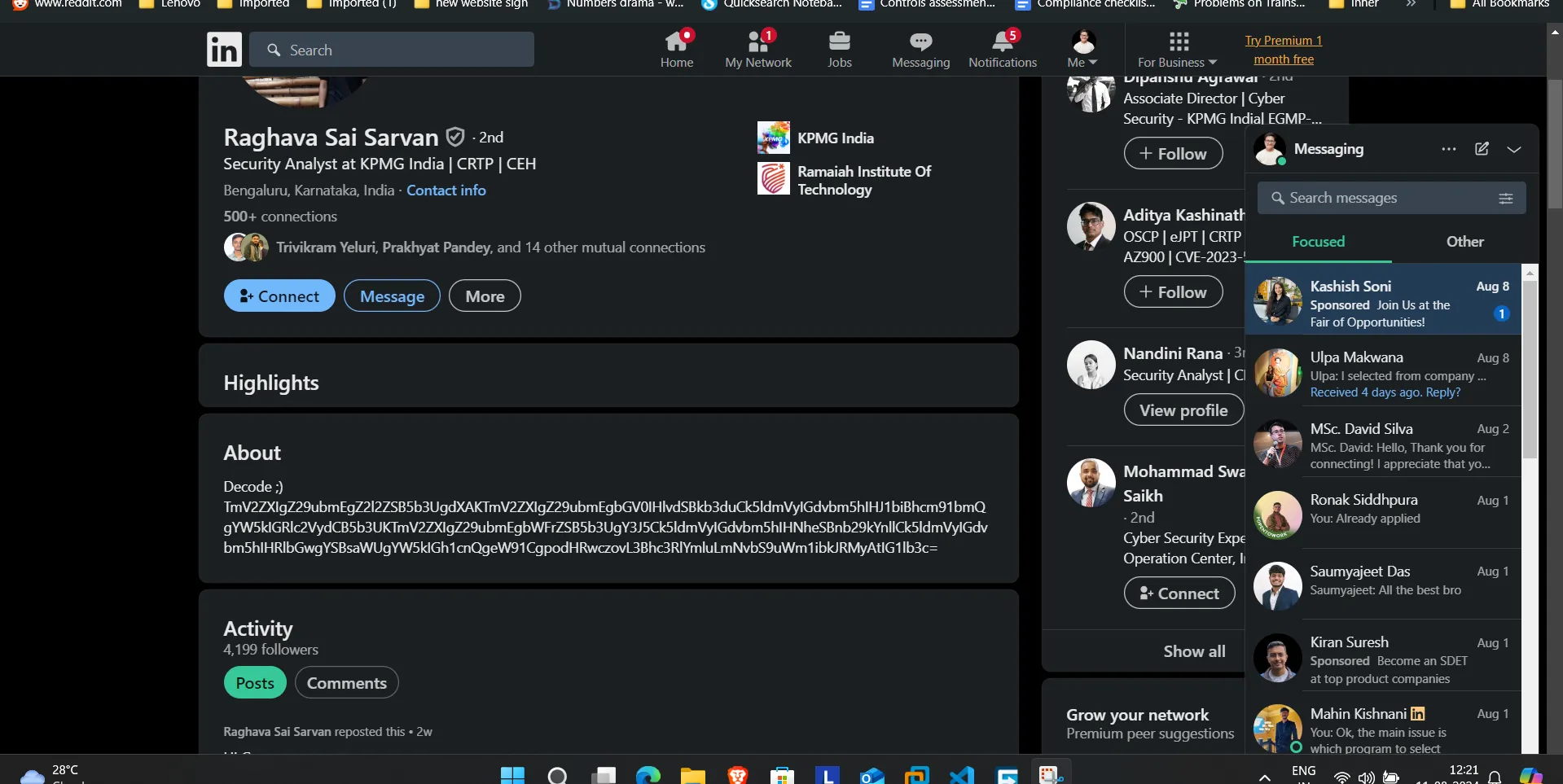
- From the text I guess that we have to search for the name
Raghava Sai Sarvaand I got a LinkedIn link:
- There is a hash in the description it is a base64 hash:
TmV2ZXlgZ29ubmEgZ212ZSB5b3UgdXAKTmV2ZXlgZ29ubmEgbGVOlHlvdSBkb3duCk51dmVylGdvbm5hlHJ1 bmQ gYW5klGRlc2VydCB5b3UKTmV2ZXlgZ29ubmEgbWFrZSB5b3UgY3J5Ck51dmVylGdvbm5hlHNheSBnb29kYnllCk51dmVylGdvbm5hlHRlbGwgYSBsaWUgYW5klGh 1 cnQgeW91 CgpodHRwczovBBhc3RlYmluLmNvbS9uWm1 ibkJRMyAtlG 1 lb3c=
- After decoding using CyberChef:
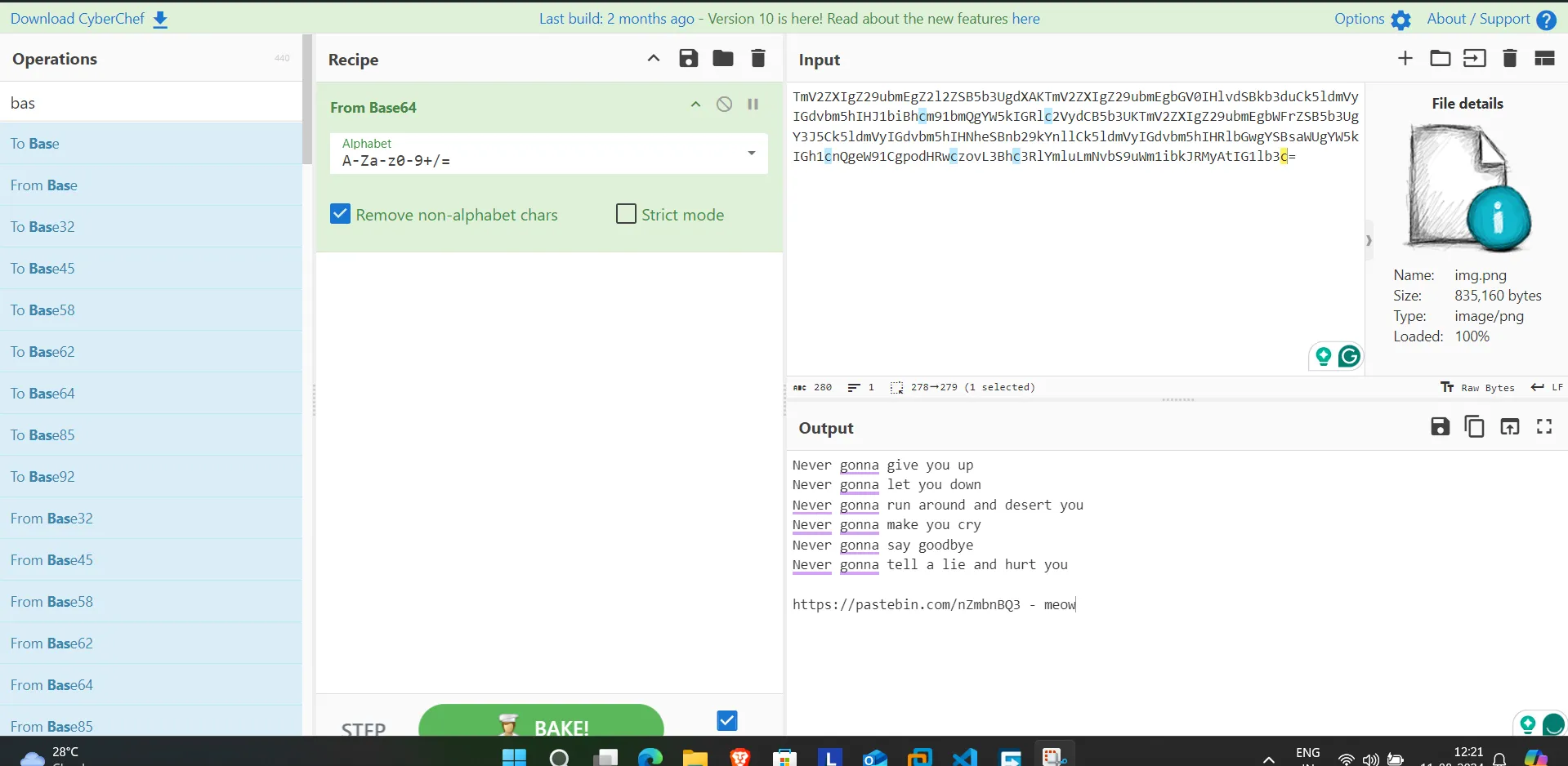
- I got a Pastebin link, let go and see what is there in the link:
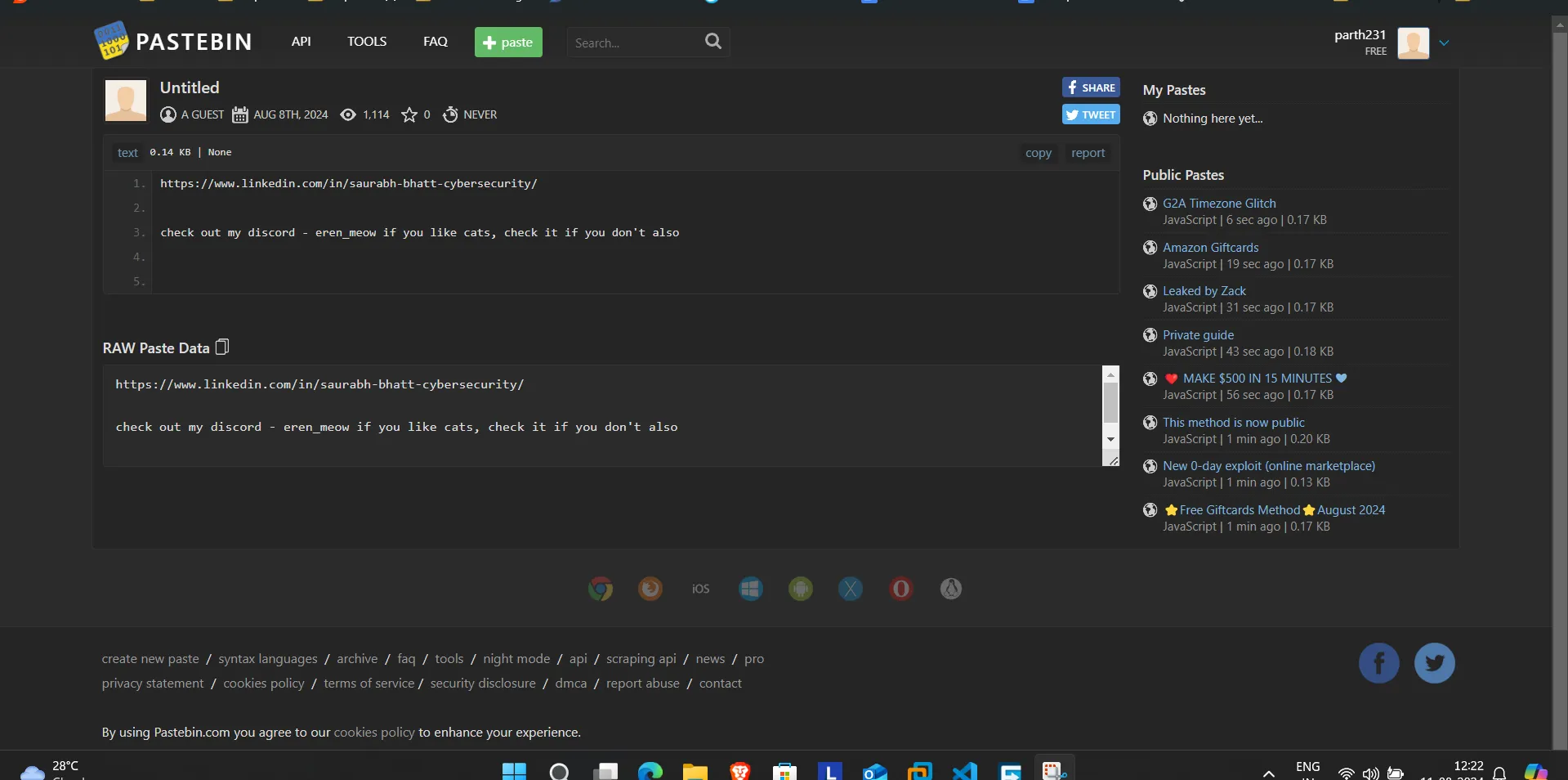
- From Previous Pastebin I got LinkedIn link and text that tells me to check the discord of
eren_meowaccount,
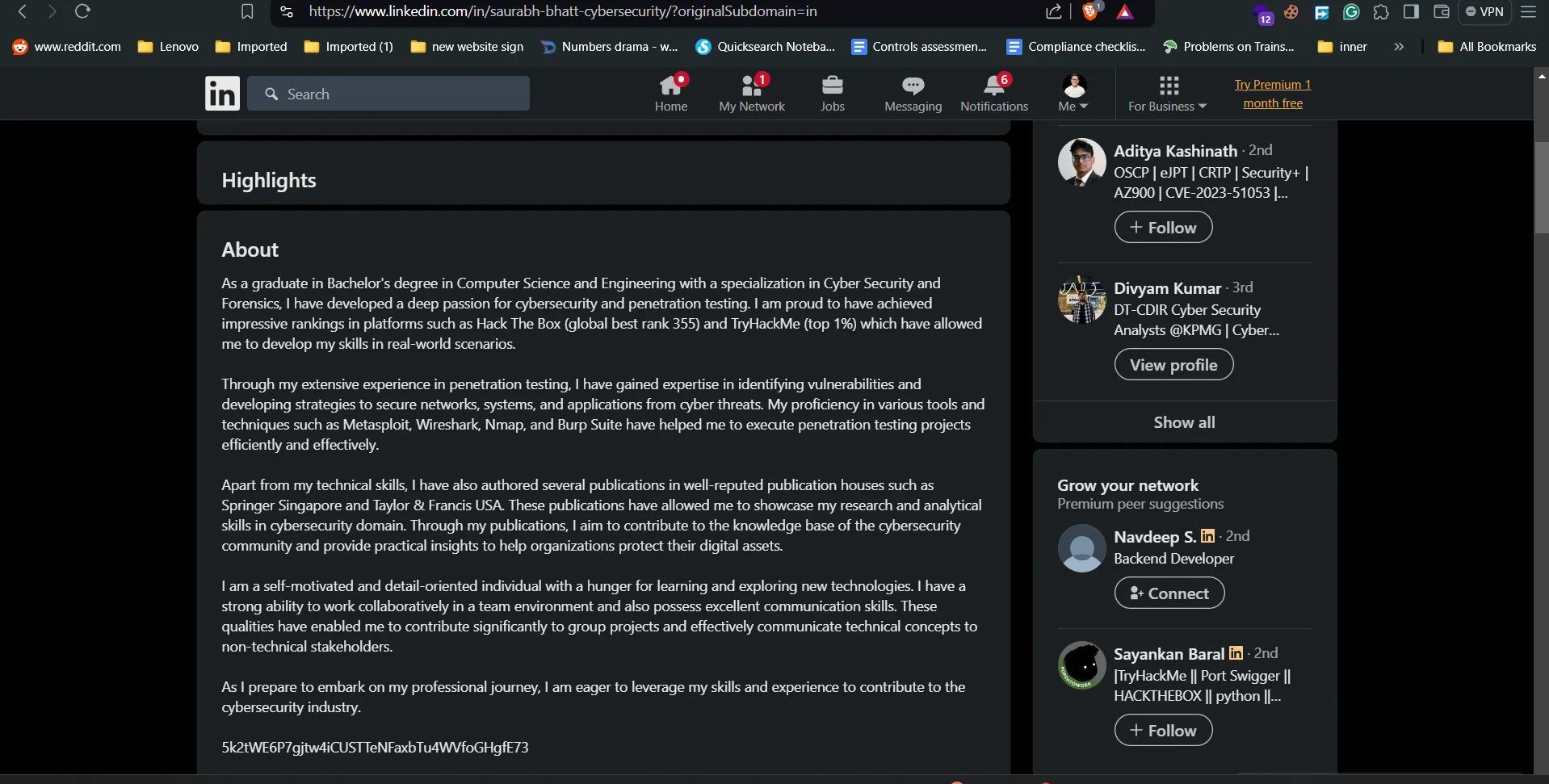
- Here we got a base58 hash:
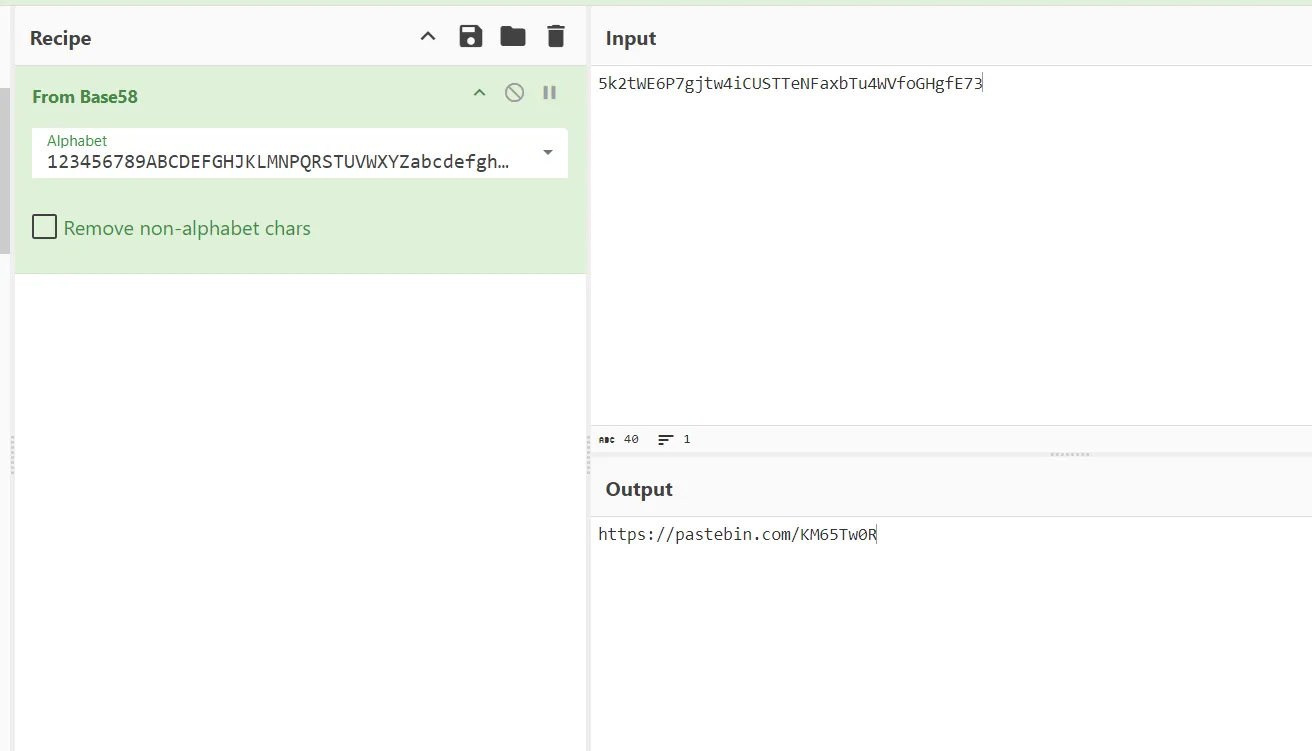
- let’s go to the link::
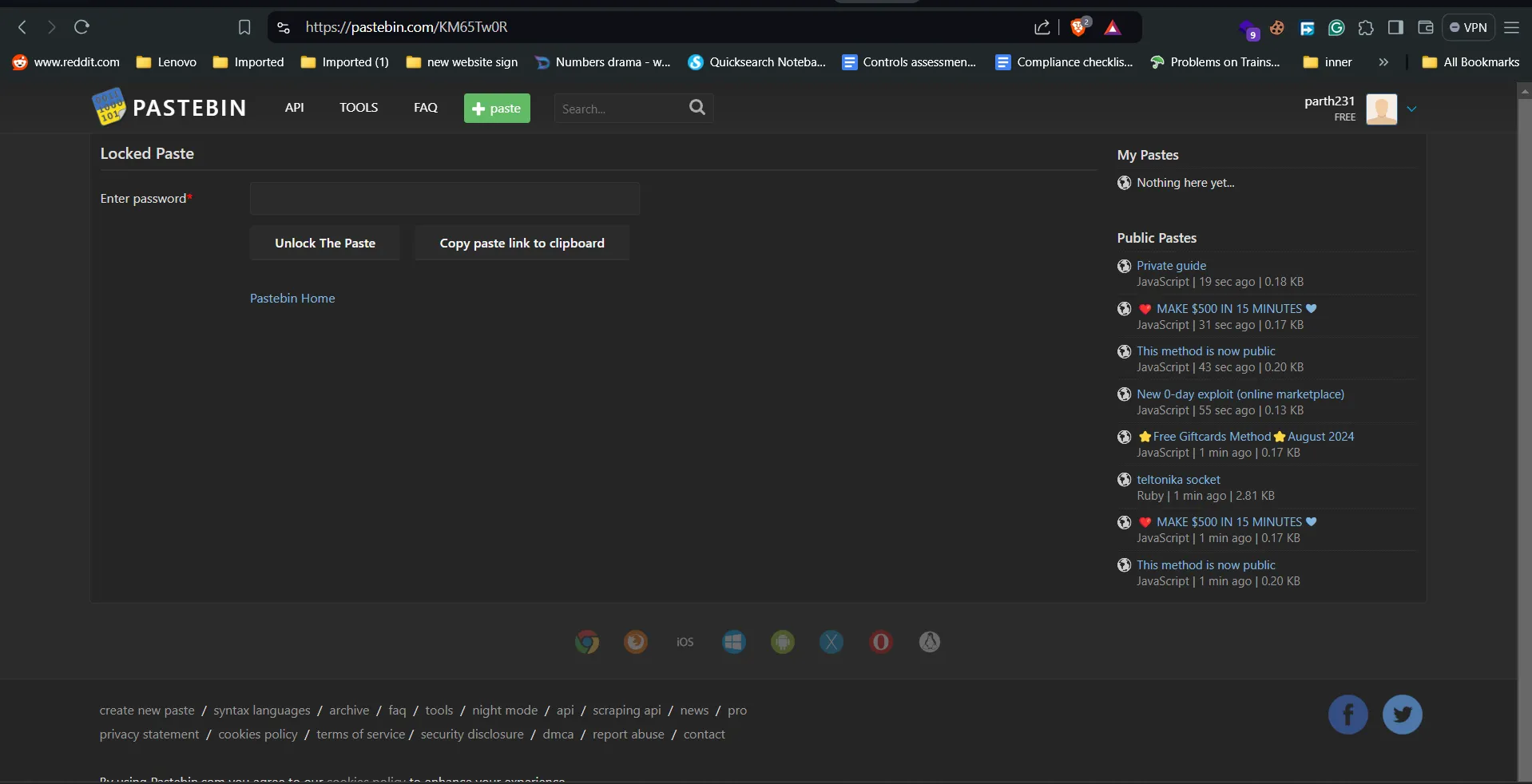
- It password Protected so check out the discord account mentioned previously
eren_meow, then let check the discord:
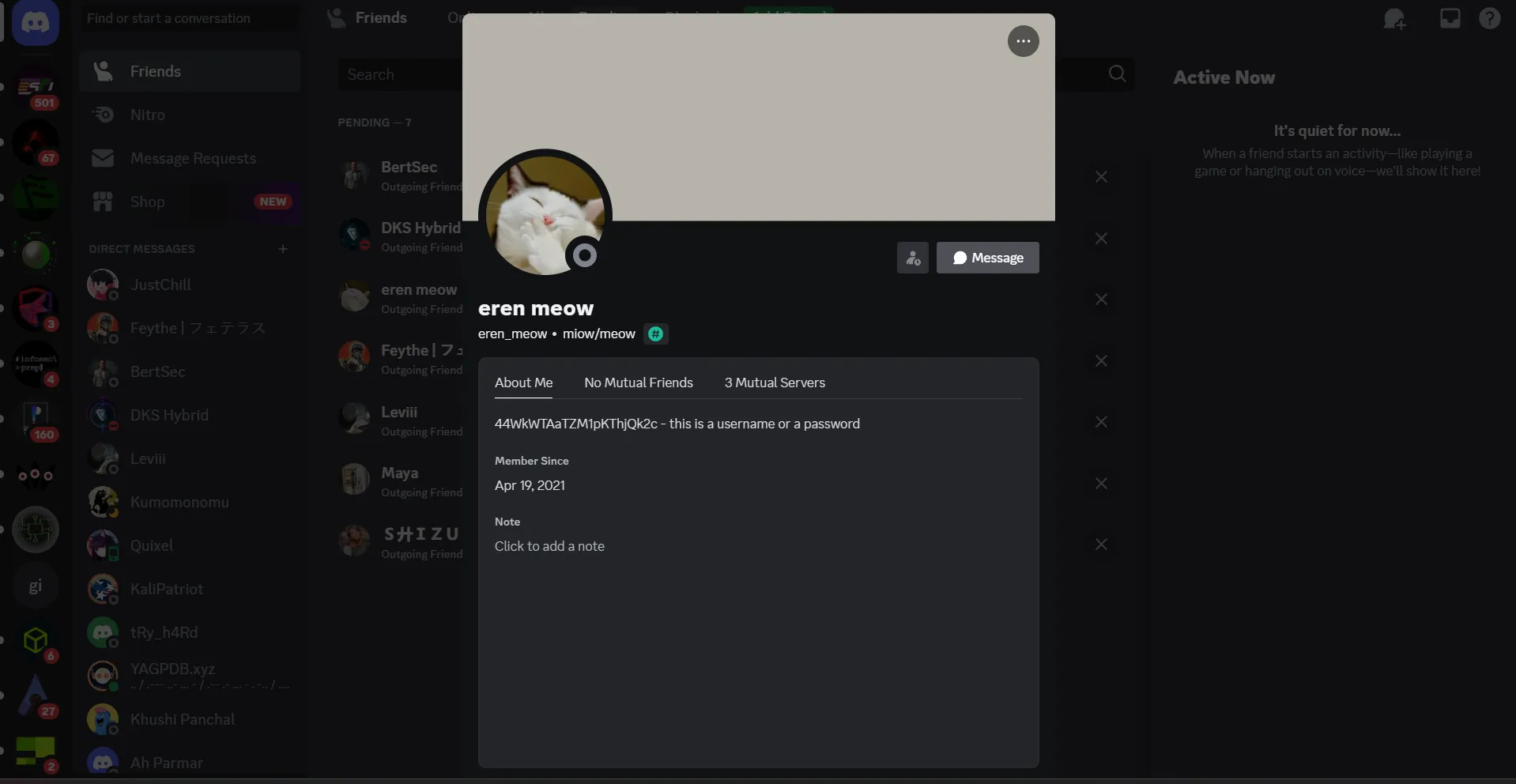
- here we got an hash that is Base58:
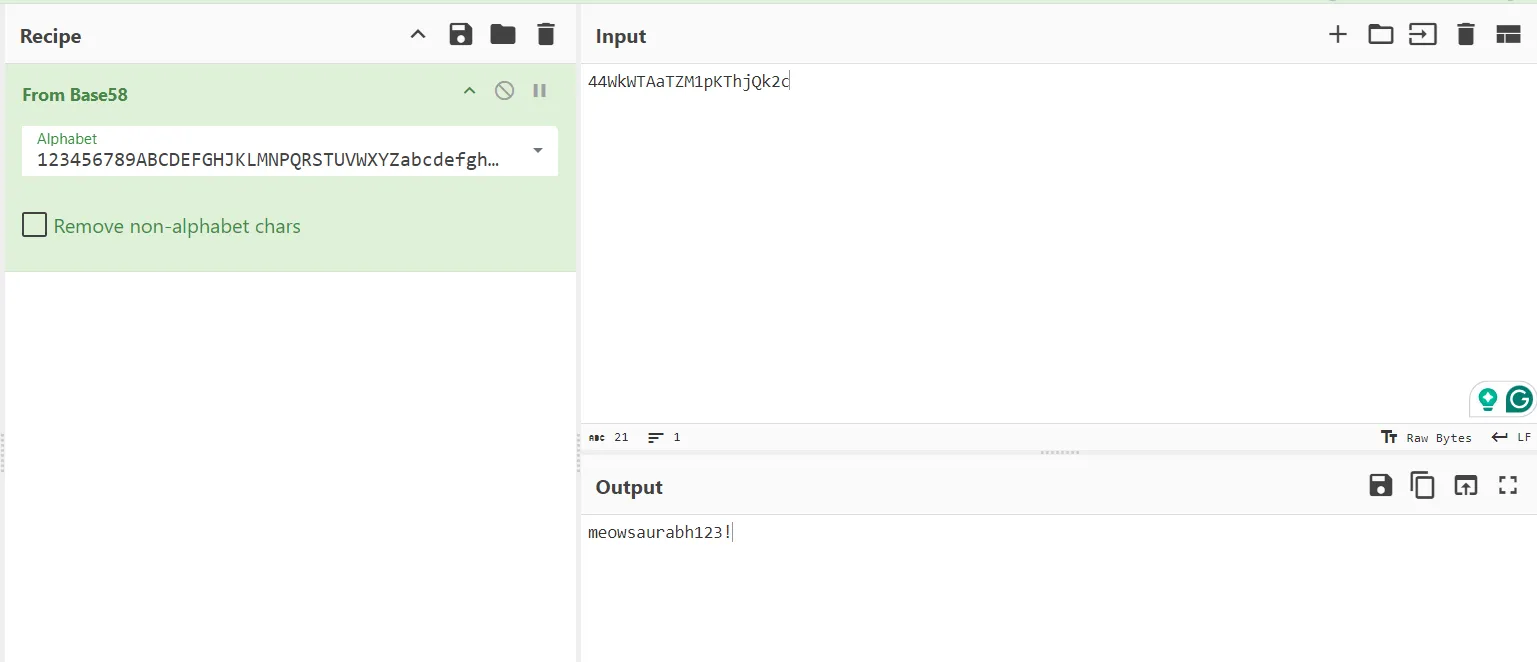
- Then We open the pastebin using
meowsaurabh123!password,
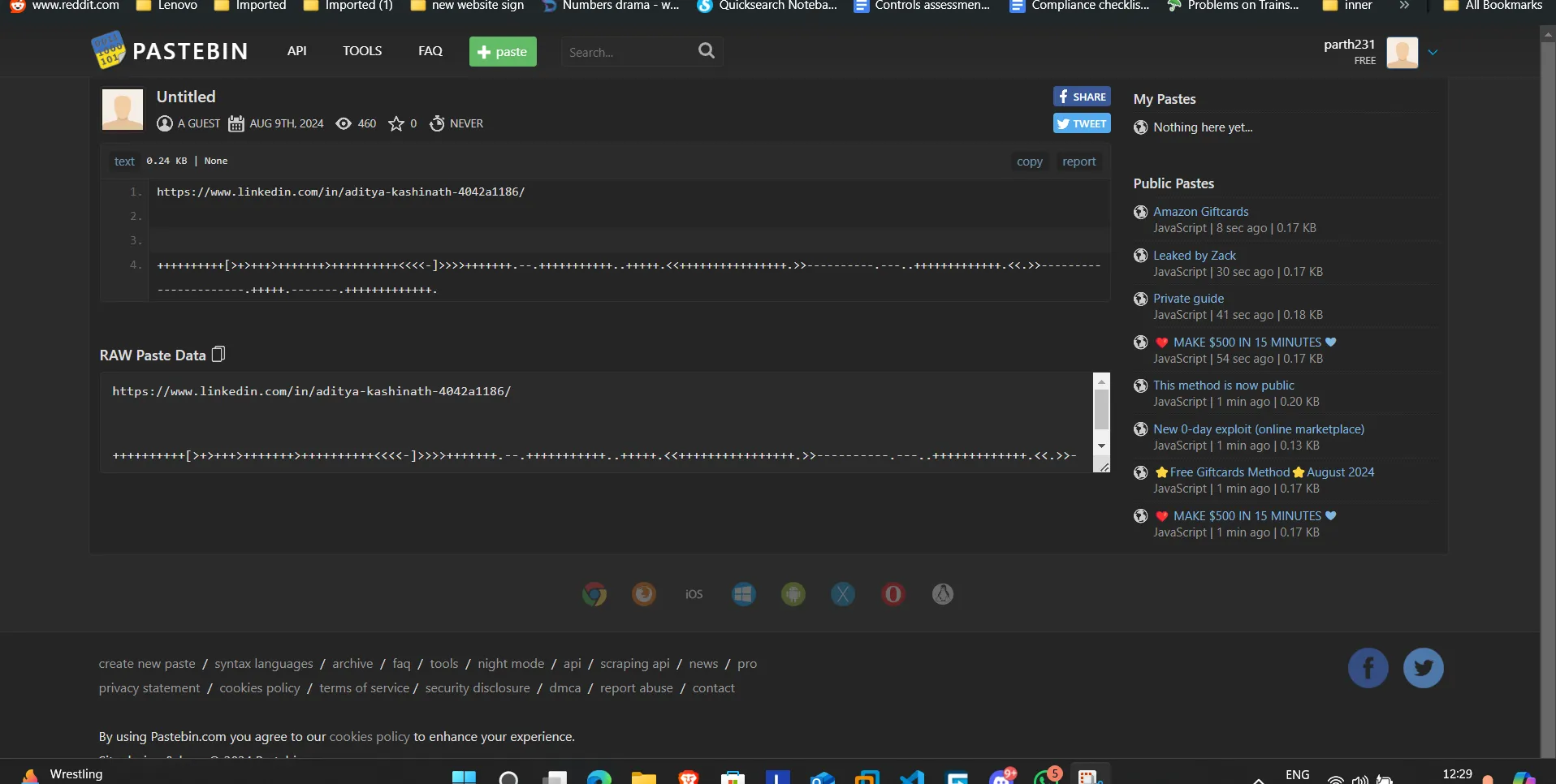
- Here again we got a LinkedIn link and a brainfuck code:
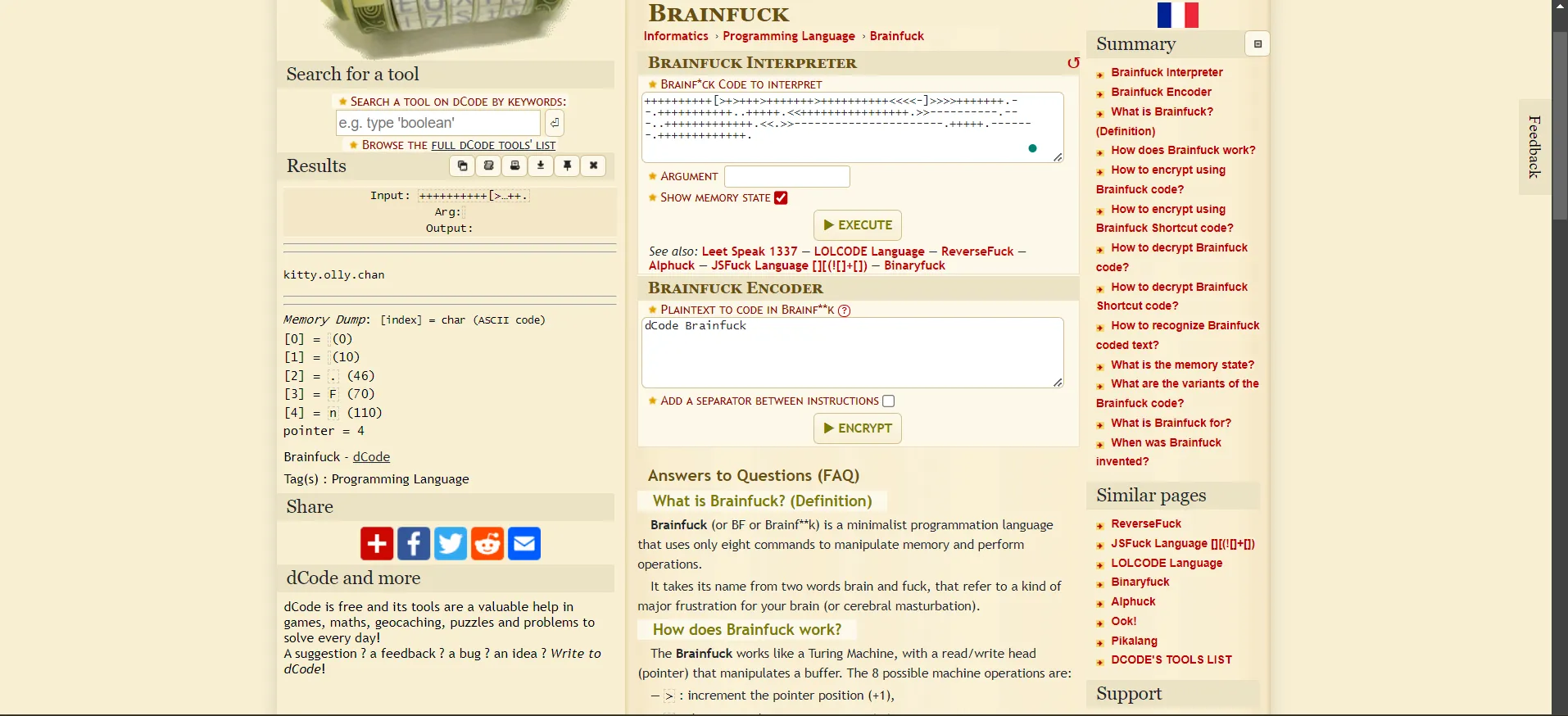
- In the LinkedIn they have given a
pastebin link:
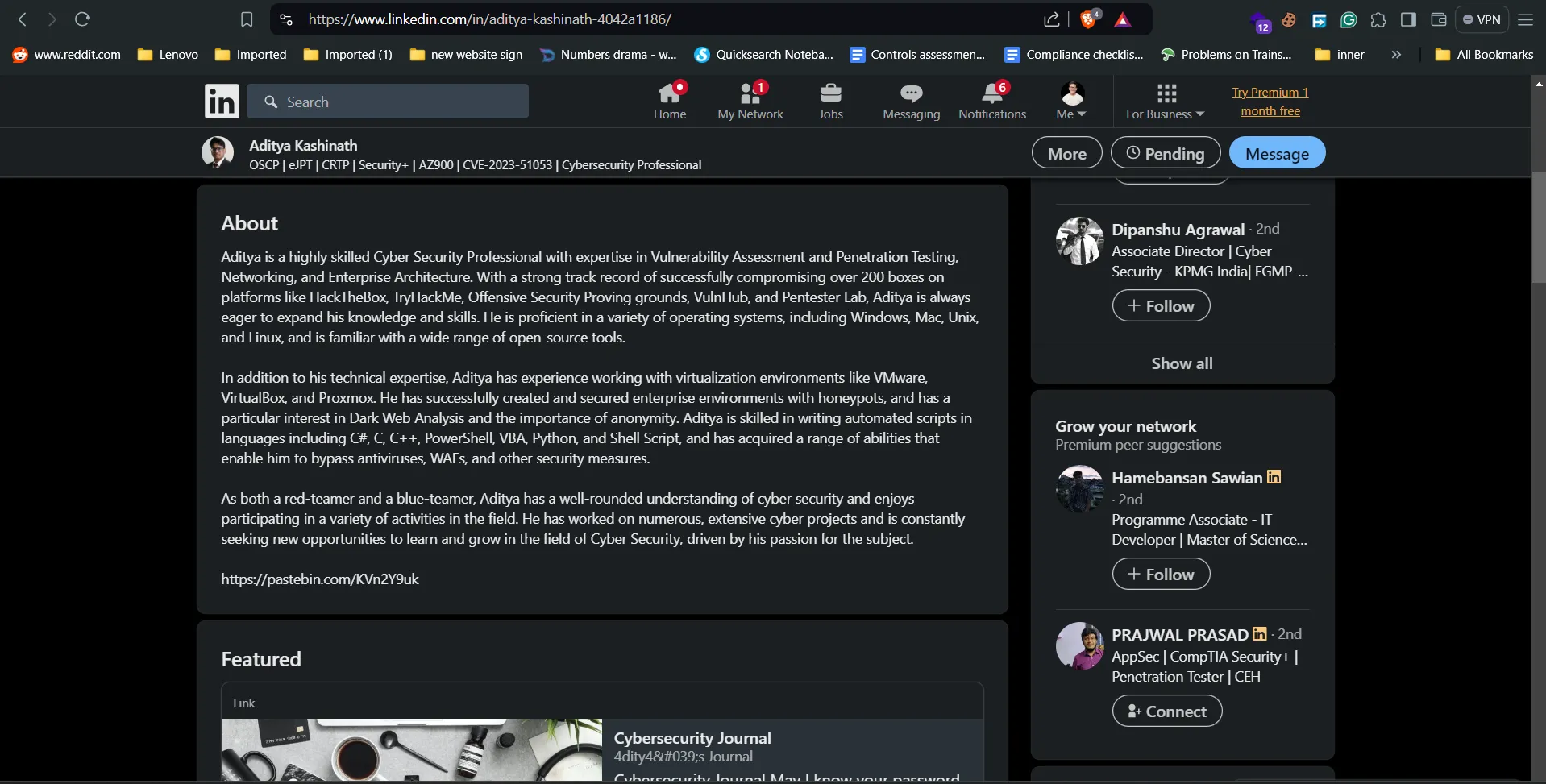
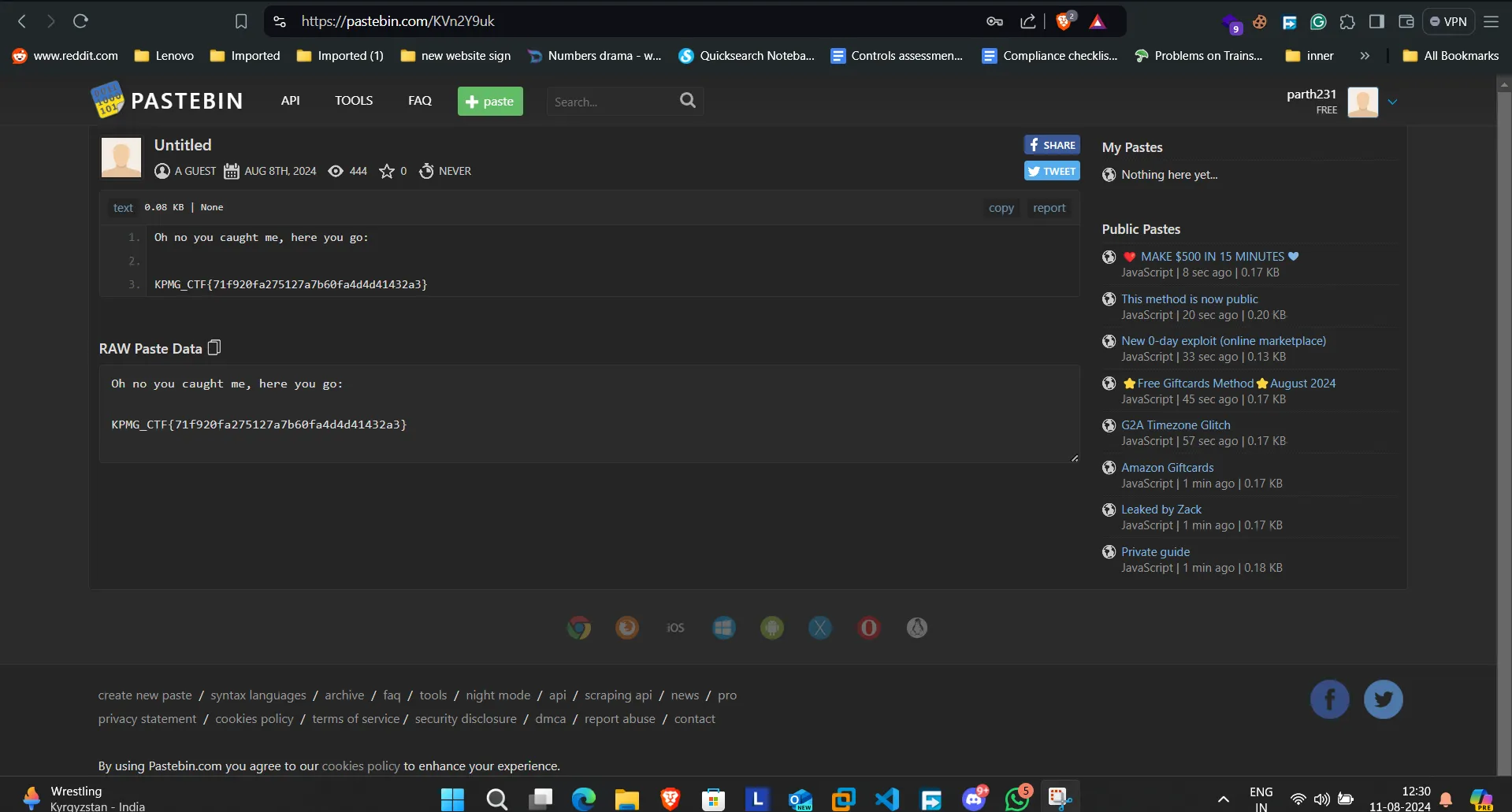
- I got the flag 🫡
Web
Memorandum Dissolve 5
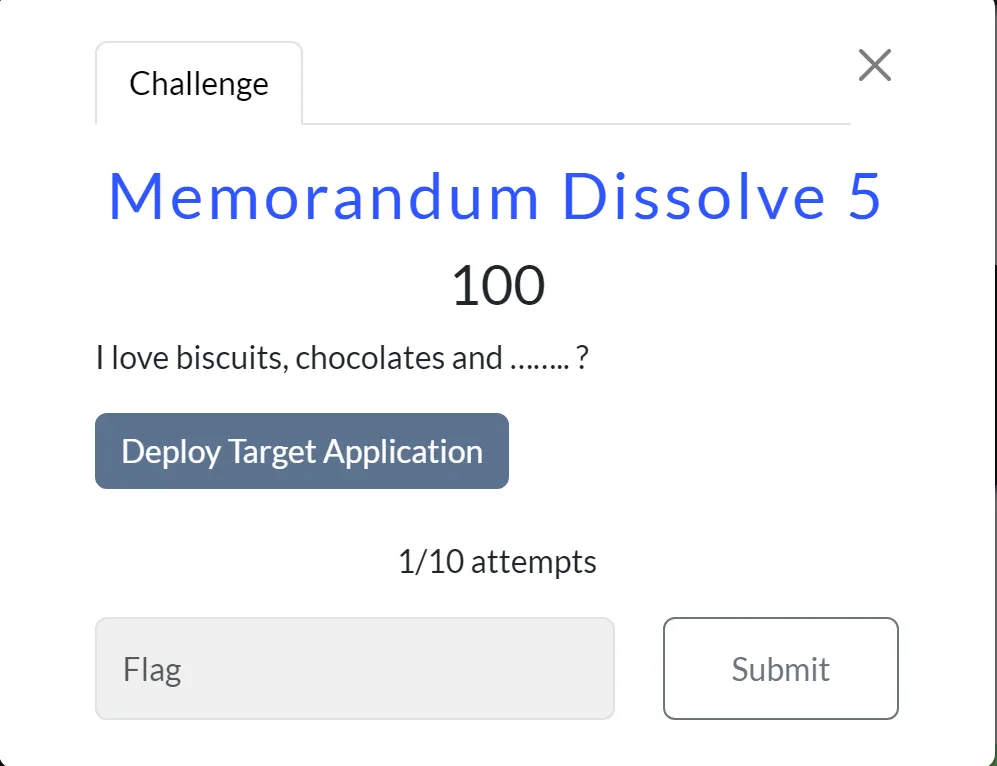
- In this Challenge I got an login page:
- As I first checked the source code of the page(which i think is a best practice), Here, they have provided the test username and password

- after logging in, I got a Welcome page, here I opened the inspect tool, for checking if there is any cookie is being used and i got the session cookie
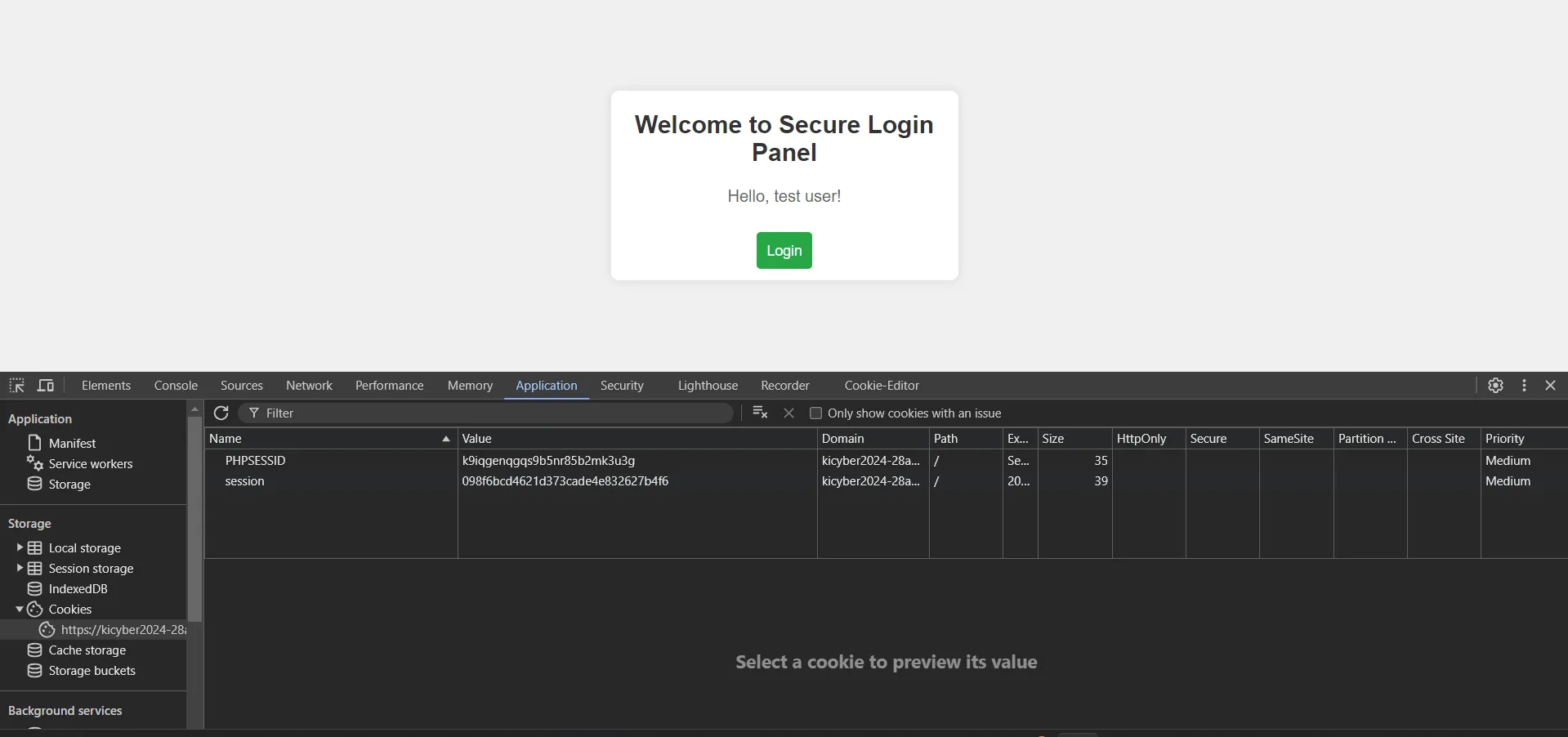
The session looked like it was an md5 hash so i tried to crack it using online decoder(https://md5hashing.net/hash/md5/2cb42f8734ea607eefed3b70af13bbd3):
MD5 hash:
test → 098f6bcd4621 d373cade4e832627b4f6As I suspected, the session key is the username so i tried using admin md5 hash as a session key
MD5 hash:
admin → 21232f297a57a5a743894aee4a801fc3
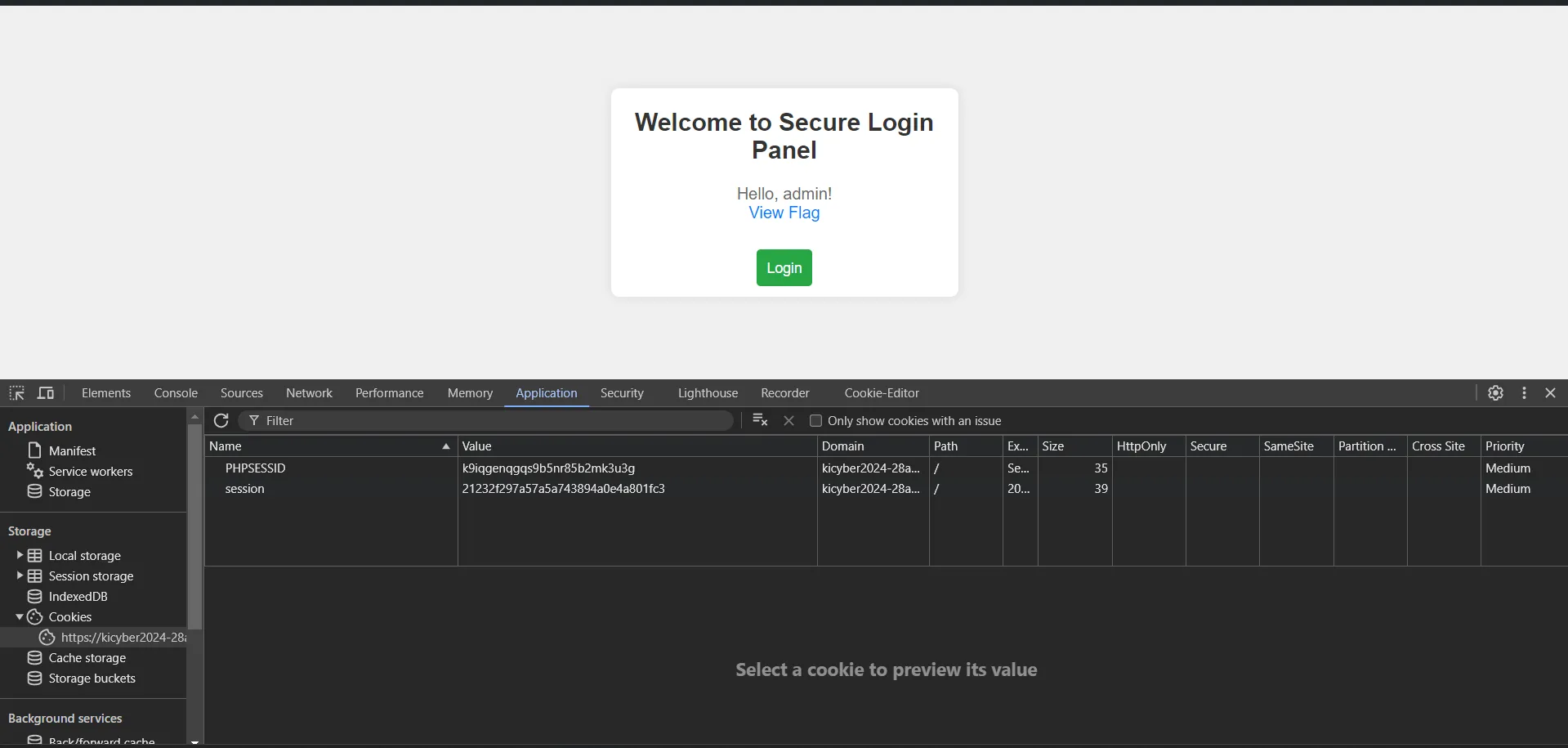
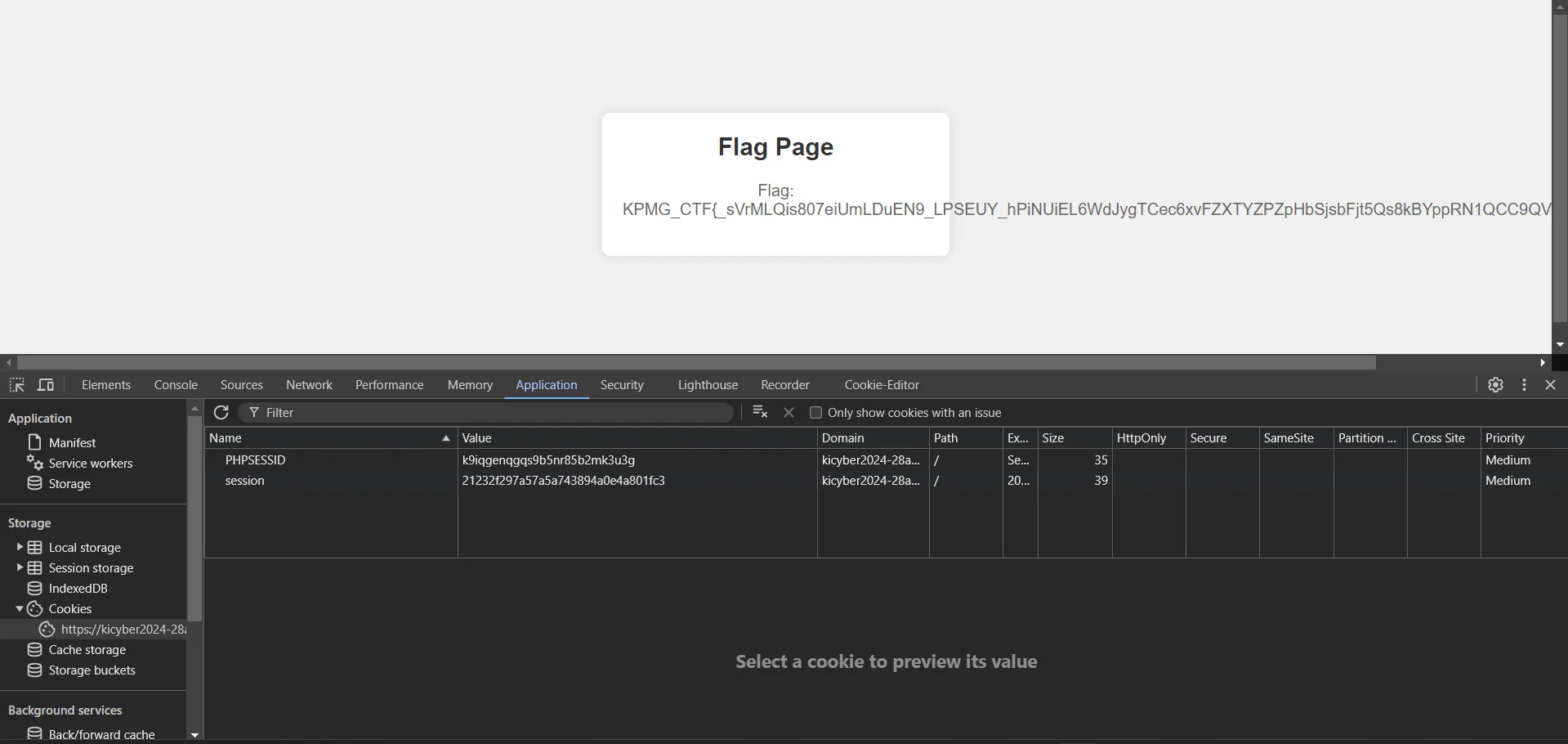
And we got the Flag. 🫡
ISC
Assassins Brotherhood - 1
- As per the description, we have given the URL, host, and port.
- First, I do the
http://0.cloud.chals.io 27232And from this, I know that on this port, SSH is running By showing the SSH header, I got. - After that i try to access the website,
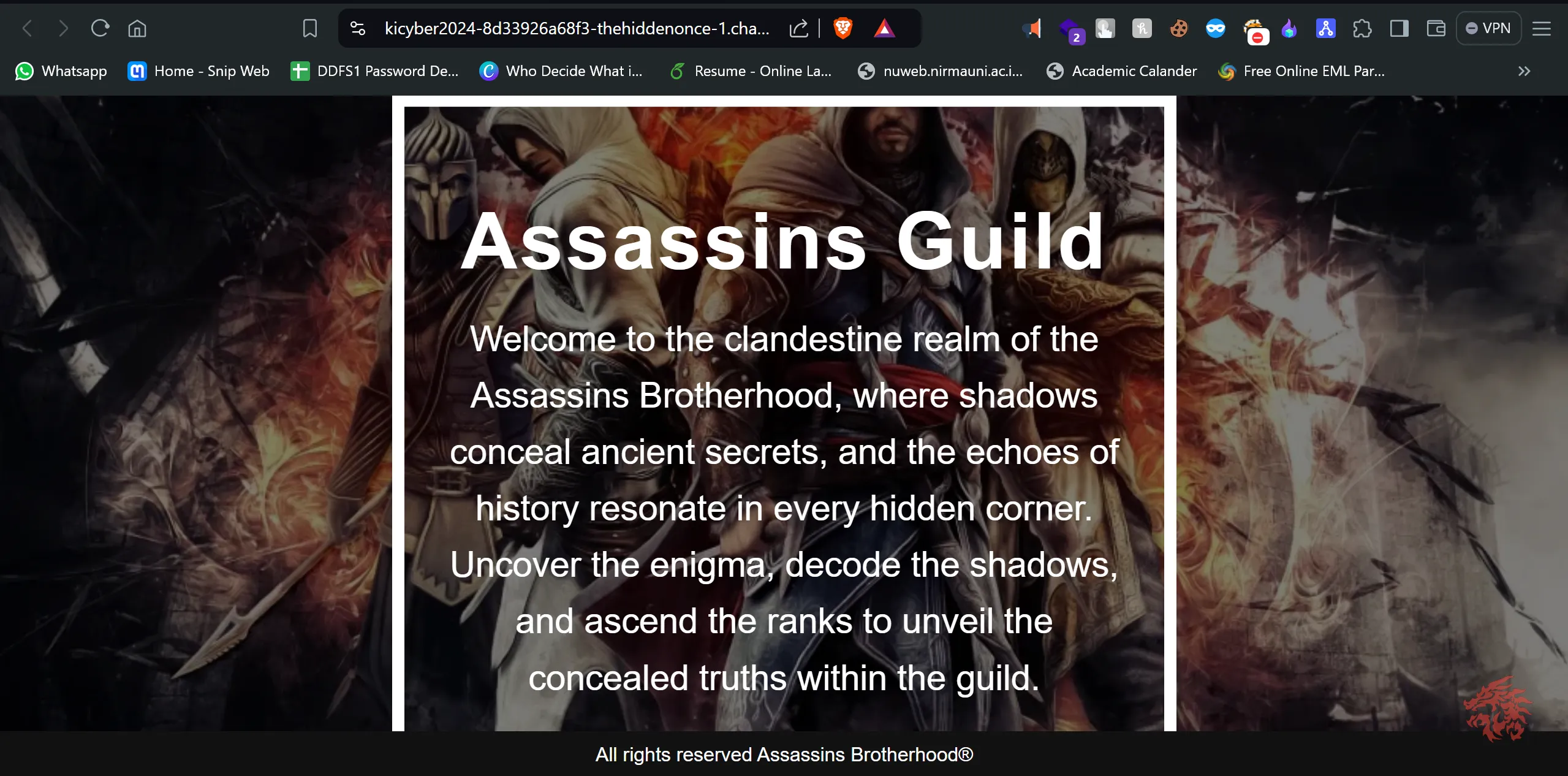
- After that, I viewed the page source, and I got this from it
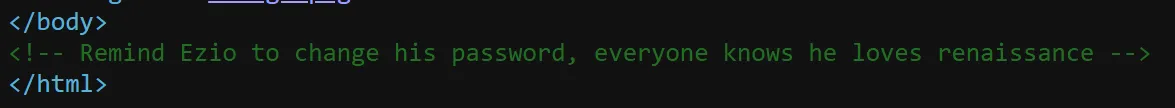
- And I said I knew that one server, SSH, was running, and this statement pointed out the username and password of the
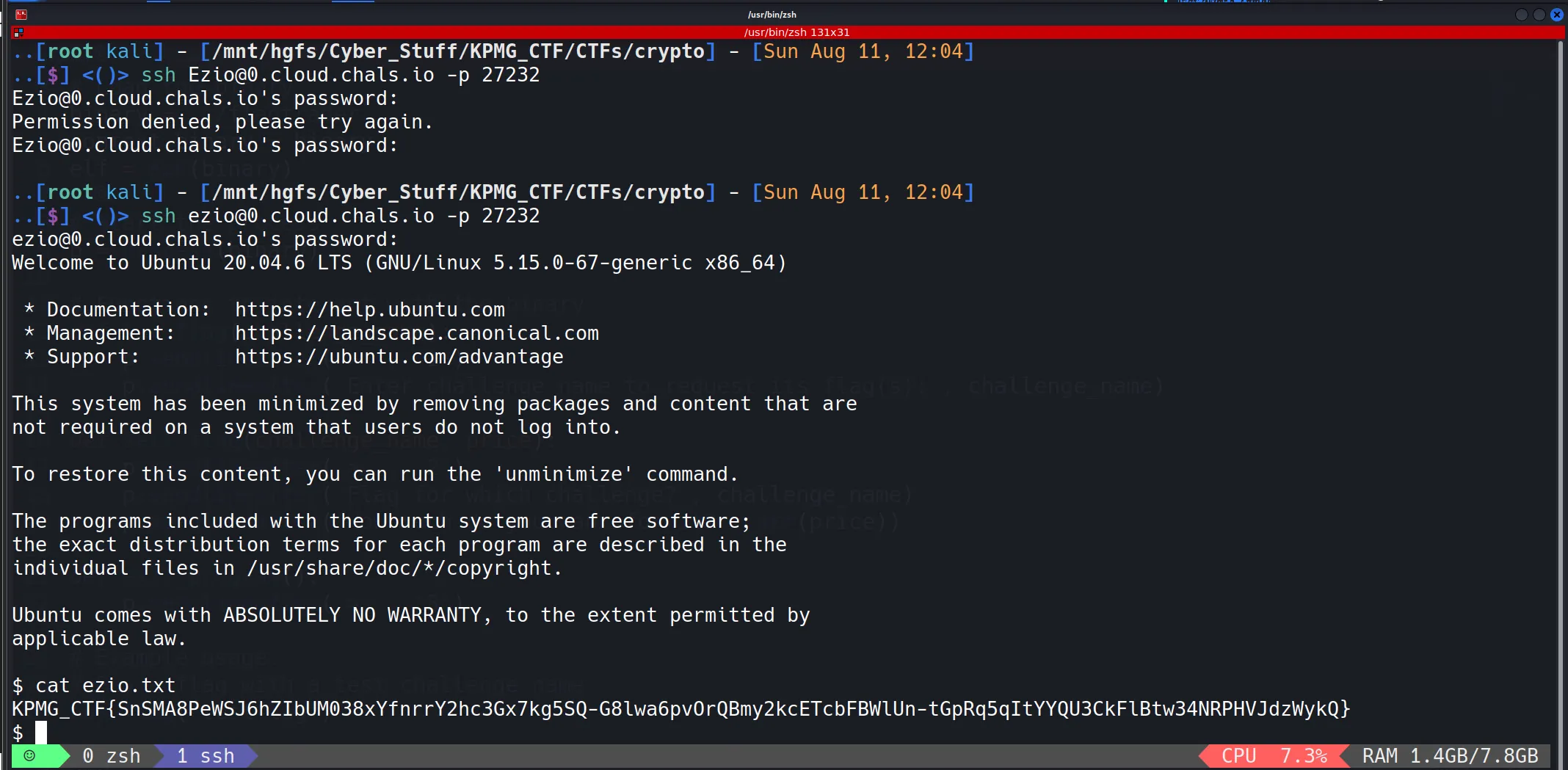
Eziouser, so i try to connect with SSH, - Connected Successfully and got flag on
ezio.txtfile, 🫠
Crypto
Micro RSA
- From this challenge i got values.txt file which contains this information,
n=124654455290240170438072831687154216330318678151127912274279675542477378324205547190448356708255017687037267403854771170485302392671467974951403923256433631043504787586559727625072674672756729381597771352105733117303538360769540765664178969569213281846028712352533347099724394655235654023223677262377960566427
e=3
c=11127001790949419009337112638492797447460274274218482444358708583659626034144288836997001734324915439994099506833199252902923750945134774986248955381033641128827831707738209340996252344658078512599270181951581644119582075332702905417250405953125
- I make a python script which performs
RSA encryption padding attack, - Reference - https://shainer.github.io/crypto/matasano/2017/10/14/rsa-padding-oracle-attack.html
from decimal import *
from tqdm import tqdm
N = Decimal(124654455290240170438072831687154216330318678151127912274279675542477378324205547190448356708255017687037267403854771170485302392671467974951403923256433631043504787586559727625072674672756729381597771352105733117303538360769540765664178969569213281846028712352533347099724394655235654023223677262377960566427)
e = Decimal(3)
c = Decimal(11127001790949419009337112638492797447460274274218482444358708583659626034144288836997001734324915439994099506833199252902923750945134774986248955381033641128827831707738209340996252344658078512599270181951581644119582075332702905417250405953125)
def int_to_ascii(m):
# Decode to ascii (from https://crypto.stackexchange.com/a/80346)
m_hex = hex(int(m))[2:-1] # Number to hex
m_ascii = "".join(
chr(int(m_hex[i : i + 2], 16)) for i in range(0, len(m_hex), 2)
) # Hex to Ascii
return m_ascii
# Find padding
getcontext().prec = 280 # Increase precision
padding = 0
for k in tqdm(range(0, 10_000)):
m = pow(k * N + c, 1 / e)
m_ascii = int_to_ascii(m)
if "pico" in m_ascii:
padding = k
break
print("Padding: %s" % padding)
# Increase precision further to get entire flag
getcontext().prec = 700
m = pow(padding * N + c, 1 / e)
m_ascii = int_to_ascii(m)
print("Flag: %s" % m_ascii.strip())
- After Running this script, I got the flag!!
KPMG_CTF{sm4ll_e_15_n07_s0_s3cur3}
Crypts Beyond The Wall
- When I tried to access the website, I got this:
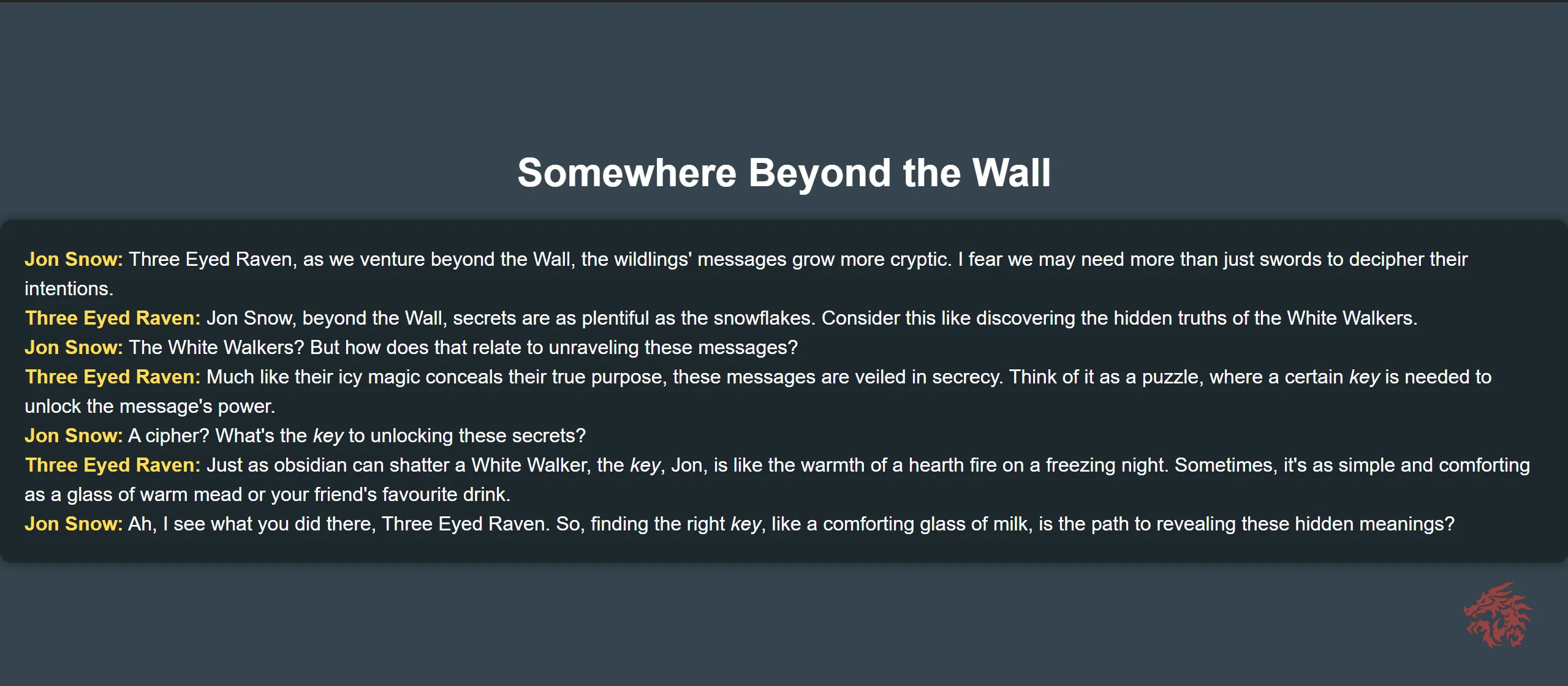
Winter is Coming: If you are a true fan of Game of Thrones, then you know this line:
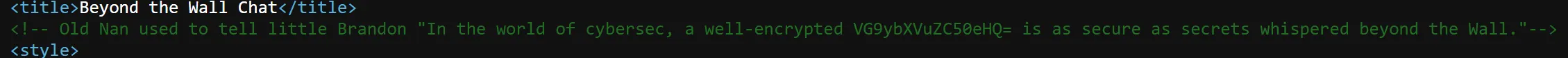
- Now I try to open the source code, and from that I get this comment:
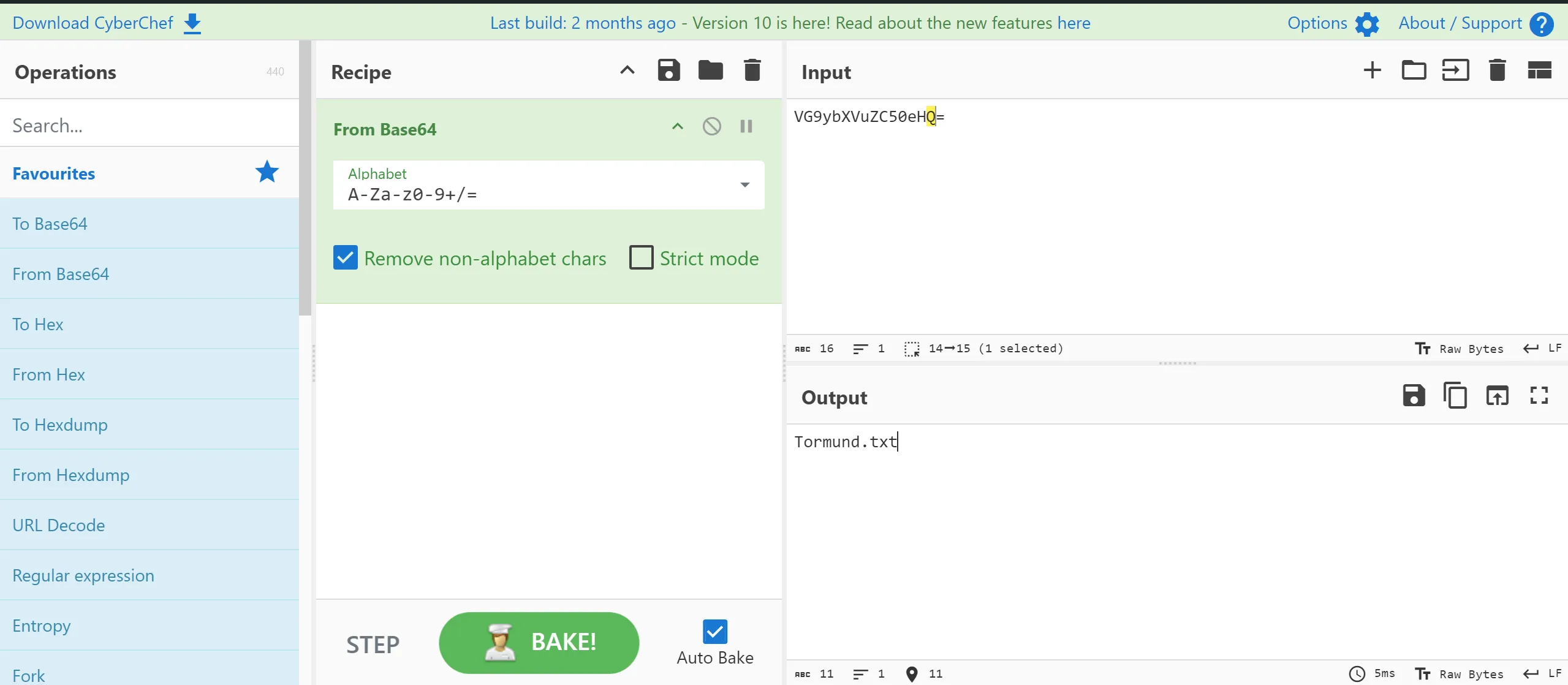
- When I tried to decode this encoded base64 string, I got ‘Tormund.txt’.
- Then I tried to access that page, and I got this:
- And from that page, I got another
BeyondTheWallsLogs.txtand a hintgiantsmikfile, which gives me,
- From this image, I got a cipher text, which I think is
vigenere cipherso I tried to decode it with the keygiantsmilk.
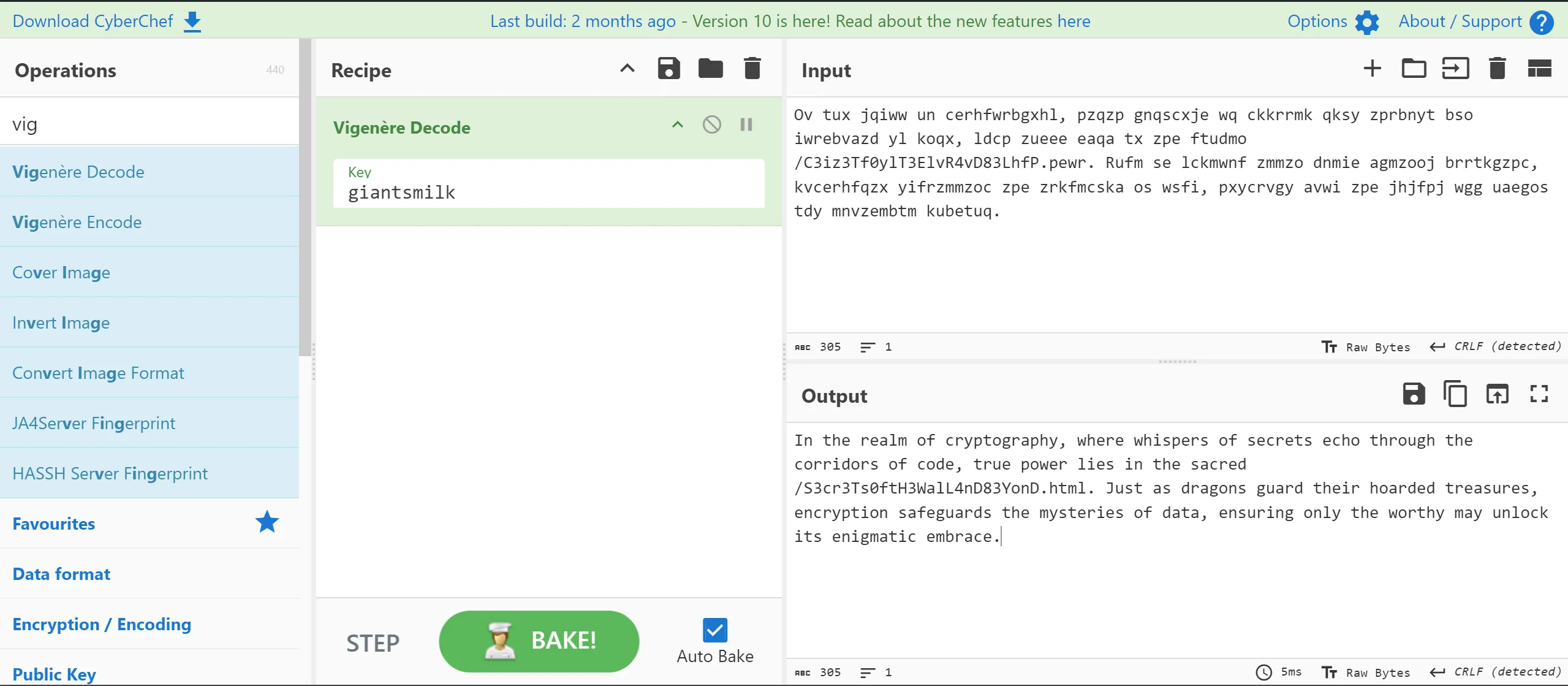
- From that, I got
/S3cr3Ts0ftH3Wa1L4nD83YonD.htmland from this file, I got the flag.
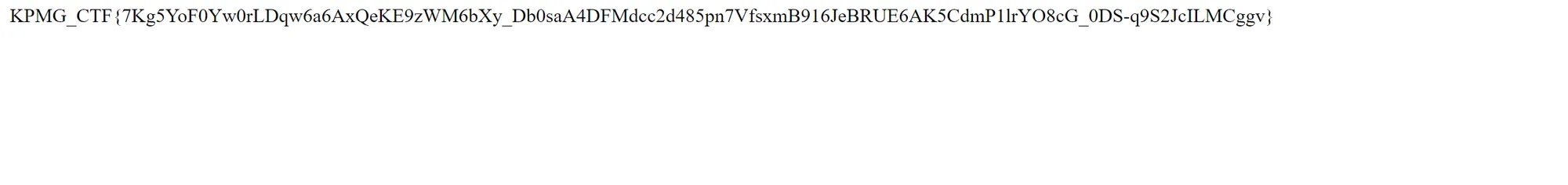
Mobile
Android CryptoQuest
- From the description, we got the apk file
mobilechall1.apk. - After decompiling the file with
jadx-guisoftware for Windows,. - After digging around in the decompiled classes and Java files, I found an example.
example.ctfchallpackage which contains the class files of the decompiled code, and from this directory, i got theMainActivityfile, which contains thehalf-flagin encoded format.
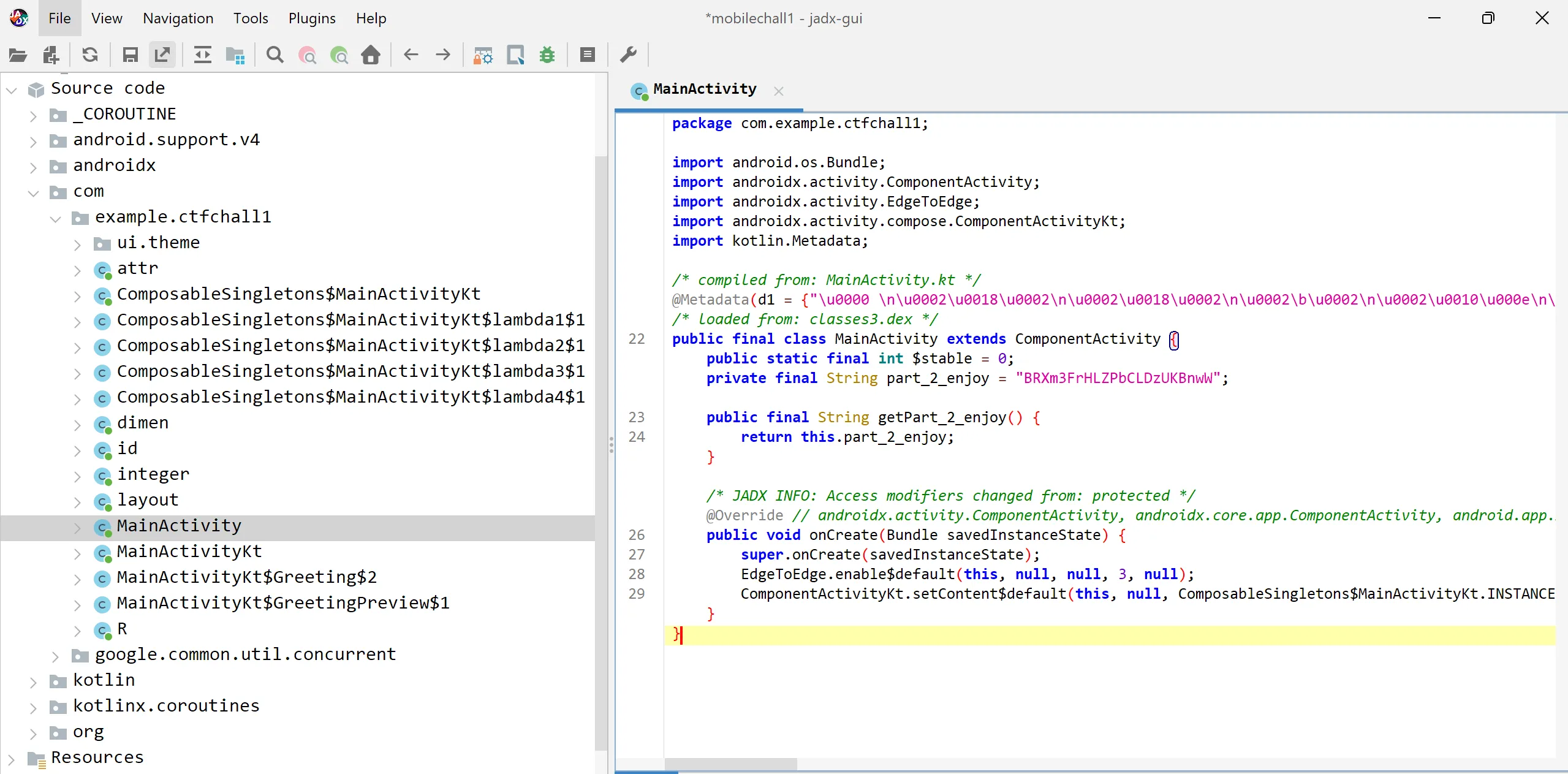
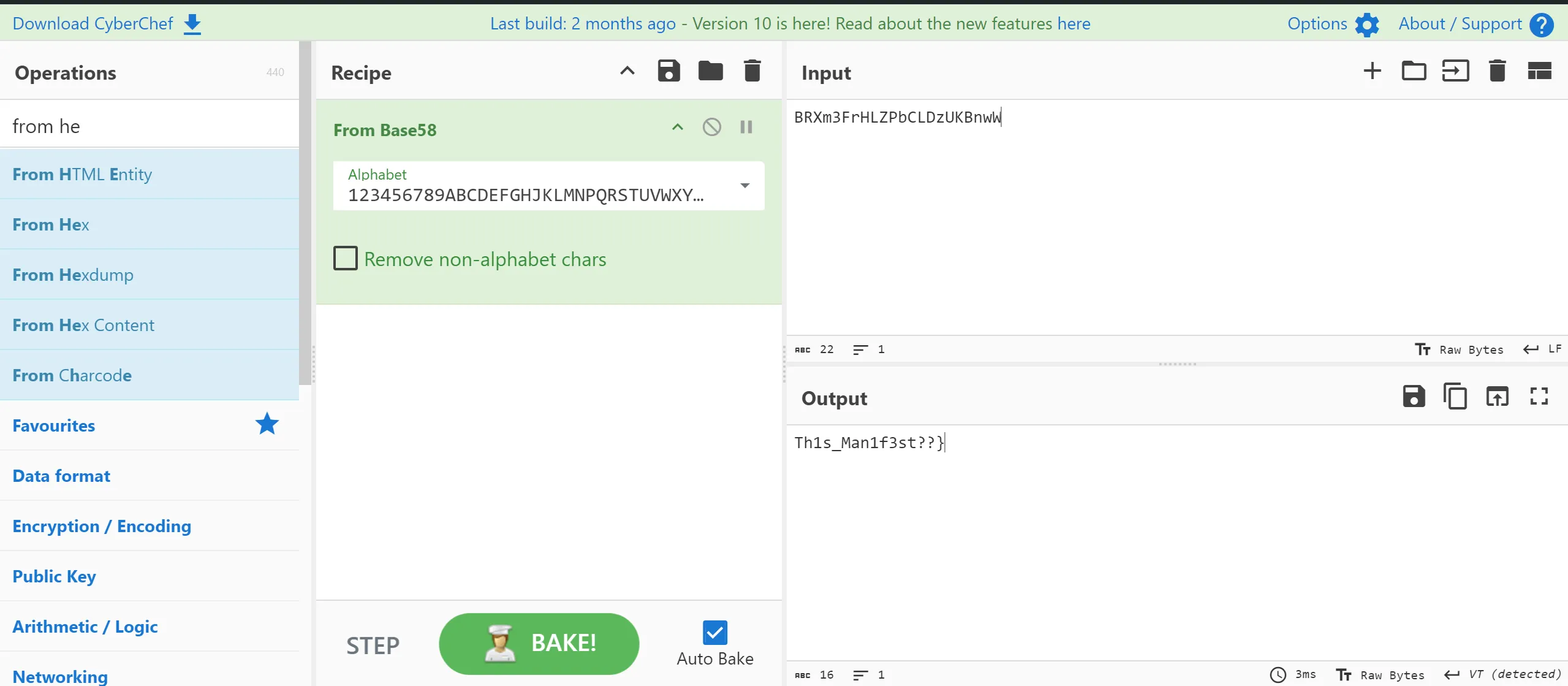
- After decoding this base85-encoded string, I got to know that this flag was pointing out something, which is
AndroidManifest.xmlfile,
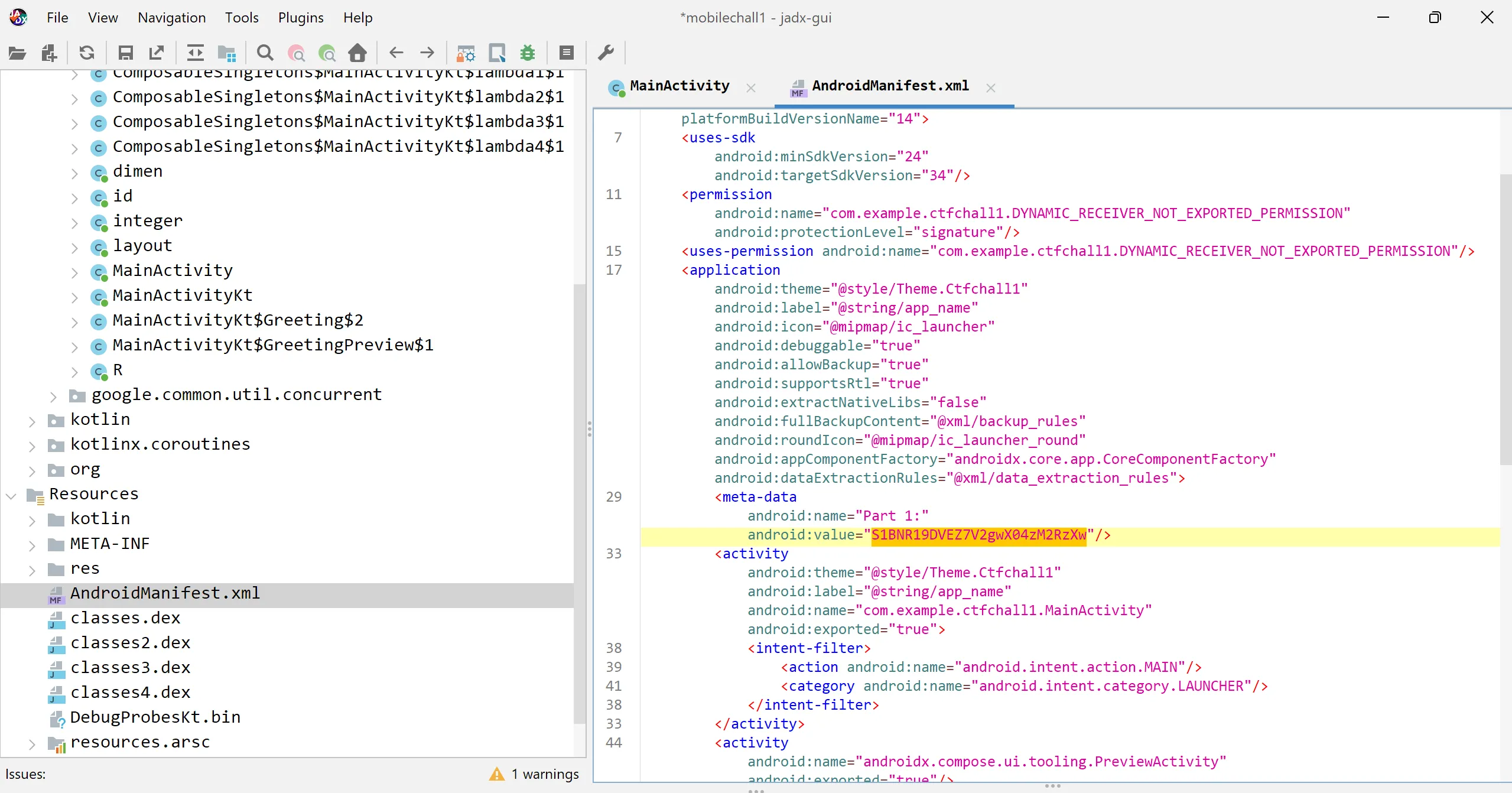
- Then check out the
AndroidManifest.xmlfile and hurray i got the another part of flag then i decode it with base64 scheme and assemble the flag,
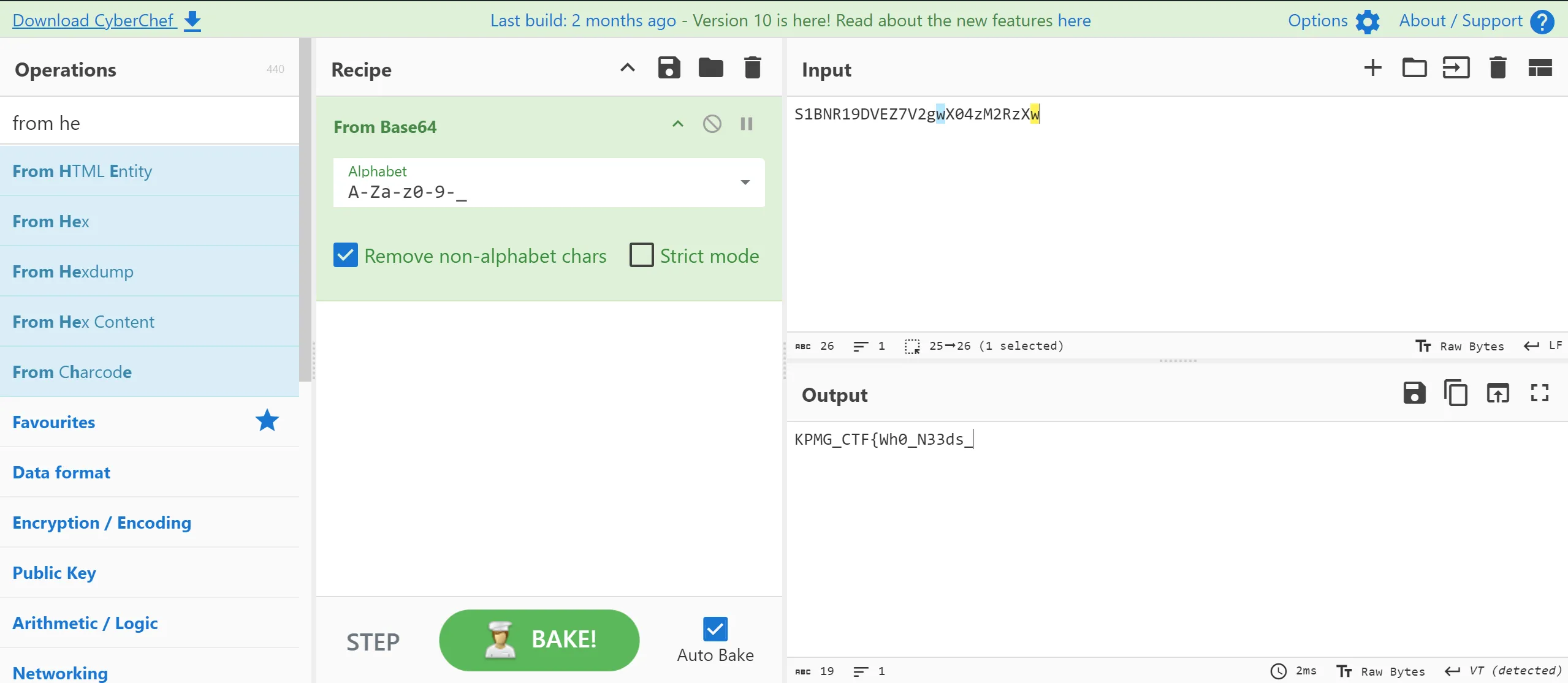
- Assembling the Flag,
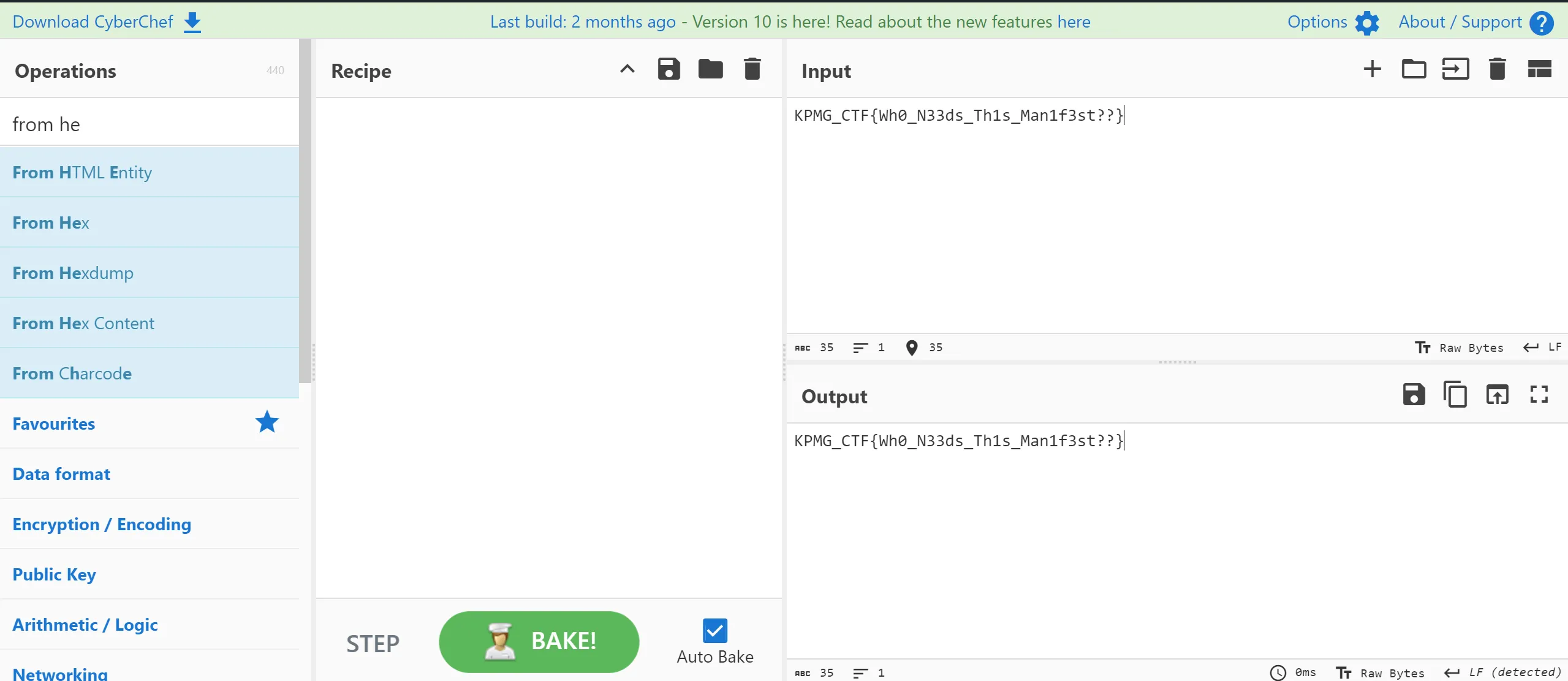
OT
Modulus bus Station
- As per decryption, I can understand that I have to use the Modbus client tool to connect with the protocol. After some searching, I found a tool named
modbus_cli.
pip install modbus-cli
- After installing it, I saw the manual for its usage, and after a while, I knew how to use it and got some raw data bytes in hex.
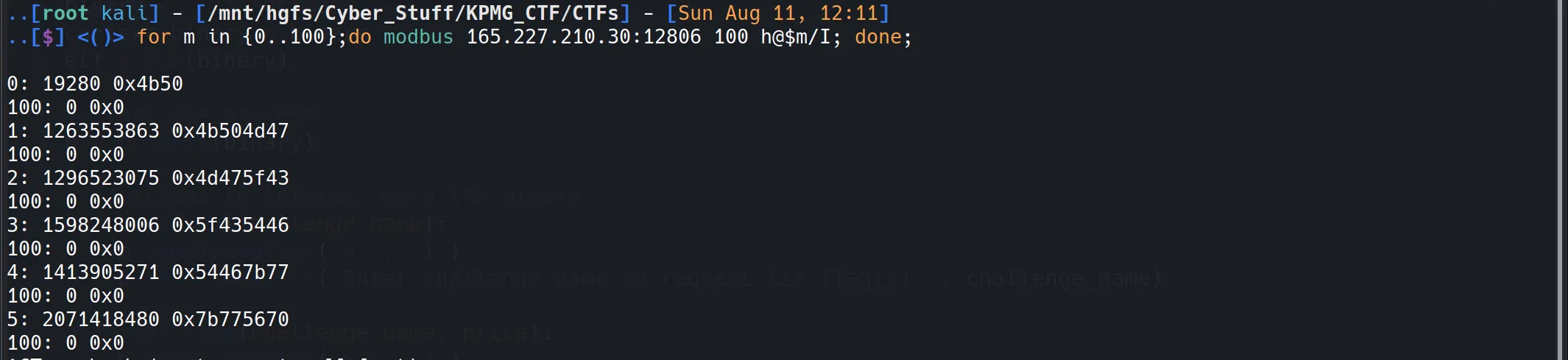
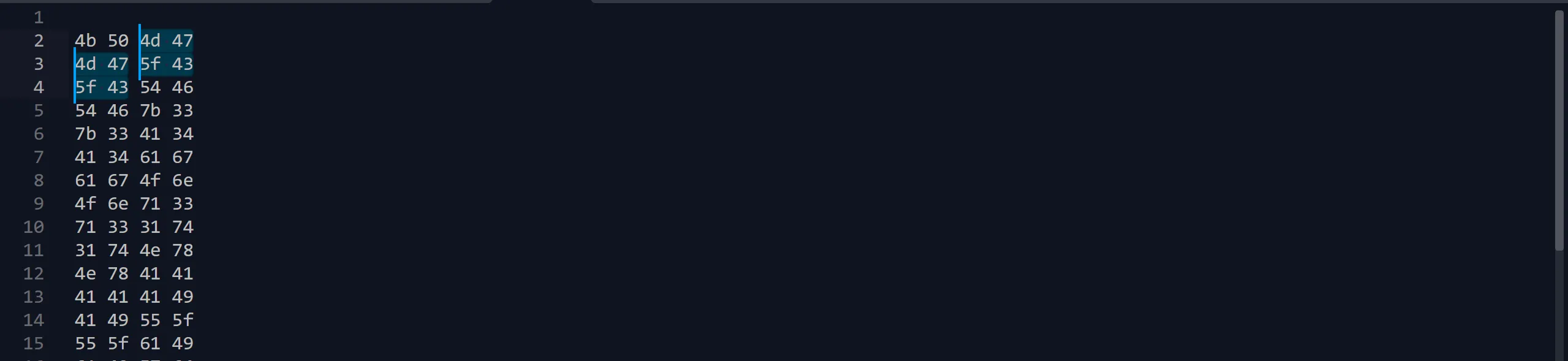
- I cleaned up the data in these 3 steps:
- First, grep all the hex data and remove other stuff in a file.
- Then I convert each bytes hex to ASCII character equivalent.
- Then remove all the duplicate bytes from the data.
- Then combine all the data.
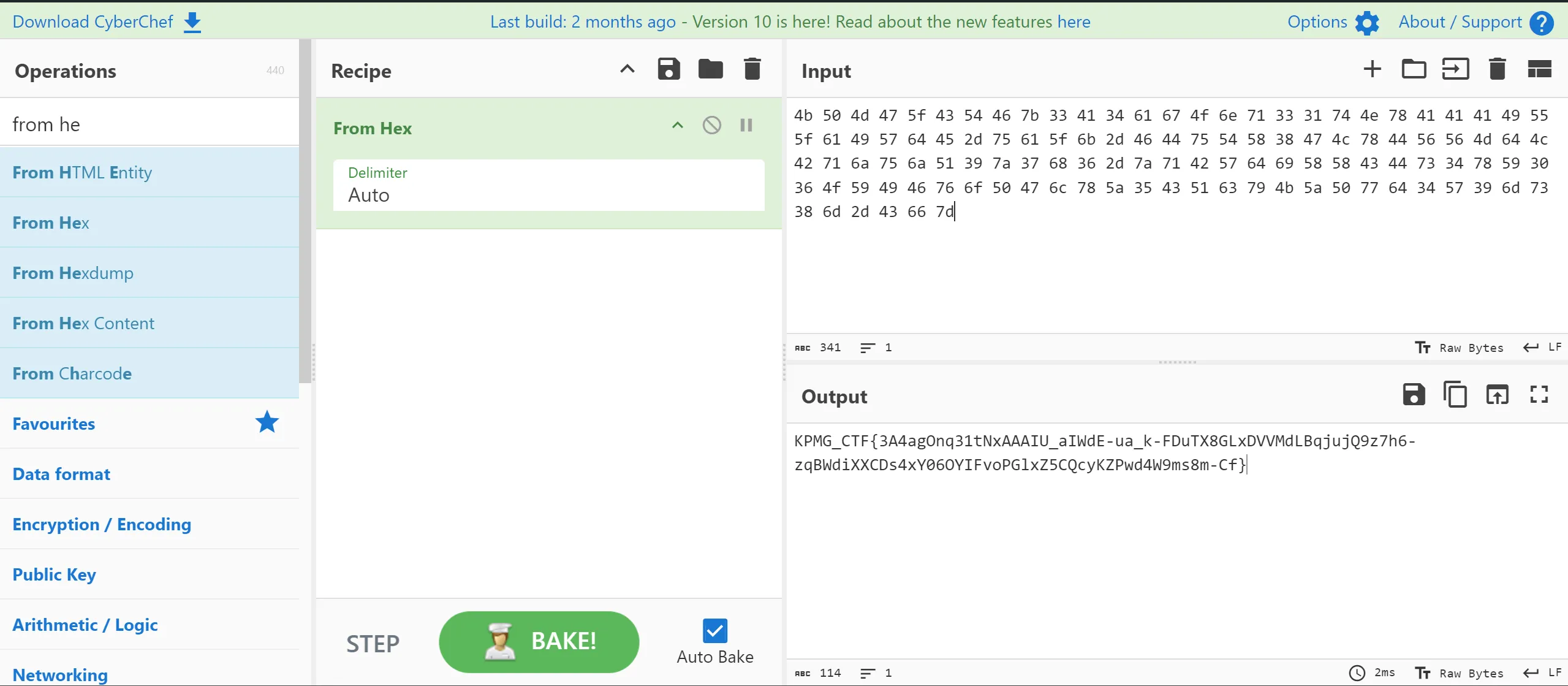
- Then i try to decode it from CyberChef and i got the flag, 🫠
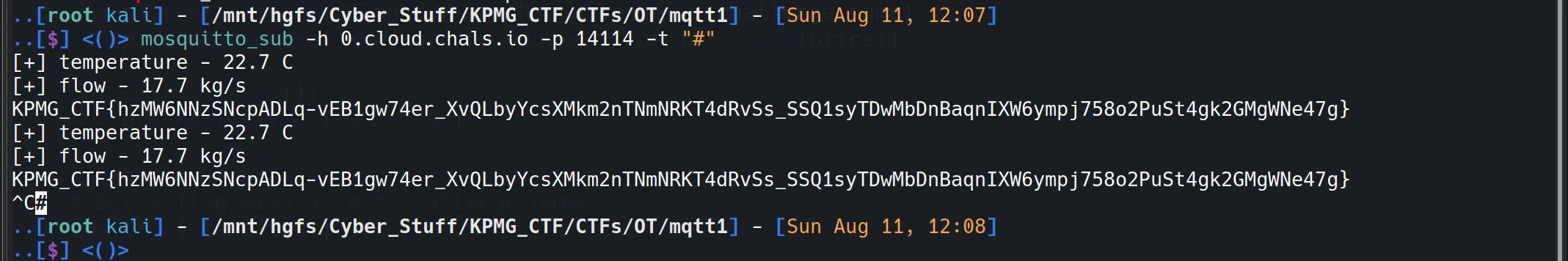
mqtt - Master Qutie TT - P1
- As per the decryption given, we have to access the HVAC system and try to subscribe to all the subtopics.
- So first of all, I don’t know how to access the mqtt service, so I just did a Google search and got the treasure.
1883: Pentesting MQTT (Mosquitto)- From this, I know which tool to use and how to use it, so I use
Mosquito.
apt-get install mosquitto mosquitto-clients # Install the tool
- From Blog, I used the -t option for subscribing to all the subtopics, and from that, I got the flag. 🕺